Quick help in case of emergency!
+49 30 555702 112
incident@secuinfra.com
Quick help in case of emergency!
+49 30 555702 112
incident@secuinfra.com
Incident Response
- 24/7 availability of our certified incident response experts.
- Fast help for every company. Guaranteed response times with framework agreement.
- Structured approach according to best practice & established standards.
for fast help
You have become a victim of a cyber attack? We help you quickly and efficiently, around the clock, 365 days a year!
Incident Response
During a cyber attack, professional coordination and communication is essential to contain and manage the ongoing attack. Upon request, we will work with you to develop a communication plan to optimize response times and identify responsible resources.
Regular reporting with all stakeholders throughout all phases is necessary and can be taken over by us. SECUINFRA supports you in an advisory capacity during a cyber attack and develops recommendations for action to rebuild your IT systems.
Proper coordination and communication during a cyberattack avoids major damage.
If you are affected by a cyber security incident, our trained and experienced incident managers will provide you with technical, coordination and communication support.
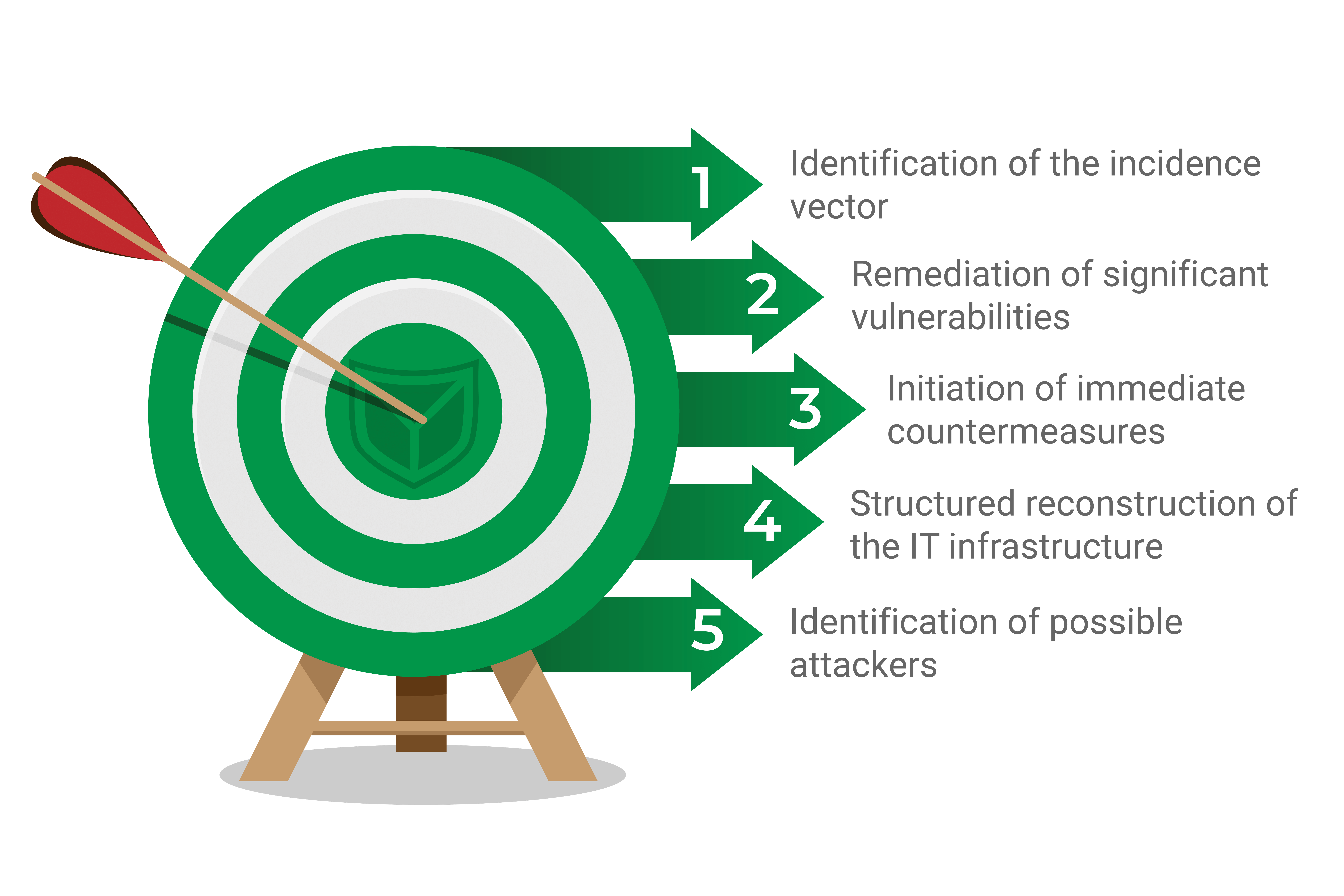
As a specialized service provider, we are happy to take over all necessary measures for detecting, analyzing and defending against the cyber attack. You can count on us. We help you detect and defend against targeted attacks by professional actors (APTs) and organized crime.
The goal of our mission is to take a holistic look at the cyberattack that has been carried out in order to analyze the perpetrators’ actions in detail.
The following insights may result from our efforts:
In the event of a cyber attack, you react efficiently, quickly and correctly with our help. This will help you avoid unnecessary costs and high damages.
Yasin Ilgar, Managing Cyber Defense Consultant
Certifications of our experts






The most important FAQ from the Incident Response area
Our professional incident response service supports your company in dealing with crisis situations related to cyber attacks and security threats. We provide fast and effective help around the clock to contain and resolve security issues. With our service, you can protect your business from major damage caused by cyber attacks and ensure that your IT infrastructure remains stable and secure.
Our experts are available around the clock to respond as quickly as possible to a security incident. In any case, we act as quickly as possible to minimize the impact of the incident on your business.
Our experts help you analyze and resolve an incident in many ways:
- We collect and analyze information about the incident to understand the extent and cause of the problem.
- If required, we also perform a Compromise Assessment on the allegedly affected systems.
- We assist you in containing the problem to prevent further damage.
- We work closely with you to quickly develop a solution to the problem and help you implement it.
- They will help you recover systems and data if necessary.
- They will advise you on improving security measures to prevent future incidents.
The requirements for an Incident Response Service depend on various factors, such as the complexity of your environment or the affected system, as well as the available resources. In general, however, your infrastructure should meet the following requirements:
- A stable, segmented and secure IT infrastructure that allows for analysis and resolution of issues.
- Detailed documentation and records that support incident analysis.
- Security measures and policies that minimize the risk of security threats.
- An adequate number of resources and skilled personnel who can assist in the analysis and resolution of issues.
- A communication strategy to ensure that all relevant stakeholders are aware of the incident and the actions being taken.
- If necessary, we support them in advance with a workshop to be able to fulfill the above requirements.
Our Incident Response Service is characterized by the following features:
- 24/7 availability: our experts are available around the clock to minimize response time and provide you with round-the-clock support.
- Highly qualified experts: our experts have extensive knowledge and experience in IT security and incident response. We are able to analyze and solve even complex problems.
- Flexibility: We are able to adapt to the specific needs and requirements of our customers and develop customized solutions.
- Transparency: We keep you informed about the progress of the analysis and resolution of the incident throughout the entire process and inform you about all relevant developments.
Our approach complies with established standards and best practices
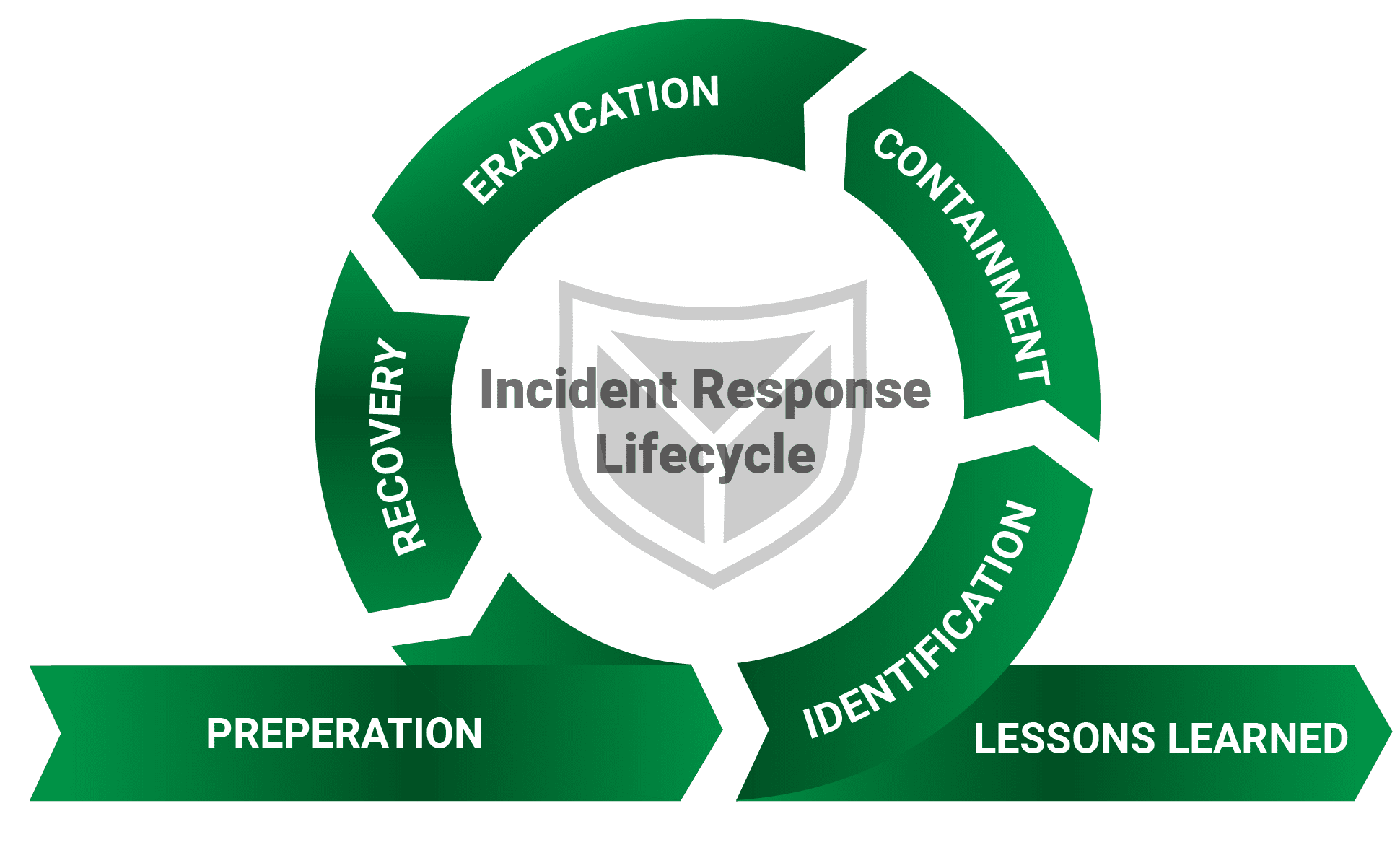
Our approach is based on the established Incident Response Plan of the SANS Institute. The SANS Incident Response Plan, or lifecycle, is divided into six main phases. Preparation of the Incident Response Plan (Preperation), Identification of the Threat (Identification), Containment of the Infection (Containment), Remediation and Recovery of the Systems (Eradication), Recovery of the Lost Systems and Data (Recovery) and Lessons Learned.
In numerous incident response operations, we were able to gain extensive experience and complement the SANS standard with our best practices.
The preparation phase refers to the preparation of all actors involved for a cyber security incident. We distinguish between internal and external preparation. The internal preparation refers to all preparations to be made within the DFIR team of SECUINFRA (documentation of customer information, training/certification, further development of tools and technologies, research of new attack methods/groups, …).
The external preparation happens with you as a customer, optimally before the occurrence of a Cyber Security Incident. If you choose our DFIR framework contract, we will prepare you for a Cyber Security Incident during the onboarding process. In addition, we offer and recommend an annual service review, among other things, to prepare your organization for changing threat conditions. If you have already been affected by a cyber security incident, we are also prepared to provide you with professional ad-hoc support.
The aim of the Identification Phase is to identify deviations in your infrastructure. In this context, we determine whether such deviations represent a cyber security incident for you as a customer. This also includes the classification of the incident into the corresponding criticality.
Among others, the following elements can serve to identify Cyber Secuirty Incidents or will be considered in consultation with you:
- Establishment of monitoring to monitor and detect deviations in IT systems and IT infrastructure.
- Identification of compromised systems using Compromise Assessment.
- Analysis of events from various sources such as log files, error messages or warnings from security tools.
- Identification of a cyber security incident by correlating data from multiple sources.
Containing the damage but also preventing further damage from the current Cyber Security Incident occurs in the Containment Phase. Several steps are required to fully contain the Cyber Security Incident and at the same time prevent the destruction of evidence that might be needed for law enforcement.
In this context, we distinguish between short-term and long-term containments.
Short-term containments limit damage before the Cyber Security Incident worsens. Typically, this is done by isolating network segments and/or compromised assets, routing them to failover* , or shutting down the compromised assets. The latter should only be considered if other containment steps are not possible or take too long and could cause too much damage.
*Failover is a backup mode of operation that automatically switches to a standby database, server or network when the main system fails or is shut down for maintenance.
Long-term containment includes applying temporary fixes to bring production systems back online. The main focus is on eliminating user accounts or backdoors that attackers may have left on the systems. Another main focus is on the elimination of the root cause, e.g., fixing a defective authentication mechanism or fixing a vulnerability that led to the attack.
In the eradication phase, the aim is to actually remove malware or other artifacts introduced by attacks. If possible, the systems are completely cleaned up or a secure recovery is prepared. All possible measures for eradication are discussed and implemented with involved contacts.
The following elements, among others, may be applied as Eradication Steps during a Cyber Security Incident or will be considered in consultation with you:
- Re-imaging of compromised assets ensures complete deletion of all malicious content.
- Elimination of root cause such as patching the vulnerability exploited by the attacker.
- Applying basic security best practices such as updating old software versions or disabling unused services.
- Scanning for malware or remaining IOCs using security solutions such as antivirus, EDR, and/or IOC scanners to ensure that all malicious artifacts have been removed.
After the complete cleanup, we support you in the recovery phase to restore your system landscape. Together with you, we create a sustainable recovery plan. A recovery plan provides, for example, for the secure setup of the systems in a partitioned network area, which is only migrated to a productive network once the cleanup is complete.
The following elements, among others, can be implemented as recovery measures in consultation with you as the customer:
- Setting a time and date for restoring operations.
- Testing and Verification – Testing and verification is intended to ensure that systems are clean and fully functional when they go live.
- Monitoring – Ongoing monitoring for some time or permanently (this is more recommended) after the Cyber Security Incident to observe operations and check for abnormal behavior.
- Further measures to prevent a recurrence of a Cyber Security Incident We can offer you our managed or co-managed services with 24/7 monitoring in this framework. Please contact us.
After the security incident has been completed, all relevant information about the security incident is summarized in the final phase and lessons learned are derived for future incidents and measures.
If required, all relevant results are presented and discussed with you in a final workshop. If desired, lessons learned can be fed back into the preparation phase in order to trigger the Incident Response Lifecycle again for continuous improvement.
Complementary services
Compromise Assessment
The APT Scanner is the core component of our Compromise Assessment service. By professionally evaluating the scan results of the APT Scanner, our cyber defense experts are able to efficiently and reliably detect compromised IT systems in your infrastructure.
Digital Forensics
In the area of digital forensics, our cyber defense experts use APT scanners to quickly gain an initial overview of the extent of a cyber attack. Furthermore, initial conclusions can be drawn about the course of events. Both are absolutely necessary to fully clarify an external cyber attack or internal misconduct.
Incident Response Awards

More than 7000 companies in Germany rely on SECUINFRA directly or via partners in the field of digital forensics and incident response (DFIR)

Best product in the area of Advanced Persistent Threat (APT) Detection and Response

Winner of the Cybersecurity Excellence Award & recognized as the best incident response service company in Europe!

SECUINFRA has been one of the TOP 10 digital forensics consulting/service companies in Europe since 2020 according to Enterprise Security Magazine!
That's why SECUINFRA!

Relevant trainings and certifications, but above all constant incident response missions have contributed to the fact that our incident responders have been able to build up an enormous expert knowledge over the years.

SECUINFRA has one of the most powerful incident response expert teams in Europe. Framework contracts guarantee the availability of our incident response experts at any time.

Incident Response is one of SECUINFRA's core competencies. Over the years, we have continuously perfected our methods, processes and tools to provide you with a professional service at all times.

We conduct onboarding for all incident response customers to prepare them for emergencies. This ensures that they always keep their cool and make the right decisions in an emergency.
References in the area of Incident Response
- SECRECY
SECUINFRA does not name clients or references publicly! The wish of our clients for confidentiality is at all times above the marketing interests of SECUINFRA. - SUCCESS THROUGH RECOMMENDATION
The SECUINFRA DFIR teams have been supporting companies in the field of digital forensics and incident response (DFIR) day by day for years.More than 7000 companies in Germany trust SECUINFRA directly or through partners in the field of digital forensics and incident response (DFIR). - REFERENCES ON REQUEST
In case of legitimate interest we will establish contact to suitable reference customers.
Here you can get in touch with us!
Contact form end of page
Contact form at the bottom of the page
"*" indicates required fields
Our portfolio
©2024 SECUINFRA GmbH. All rights reserved.