Inhalt
When implementing a SIEM Solution one of the biggest challenges for companies is to answer the question which threats should be detected and how to prioritize those threats.
This question is so challenging because a serious answer requires a solid knowledge of common attack patterns, their functionality and the implications on the business. Companies that are new to cyber security lack the specific knowledge and expertise to analyze common attack patterns, their functionality and the implications to their business.
One, if not the most, common answer to the question which attack patterns are frequent is MITRE ATT&CK. This matrix describes the goals of attackers (“tactics”) and associated actions (“techniques”) to achieve those goals. MITRE ATT&CK has made its way to be the quasi-industry standard when it comes to describing attack patterns.
However, practically speaking, this answer isn’t that helpful either because the MITRE ATT&CK matrix, at this point, contains about 600 active techniques.
This might technically solve the initial problem of not knowing which attack patterns are out there, but the amount of information provided is so overwhelming that the outcome stays the same – investing months of work to read through hundreds of techniques is hardly an attractive solution.
Companies new to cyber security still face the challenge of not having a tool at their hands to efficiently decide what to detect with their SIEM.
How can MITRE ATT&CK be used as a source for strategic threat intelligence?
We want to help companies with exactly this problem. Our tool “attack_rate” parses the Threat Intelligence data provided by MITRE ATT&CK into an easily accessible and understandable format. It parses the MITRE ATT&CK database which is provided in the STIX 2 format through the mitre/cti (cti = cyber threat intelligence) repository on GitHub. The exact functionality of the tool will be discussed in another more technical blog post.
Our tool will write its output into a CSV file. If you don’t want to go through the hassle of setting up a ruby environment locally you can simply download the current CSV or XLSX file from our GitHub repository.
The term “Threat Intelligence” is used somewhat ambiguous in cyber security. In the context of SIEM the thought is compulsory associated with it is often the use of threat intelligence feeds. When we say threat intelligence in this context, we mean the usage of such data as a strategic tool.
What should be the goal of a well implemented SIEM?
First of all, we should come to a common understanding of what should be achieved by its initial implementation. The following objectives can usually be agreed upon:
- Attacks should be detected before they can have a critical impact
- Especially in the beginning the cost benefit ratio should be as good as possible
- Alerts should be reliable, false positives should be avoided whenever possible
Two Third of the relevant information can automatically be gathered by using attack_rate. The last step still requires a manual analysis, but the overall effort can still be drastically reduced by limiting the scope of the manual evaluation which results in days of work instead of months.
Which MITRE ATT&CK techniques should be in and out of scope?
First of all, we must look at the tactics themselves as there are some that can be excluded categorically because a detection by a SIEM system is not possible, not practical or only achievable with very low accuracy.
Fig. 1: MITRE ATT&CK matrix in version 10 (Click image to view original size)
- The tactics Reconnaissance and Resource Development where a part of the PRE Matrix of MITRE ATT&CK which described steps attackers would execute in PREparation of an attack. The PRE Matrix has currently been integrated into the Enterprise matrix. There are means by which the included techniques can be detected, for example by cyber deception use cases, but the value of such alerts is questionable at least in the beginning of a SIEM implementation.
- Techniques from the Discovery and Collection tactics are usually very hard to separate from normal user behavior or prone to a high false-positive rate. A useful implementation of such detection mechanisms is possible but the assessment has to be performed on a case by case basis which will take up a lot of time and effort.
- Techniques from the Command & Control and Exfiltration tactics are usually hard to detect with the available log sources. This dilemma is usually based upon a very low information density of typical network logs (e.g. firewall, switches, routers, etc) which results in a high false-positive rate or an inability to implement sufficient detection mechanisms. To get around this problem we generally recommend the implementation of an NDR platform like Corelight because of the higher information density and its flexibility.
- The tactic Impact contains techniques that can often be detected quiet easily, but the detection of such techniques is not too valuable as they are usually noticed by users and administrators in short time even without a SIEM.
Next Step: Prioritizing techniques by their prevalence
Now we enumerate the remaining tactics and prioritize them by their prevalence. The assumption behind this is that the most common techniques are also most likely to reoccur in your IT environment.
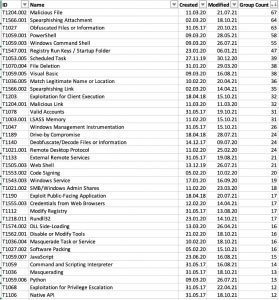
In the generated excel file the column “Groups” represents the prevalence of the technique. This information is based on the Advanced Persistent Threats (APT) that have been documented to use this technique.
This information can also be accessed through the web-based version of MITRE ATT&CK. It can be found in the Procedure Examples section of each technique and start with G (which stands for group).
Fig. 2: MITRE ATT&CK technique T1588.003: Kerberoasting (Click image to view original size)
It can be quite interesting to have a deeper look at the documentation of individual groups as the data set in MITRE ATTA&CK also contains general information about each group, their supposed background and assumed objectives.
Fig. 3: Excerpt from the list, filtered & prioritized MITRE ATT&CK techniques
Based on the prioritized list, MITRE ATT&CK techniques can be selected as the basis of SIEM use cases depending on how well they fit your environment and the available data in your SIEM. Not all MITRE ATT&CK techniques can be detected with a SIEM or at all.
Conclusion
With the approach outlined, we have created a way to prioritize the techniques described in MITRE ATT&CK without much effort – which will make the following case-by-case analysis much easier.
We see MITRE ATT&CK as an entry point to help answer the question of which detection mechanisms make sense to enter the SIEM world. This does not mean that we recommend developing a separate SIEM use case for each MITRE ATT&CK technique identified. Therefore, one should also address the questions of how the scope of use cases can be derived most meaningfully from MITRE ATT&CK techniques, whose interests are to be taken into account in the process, and which standards one can fall back on here.