SOAR Consulting
- Maximize your security operations: Efficiency and automation with SOAR
- One step ahead of cyber threats: Intelligent solutions for your cyber defense
- Transform your cyber security strategy: Faster response and resilience with SOAR
Consulting days
We provide you with a clear view – rely on a
SOAR from SECUINFRA
With our expertise, we get the best out of your SOAR out!
The successful introduction of a SOAR system (Security Orchestration, Automation and Response) requires more than just the installation of the product. The supplied functions and automations often do not offer the desired added value. Our cyber defense experts therefore support you from planning, implementation and content creation through to the operation of your SOAR. This enables them to generate added value from their SOAR and strengthen their security process after just a short time.
You decide individually which activities you would like to take advantage of from our experts. In addition to consulting services for the setup and further development of your SOAR system, we also offer operational support through our co-managed SOAR approach.

With years of experience in the areas of cyber security and incident response, we get the best out of your SOAR.
Simon Hanke, Cyber Defense Consultant
Comprehensive SOAR introduction
SOAR is more than just a product – we support you from implementation to operation.

Before purchasing a SOAR product, you should be clear about which security processes you want to automate. On this basis, they can clearly define their requirements for the SOAR system and the connection of other tools.
SECUINFRA supports you in planning and implementation.
You bring your expectations and goals to your SOAR and we supplement these with our many years of experience in the areas of SIEM consulting and incident response.
The implementation of a SOAR system is divided into several steps. In addition to the initial installation of the system, further components need to be connected. The aim is to position SOAR as a central tool in your security concept.
Alarm connection
By linking all security-relevant alarm messages from your organization to the SOAR, you receive an overview of all events. Therefore, when introducing a SOAR, all tools that generate alarm messages must be identified and connected. This includes XDR and SIEM systems as well as reports of phishing emails or possible software vulnerabilities.
Analysis tools
Various analysis tools are required to contextualize and analyse the alarm messages. These evaluate various IoCs for them, such as IP addresses and domain names, or execute suspicious files in a sandbox. We work with you to select the tools you need and connect them to your SOAR system.
Reaction tools
In order to be able to react automatically to detected threats, it is necessary to connect various tools with response options to your SOAR. This includes, for example, the connection of firewalls and web proxies for access control or EDR tools for isolating host systems.
Threat intelligence
The threat intelligence component rounds off the implementation of the SOAR system. This gives companies the opportunity to receive external information about current threats and automatically check their infrastructure for their presence.
SOAR offers great added value in the automation of various tasks. To do this, it is necessary to map the existing analysis and incident response processes within the SOAR system.
The aim is to integrate and supplement the processes already established.
As part of the SOAR introduction, we support you in the implementation and develop individual playbooks for your environment. In addition, our cyber defense experts draw on the SECUINFRA internal playbook library and offer you further options.
In addition to process automation through playbooks, it is also important to adapt the SOAR platform to the customer’s needs with dashboards and reports.
We support you in implementing the defined SOAR operating concept. We can also take on individual operating roles for you on request. The SOAR introduction by SECUINFRA is rounded off by a comprehensive know-how transfer program. In addition to product training, we primarily provide know-how on how to use your SOAR for your tasks.
Modular SOAR operation
Security orchestration, automation and response (SOAR) is a fundamental aspect of modern cyber security that enables an efficient response to cyber threats. The modular SOAR operation extends this concept by dividing it into four specific but interconnected areas: Analysis, Threat Hunting, Playbook Development and Platform Operations.
Overall, the modular SOAR operation offers a comprehensive approach to cyber security that combines both proactive and reactive strategies and the necessary technologies to deal with increasingly complex threats.

Analysis refers to the systematic investigation of cyber threats and security incidents to identify trends, patterns and vulnerabilities. This can help to assess potential threats and risks and prioritize the response.
- Detailed analysis and evaluation of relevant incidents.
- Consultation with affected users and responsible parties to clearly assess relevant incidents.
- Clear recommendations for action by the incident response team in the event of security incidents.
Threat hunting is the process of actively searching for threats that may not be detected by automated security systems. It is a proactive approach based on human analysis and creative thinking to detect and neutralize hidden threats.
- Analysis based on internal or external incidents.
- Analysis based on newly disclosed IOCs.
- Analysis based on detected attacks at other customers.
The development of playbooks involves the creation of standardized processes and procedures for dealing with security incidents. These “playbooks” are essential to ensure that the team responds effectively and consistently to threats, and often form the basis for automation in SOAR operations.
- Development and optimization of SOAR playbooks.
- Connection of further integrations and external systems.
- Setting up dashboards and reports.
Finally, platform operation refers to the actual administration and maintenance of the SOAR systems and technologies. This includes activities such as patch management, system updates and ensuring general system stability and performance.
- Ensuring the smooth operation of SOAR.
- Continuous monitoring of the availability of all SOAR components.
- Continuous updating of all SOAR components.
- Regular review of all connected integrations.
The most important FAQs from SOAR Consulting
A SOAR (Security Orchestration, Automation, and Response) system can be critical to your organization for several reasons:
- Increased efficiency: By automating routine cyber security tasks, your security team can focus on more complex threats.
- Faster response times: Enables faster detection and resolution of security incidents, minimizing potential damage.
- Improved coordination: Orchestrates the work of different security tools and teams to ensure a coordinated and effective response to threats.
- Reducing complexity: Helps to reduce the complexity of security management by standardizing and automating processes.
- Compliance and reporting: Supports regulatory compliance through the automated collection and analysis of security data and facilitates reporting.
A SOAR also supports security analysts in threat and vulnerability management, in the incident response process and in the automation of various security-relevant processes.
In short, SOAR helps you optimize your security operations, neutralize threats faster and deploy resources more efficiently, strengthening your company’s overall security posture.
We have experience with many leading SOAR providers.
In addition, SECUINFRA has strategic partnerships with Swimlane and Palo Alto Networks to get the most out of SOAR.
More and more companies want to improve their security processes with a SOAR – but this is difficult or even impossible, especially with small budgets or a lack of internal IT security experts. SECUINFRA offers you the possibility to realize your individual SOAR according to the modular principle. Our experts work with you to plan the implementation and optimization of various analysis scenarios and automations.
Various requirements must be met before a SOAR system can be introduced. This includes the option of connecting existing security tools such as XDR or SIEM systems via APIs. Furthermore, access to internal organizational systems such as Active Directory or CMDB must be available. Other sources for later contextualization such as threat intelligence databases or analysis tools round off the necessary connections.
Furthermore, their analysis processes must be defined for the subsequent automation of the alarm messages. A concrete incident response process for planning further steps also helps here. Despite the extensive automation options for various alerts, security analysts must have the necessary expertise to make a final assessment of potential threats.
SECUINFRA supports you in all necessary steps with our flexible SOAR Consulting.
SOAR systems support numerous IT security processes.
The focus here is on the automatic (pre-)analysis of various alarms from security systems such as XDR or SIEM. A SOAR system contextualizes the alarm information with data from other sources and automatically initiates protective measures if necessary.
In addition, a SOAR system offers the possibility of carrying out and evaluating threat hunting activities at regular intervals. Connections to existing systems such as EDR or NDR can be used for analysis activities. Another application of SOAR is the support of vulnerability management. The automatic checking of the products used and the subsequent assessment of their vulnerability increases their security.
The introduction of a SOAR system will strengthen your incident response process in many ways. First of all, this includes the forward-looking definition of the necessary action steps for individual threat scenarios. In addition, your incident response process becomes reproducible thanks to alarm-based playbooks, thereby improving the quality of the analysis work. In addition, a SOAR system enables the continuous and automated documentation of all activities carried out and the creation of case or summary reports.
SOAR Playbooks are diverse
We show examples of an automated analysis process with SOAR.
SOAR supports numerous processes when analysing potential phishing emails. For example, the entire process of gathering information about senders, embedded URLs or email attachments can be automated. Existing alerts can also be correlated and aggregated. Based on the information obtained, an automatic assessment of an actual threat or a false alarm can be made. In the event of an actual threat, various reactions, such as the isolation of a host or the blocking of email accounts, can be initiated automatically. At the same time, all events can be automatically documented in the form of dashboards or reports.
Depending on the configuration of the playbook, a security analyst can intervene manually in all steps or take additional measures.
Translated with DeepL.com (free version)
After an initial alarm from an XDR or SIEM system, it is the task of a security analyst to contextualise and evaluate it. A SOAR system supports this by automatically providing a wealth of information. This includes, for example, information about the affected user account and the host systems used. External information about IP addresses or domain names is also automatically recorded. In addition, correlations can be established with other alarms or IoCs found. This provides the security analyst with all the relevant information as soon as the alarm is received, enabling a rapid assessment and response.
Translated with DeepL.com (free version)
SOAR also offers numerous support options in the area of threat hunting. For example, it is possible to automatically search for suspected indicators of compromise (e.g. IP addresses, domain names, file hashes) in various log sources from EDR, NDR or SIEM systems. It is also possible to obtain external threat intelligence information on the respective IoCs.
In the event of a positive detection, various protective measures are initiated and a further check of all affected systems is initiated. In addition to the automated processes, security analysts can carry out additional activities manually via the SOAR system.
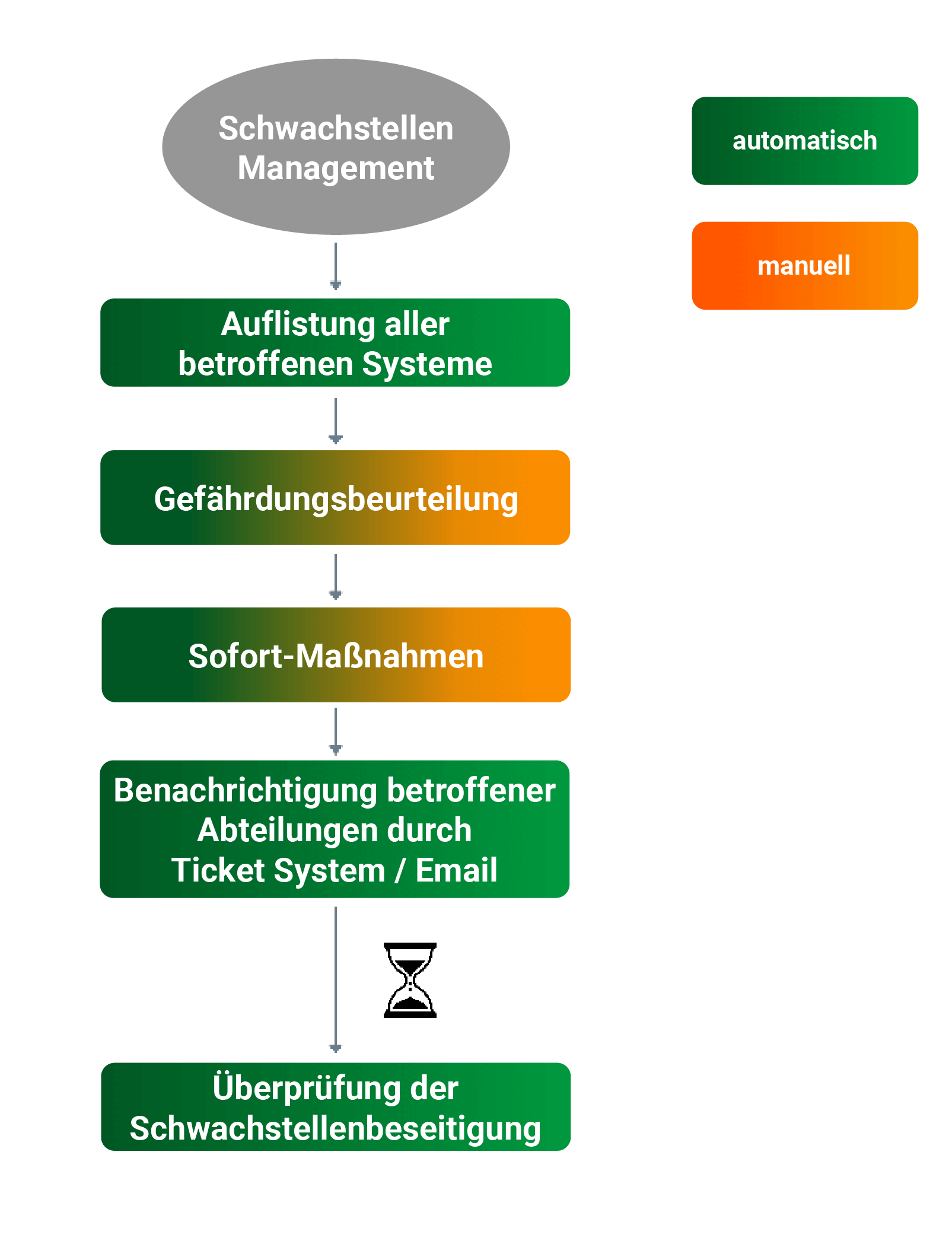
In addition to responding to alerts, SOAR systems also support preventive measures. To this end, messages from connected vulnerability scanners can be analysed and evaluated. Subsequently, initial measures to protect the affected systems can be carried out automatically or manually. It is also possible to notify the responsible parties via ticket systems or email communication.
Finally, the elimination of the vulnerabilities can be verified by rescanning the systems.
The SOAR systems support the containment of detected malware through various automatic and manual protective measures. These include, for example, the automatic isolation of host systems or the blocking of domains or IP addresses by firewalls. In addition, targeted measures on the affected systems can be controlled by the EDR solutions found. Furthermore, all IoCs found can be automatically verified and analysed for their presence on other systems within the network.
In addition, SOAR offers a guide for further analyses and protective measures and provides all relevant information via individual dashboards and reports.
That's why SECUINFRA!
The continuous support and further development of the SOAR by SECUINFRA's cyber defense experts makes it possible to react to a constantly changing threat landscape.

SECUINFRA can look back on years of experience in developing use cases and analyzing security incidents. The know-how gained flows into every new project.
We are flexible and fully customize our co-managed SOAR service to your needs and processes.

As part of our partnerships with leading manufacturers, we have a direct communication channel and can react to changes in a targeted manner.
The SOAR implementation does not stop after the initial setup. SECUINFRA provides you with long-term support in operation and further development.
More informative blog posts and technical articles!
References in the area of Managed Detection & Response (MDR)
- SECURITY
SECUINFRA does not name clients or references publicly! Our customers’ desire for discretion always takes precedence over SECUINFRA’s marketing interests. - SUCCESS BY RECOMMENDATION
We have been focusing on SIEM consulting since 2010 and have gained more experience in over 150 customer projects and 37,000 consulting days than any other company in Europe. Almost all customers have become aware of SECUINFRA through recommendations and have in turn recommended us to others. - REFERENZ AUF ANFRAGE
Bei berechtigtem Interesse stellen wir den Kontakt zu geeigneten Referenzkunden her.
Here you can get in touch with us!
Contact form end of page
Contact form at the bottom of the page
"*" indicates required fields
Our portfolio
©2024 SECUINFRA GmbH. All rights reserved.