Co-managed SIEM
- Modular: Takeover of individual roles through to complete SIEM operation.
- Flexible: We adapt flexibly to your needs and processes.
- Hybrid: Provision of services from our Cyber Defense Center or at your site.
Our co-managed SIEM approach adapts flexibly to your needs!
Our co-managed SIEM approach at a glance
With the SECUINFRA co-managed SIEM approach, all SIEM components and data always remain with you. The detection mechanisms (SIEM use cases) are also your intellectual property and belong to you. This enables easy adjustments to SIEM operation at any time. Depending on the task at hand, our cyber defense experts will either be located directly on your premises or access your SIEM via a secure connection.
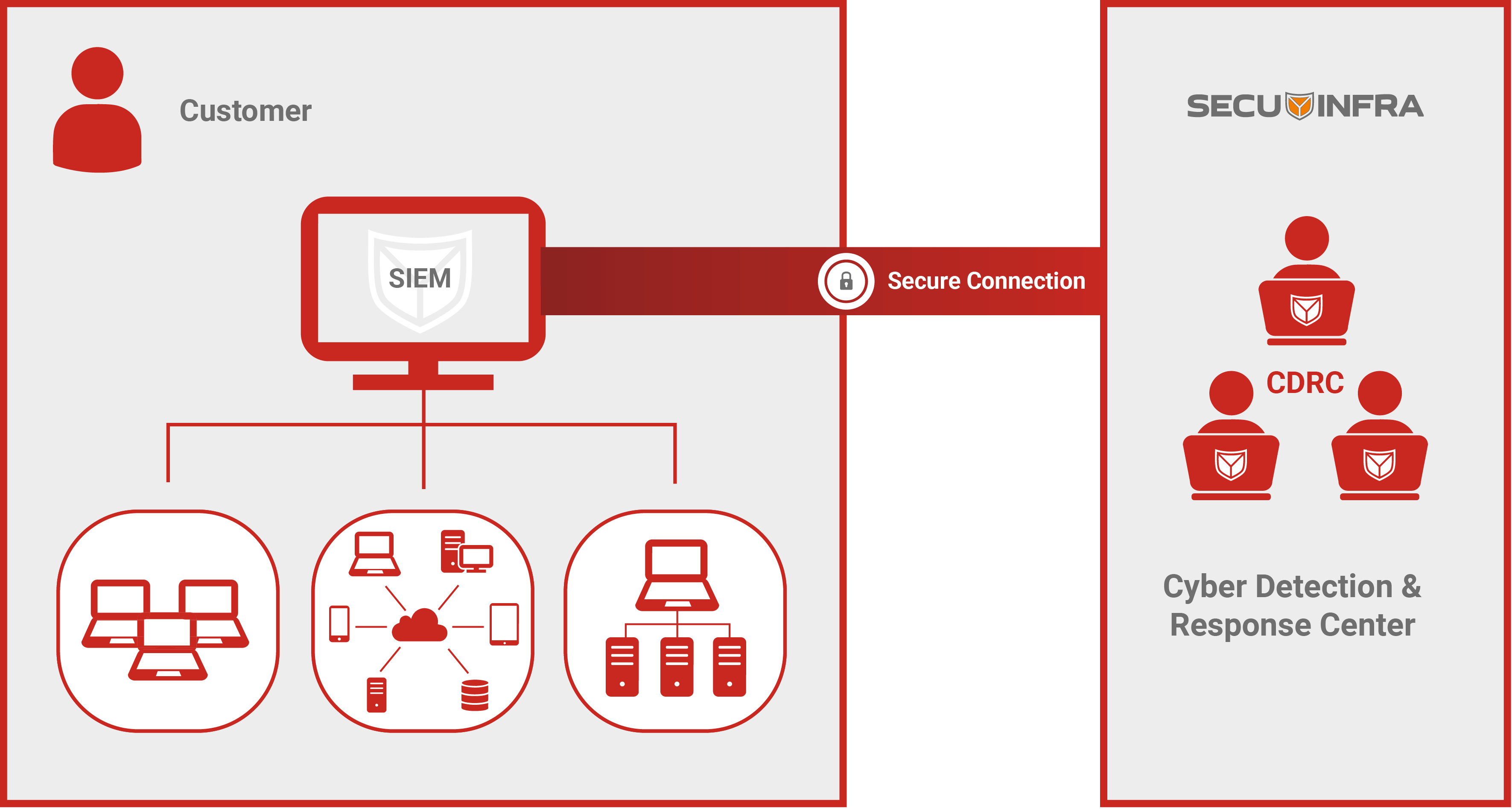
Our co-managed SIEM approach helps you avoid dependencies and hidden costs!
Norbert Nitsche, Managing Cyber Defense Consultant
Our awards in the area of SIEM Consulting

Best SIEM consulting/service company in Europe

Market leader in Security Information Event Management (SIEM)

Leading provider of SIEM consulting services in Germany

TOP 10 SIEM consulting/service companies in Europe
The 3 most important FAQs about co-managed SIEM
A co-managed security information and event management (co-managed SIEM) service portfolio ideally has a modular structure and can be flexibly adapted to almost any customer requirement. At SECUINFRA, you as the customer decide which competencies you want to build up in-house and which services you want to have managed externally. A co-managed SIEM approach is therefore perfect for companies that do not want to outsource all SIEM services, but only selected ones.
A partially – or fully – externally managed SIEM offers numerous advantages, such as
- Support from experienced cyber defense analysts in monitoring and evaluating alerts and responding appropriately to actual threats.
- Continuous network monitoring by cyber defense experts, 24/7 if required.
- Flexible use of the IT security budget through an externally managed SIEM.
From the assumption of individual roles to the complete operation of a SIEM, SECUINFRA’s co-managed SIEM approach can be specifically adapted to the needs and processes of your company:
- The hybrid offering enables services to be provided either on-site or remotely from one of the SECUINFRA Cyber Defense Centers in Germany.
- Data protection is guaranteed at all times. The data does not leave your company and is accessed exclusively from Germany.
- The SECUINFRA experts have successfully completed numerous projects in the field of SIEM consulting and services, bringing extensive specialist knowledge to the services offered.
Overview of our co-managed SIEM services
Different roles with different skills are required for SIEM operation. With our hybrid, modular and flexible co-managed SIEM approach, you decide which competencies you want to build up in-house and which services you want to buy from us. Together we ensure a first-class SIEM operation. From taking over individual roles to complete SIEM operations, we adapt flexibly to your needs. However you want to operate your SIEM, talk to us. We support you flexibly in the areas where you need our expertise, everything else remains in-house.
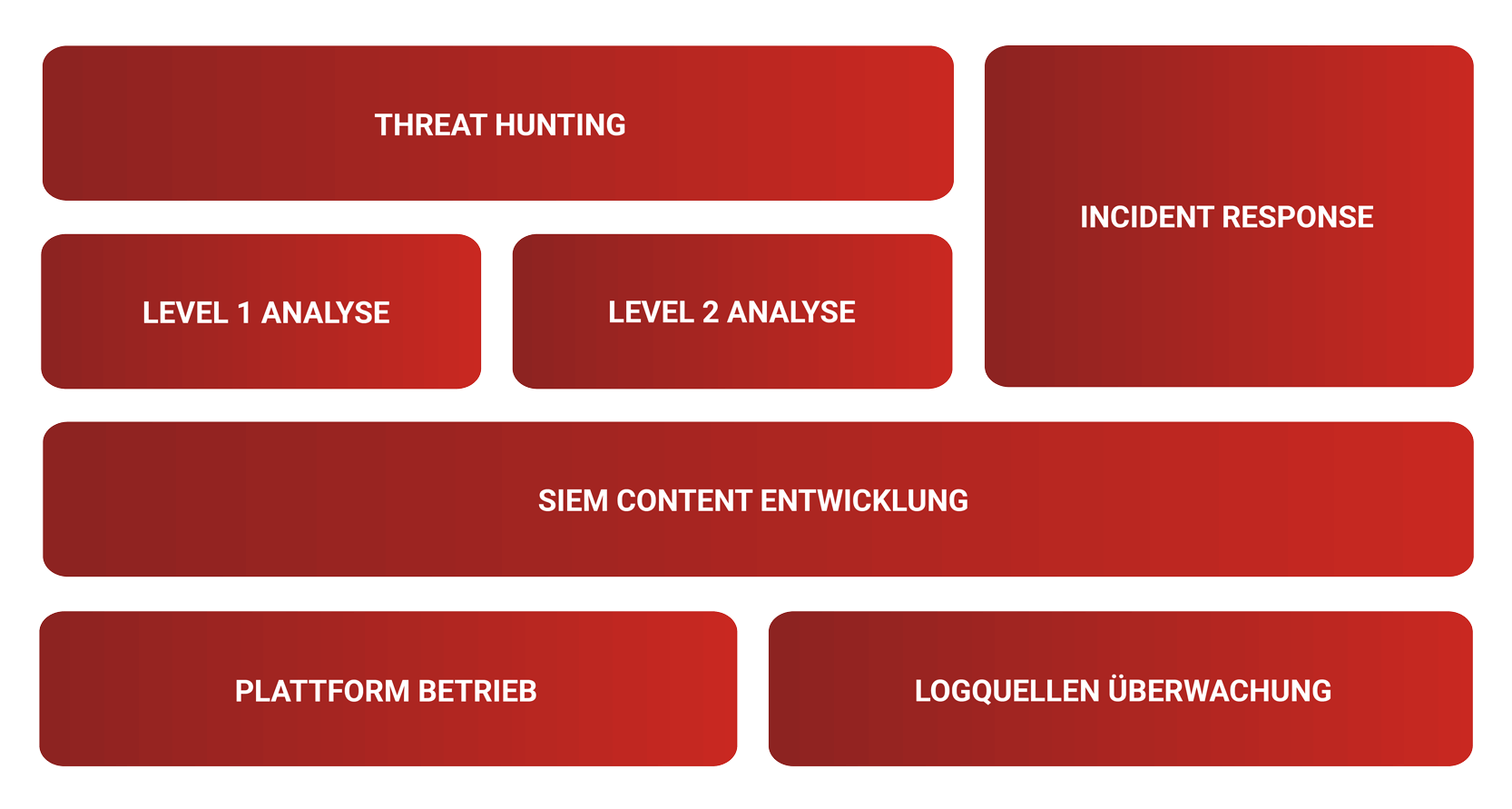
Threat Hunting
- Log data analysis due to internal or external incidents
- Log data analysis based on newly discovered IOCs and detected attacks at other SECUINFRA customers
- Clear recommendations for action for the incident response team in the event of security incidents
Level 1 Analysis
- Initial analysis of SIEM alarms
- Elimination of false positives and duplicate reports
- Escalation of relevant incidents to Level 2 analysis
Level 2 Analysis
- Detailed analysis and evaluation of relevant incidents
- Consultation with affected users and responsible parties for a clear assessment of relevant incidents
- Clear recommendations for action for the incident response team in the event of security incidents
Incident Response Support
- Implementation of compromise assessments to identify compromised IT systems
- Carrying out forensic analyses to clarify the course of the crime and to preserve evidence
- Support in the area of incident response to restore IT operations as quickly as possible
SIEM Content Development
- Development, maintenance and continuous optimization of end-to-end SIEM use cases
- Development, maintenance and continuous optimization of further SIEM content
- Development, maintenance and continuous optimization of connections to external systems
SIEM platform operation
- Ensuring smooth SIEM operation
- Constant monitoring of the availability and utilization of all SIEM components
- Continuous updating of all SIEM components
Log sources monitoring
- Ensuring the quality and availability of connected log data
- Constant monitoring of the availability and quality of connected log data
- Carrying out necessary updates in the event of changes to the log sources
Co-managed SIEM - Level 1 and Level 2 analysis
As part of security monitoring, the SECUINFRA cyber defense experts not only carry out a long-term analysis of IT security incidents, but also precisely qualify the incidents and provide suggestions for countermeasures.
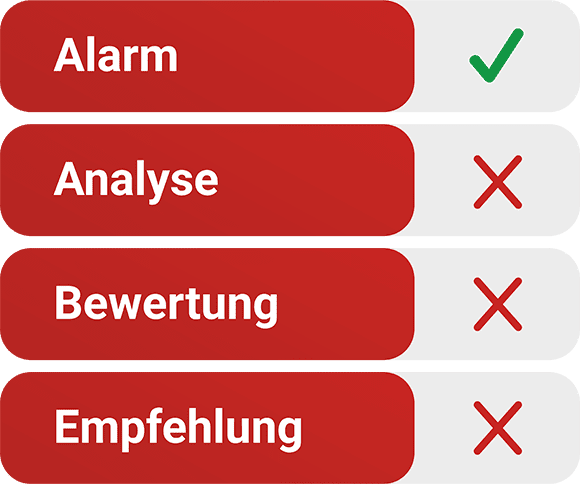
A SIEM product only sounds the alarm
Regardless of which SIEM product you use, you will receive lots of more or less qualified SIEM alerts. These must first be analyzed and evaluated by cyber defense experts in order to assess the impact on your company’s security and initiate countermeasures.
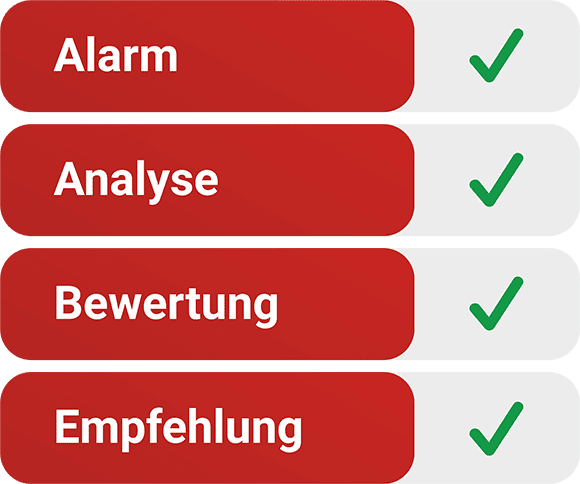
SECUINFRA Co-Managed SIEM can do more!
Our cyber defense experts always maintain an overview of the current threat situation and continuously analyze anomalies (SIEM alerts). Security breaches are escalated to the Incident Response Team, including an assessment and clear recommendations for countermeasures.
Co-Managed SIEM - SIEM Content Development
SECUINFRA has continuously invested in SIEM content development since 2010 and has developed unprecedented concepts, methods and techniques.
From our “Status Based SIEM” approach, which enables SECUINFRA customers to keep track of active cyberattacks and compliance violations, to an “Application Security Cockpit” for monitoring critical applications, to our constantly growing “End-to-End SIEM Use-Case Library”, SECUINFRA has created unique SIEM content worldwide.
In addition to their own experience, our SIEM content developers draw on the concepts, methods and techniques developed by SECUINFRA on a daily basis and continuously develop them further.
The SIEM use case designer takes your SIEM requirements and checks whether and how your requirements can be implemented. Furthermore, he calculates the effort and coordinates the implementation in the areas of log policy development, connector development and use case development. Our SIEM use case designers can draw on years of experience in the field of SIEM and can also support you in defining your requirements.
If the log data is available in the SIEM in the appropriate quality, our SIEM expert brings “intelligence” to the SIEM. To this end, he defines and implements the algorithms that are to be used to detect irregularities. He uses our internal end-to-end use case database for this. If we do not receive any deviating strict specifications for the development methodology or naming convention, we use our SIEM use case framework.
Our Connector Developer is responsible for connecting log sources to the SIEM. If log sources are not supported by default, we will develop appropriate connectors for you. The development of these connectors requires specialist knowledge and, above all, a great deal of experience. As some of our SIEM experts deal with the development of connectors on an almost daily basis, they are able to deliver results quickly and efficiently.
In the Log Policy Development area, we support you in defining the right log policy for each log source type. These form the basis of every SIEM. Irregularities can only be detected if the necessary data is generated with the correct content. We can draw on several years of experience from numerous projects.
Co-managed SIEM - SIEM platform operation
The stable operation of all SIEM components is the basis for detecting security incidents.
Monitoring the availability of SIEM components
Monitoring the availability of all SIEM components helps to minimize downtimes and prevent data loss.
Monitoring the utilization of SIEM components
By monitoring capacity utilization, we analyse historical capacity developments in the network so that we can react to bottlenecks in good time.
Maintenance of all SIEM components
By maintaining all SIEM components, we ensure that they are always up to date.
Co-Managed SIEM - Log source monitoring
Security incidents can only be detected with high-quality data.
Monitoring the availability of incoming events
We monitor event availability to ensure loss-free transmission of security-relevant events from the event source to the SIEM.
Monitoring the quality of incoming events
When monitoring the quality of incoming events, we focus on ensuring that incoming security-relevant events can be processed correctly by the SIEM.
Maintenance of data connections
That's why SECUINFRA!
Your data remains with you at all times and never leaves your company. Your data is accessed exclusively from Germany. You have full control and visibility of your data at all times.
Our knowledge comes from practical experience and is based on many years of experience in operating our own Cyber Defense Center as well as setting up and operating numerous SIEM, SOC, CERT and Cyber Defense Centers for well-known customers.
More informative blog posts and professional articles
References in the area of co-managed SIEM
- SECURITY
SECUINFRA does not name clients or references publicly! Our customers’ desire for confidentiality always takes precedence over SECUINFRA’s marketing interests. - SUCCESS THROUGH RECOMMENDATION
We have been focused on SIEM Consulting since 2010 and have gained more SIEM Consulting experience than any other company in Europe in more than 150 customer projects over 28,000 SIEM Consulting days. Almost all customers have become aware of SECUINFRA through recommendation and have in turn recommended us to others. - REFERENCE ON REQUEST
In case of legitimate interest, we will put you in touch with suitable reference customers.
Here you can get in touch with us!
Contact form end of page
Contact form at the bottom of the page
"*" indicates required fields
Our portfolio
©2024 SECUINFRA GmbH. All rights reserved.









