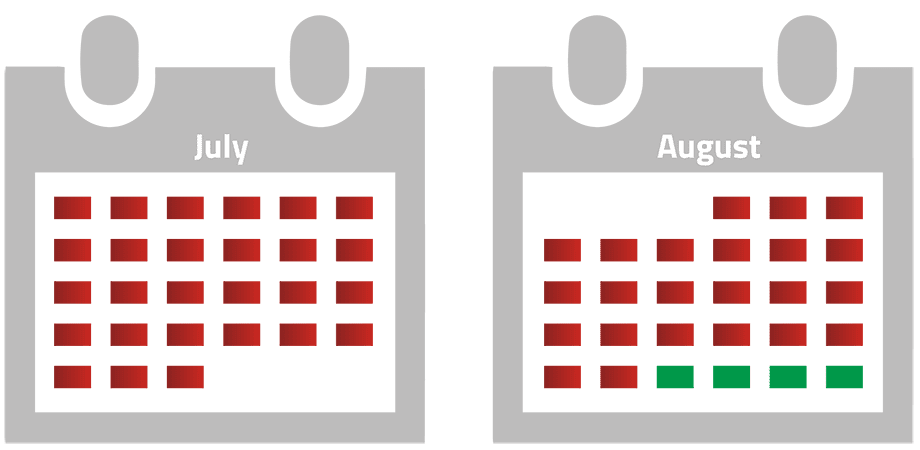
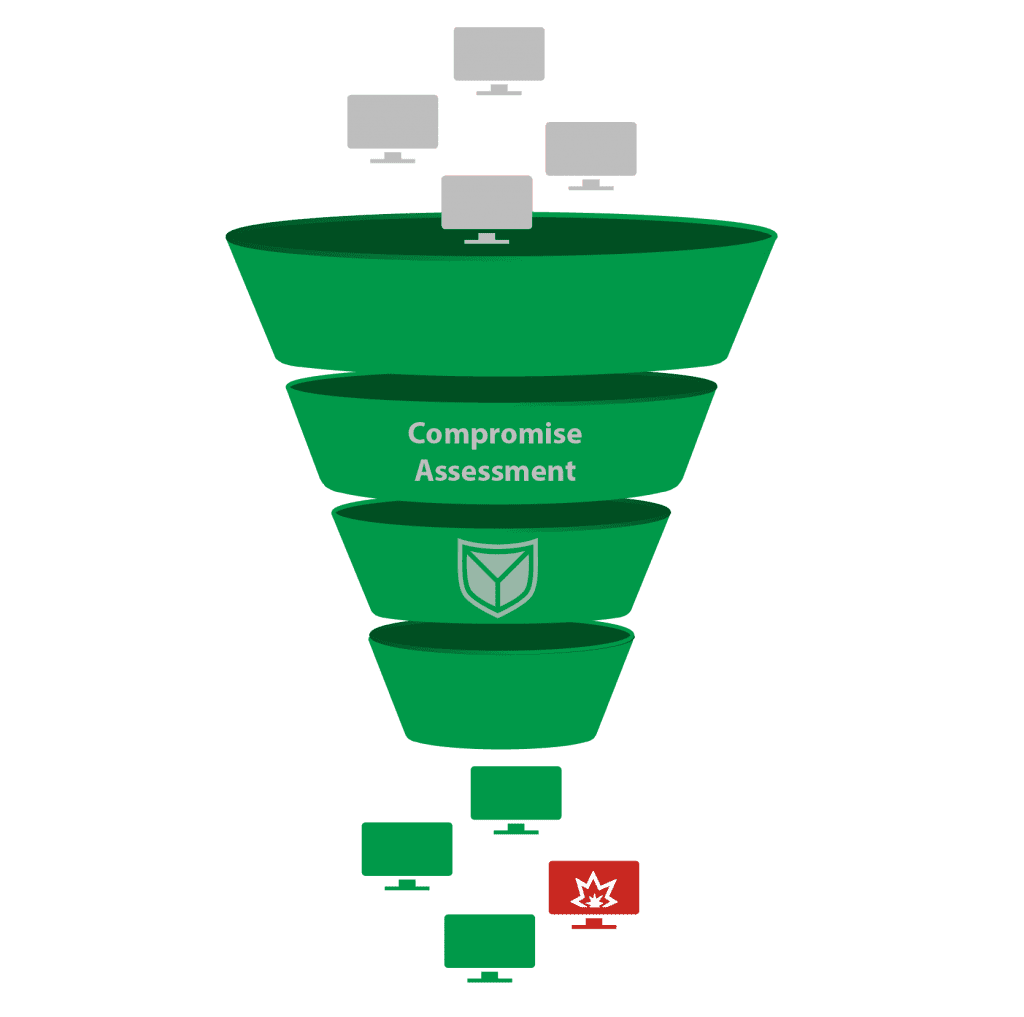
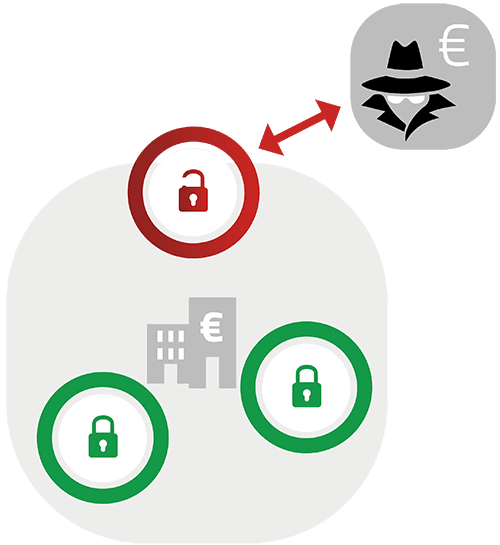
Without the regular use of forensic methods and tools to check IT systems, it takes several months before a compromise is detected, according to studies of known cyberattacks.
If a compromise goes undetected, it’s only a matter of time before an attacker gains access to your most critical systems and data, causing significant damage.