Data Breach Assessment
- Detect data leaks as early as possible, regardless of whether they are internal or caused by third parties.
- Understand and reduce your attack surface.
- Identify and close typosquatting sites efficiently.
Darkweb & Clearweb
for quick help
Use the Data Breach Assessment to find out which of your credentials has already been sold and what external attack surface your company offers.
Data breach assessment - recognizing data leakage at an early stage
Attackers often use legitimate credentials to infiltrate your company. This credentials can be made publicly accessible in various ways. For example, many credentials from compromised devices are exfiltrated by so-called Infostealers and offered for sale on the dark web. Another possibility is that users often log in to third-party services with their company e-mail and an corporate password. As soon as the third-party provider is breached, this credentials is published and other attackers can use this data to infiltrate you.
SECUINFRA’s Data Breach Assessment Service provides you with continuous monitoring of sources that indicate the publication or sale of such data and informs you immediately if such a case is discovered. However, this service offers you even more advantages.
To increase the credibility of phishing emails, attackers try to register domains that look very similar to yours and are indistinguishable at first glance, known as typosquatting. With our service, you have the opportunity to recognize such domains at an early stage and have them deactivated at best-effort.
One way for attackers to penetrate your network is through partners and/or suppliers that are connected to your network and have been compromised. We are constantly on the lookout for potentially connected and affected companies and inform you immediately in order to quickly rectify the incident and preventively monitor the connections more closely or terminate them.
Of course, the systems that can be accessed via the Internet are also of particular interest. These systems are regularly scanned and examined for known vulnerabilities (CVEs).
Take control of your cyber security with our Data Breach Assessment. Our targeted and tool-supported method makes it possible to identify traces on public systems, on the Internet, and the darknet. We recommend that you use this process continuously for your entire company, but especially for particularly critical systems and VIPs such as management or administrators.
This process enables you to identify cyber threat intelligence information effectively and with minimal effort.
To visualize the dangers and make the threat easier to understand, consider the following example:
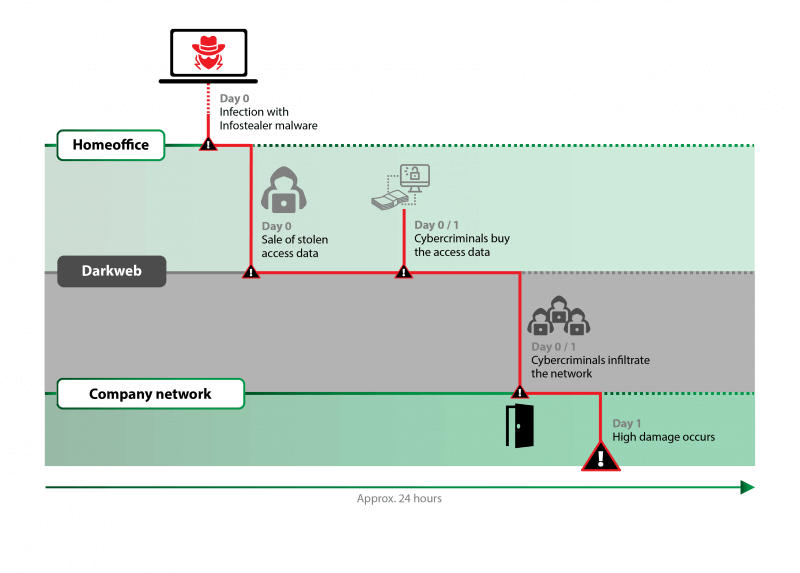
An employee catches an infostealer on his private computer which, among other things, reads credentials from the browser. Trough a synchronization of the browser account between private and company computers, the attackers also gain access to company data. These credentials are offered for sale and acquired by other cyber criminals within a very short time. This also includes the VPN credentials that allows the cybercriminals to access the company network. This allows attackers to cause considerable damage in a very short time.
We help you to identify stolen data and compromised systems quickly and efficiently.
Yasin Ilgar, Managing Cyber Defense Consultant
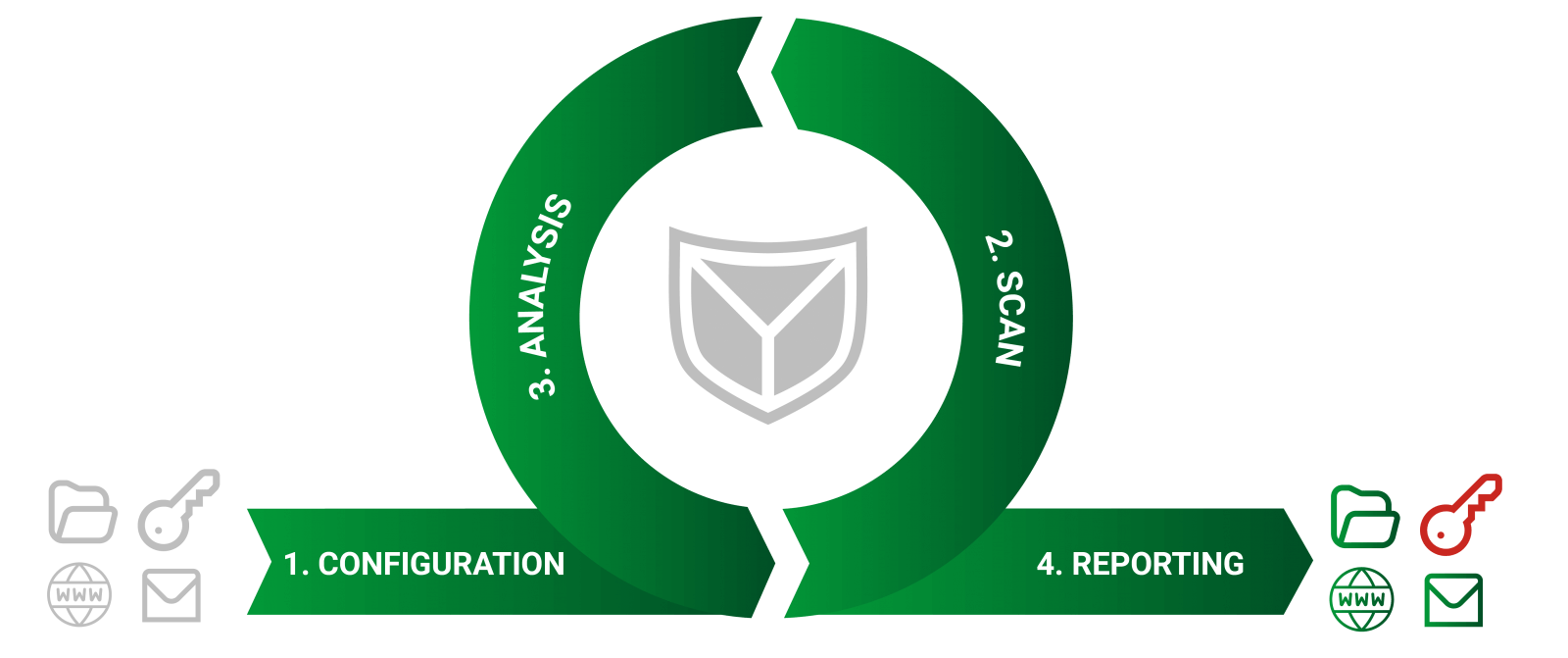
How we carry out data breach assessments
Configuration
During the configuration phase, we work with you to select suitable selectors for the search for your company data. Selectors can be URLs, IPs, user/email addresses, security keys, etc., among others. To obtain a comprehensive overview, SECUINFRA recommends focusing on critical systems, such as
- Your company domain or Active Directory domain
- Host names or IP addresses of publicly accessible systems such as firewalls or VPN gateways
- E-mail addresses of VIP users (members of management or administrators – employees with extended rights to IT systems).
These are then configured for the service and the scan is started.
Scan
The scanning phase depends on the selected service package:
AdHoc Data Breach Assessment (assessment of data breaches)
In our AdHoc service, all incoming events are categorized, analyzed and evaluated by our experts. If a security incident is identified, you will be informed immediately.
Continuous data breach assessment
With our Continuous Service, the initial scan of the systems is regarded as a baseline scan. It provides a qualitative overview of the current security and risk situation in relation to the selectors under consideration. Follow-up scans are carried out at regular intervals, which build on the baseline scan and in which only the changes are considered. Continuous Data Breach Assessment in particular makes the analysis more efficient with each subsequent follow-up and exfiltrations or stolen data can be detected much faster before attackers can explicitly exploit them.
Analysis
In the analysis phase, our cyber defense experts examine the scan results and identify stolen data and compromised IT systems. The events are described, divided into criticality classes and provided with clear recommendations for action. You will be informed immediately if the results are particularly critical.
Reporting
After each scan, you receive a detailed report with all security-relevant results, detailed descriptions, evaluations and clear recommendations for action. The report will be presented to you in a video conference.
Certifications of our experts






The most important FAQs from the field of data breach assessment
The SECUINFRA Data Breach Assessment uses tools to specifically search for traces of stolen or leaked data/information on the Internet and Darknet. A data breach assessment can also reliably detect compromised IT systems. By quickly detecting a compromise, countermeasures can be initiated at an early stage and the attacker’s access to critical systems and data can be prevented. Major damage can thus be avoided.
As a rule of thumb, the domains of your company are required. This also includes domains of subcontractors, foreign locations, etc. Optionally also the IPs of publicly accessible systems and the names of their VIPs.
We generally differentiate between an ad hoc and a continuous scan. In an ad hoc scan, we search all sources once and present you with the results. With a continuous scan, we search all sources regularly and inform you immediately when we have made a discovery.
This of course depends on the result. If your data is published because an attacker has penetrated your network, we also offer you a Digital Forensics & Incident Response Service.
Another component of our service is a takedown service based on the best-effort principle. If this is not possible in your case, we will be happy to advise you on alternative mitigation measures.
Our team is available for you around the clock. As soon as a finding is detected that requires immediate intervention, the responsible persons are informed directly.
Our service not only fits seamlessly into your company’s existing security concepts, but also enhances them. SECUINFRA Data Breach Assessment goes far beyond the possibilities of classic breach detection and thus closes existing gaps in detection. The areas of Cyber Threat Intelligence, Digital Risk Protection and External Attack Surface Management are covered by the SECUINFRA Data Breach Assessment.
SECUINFRA’s Data Breach Assessment Service can be used both preventively – without a known threat situation – and after a security incident has already occurred. The latter scenario includes, for example, situations in which an initial cyber attack on your company network has been confirmed and there are initial indications that data has been exfiltrated or credentials has been offered for sale. Our Data Breach Assessment clarifies the possible exploitation of this data and the associated spread of an attack in record time, thus preventing major damage.
That's why SECUINFRA!

Through training, certifications, and most importantly, ongoing incident response assignments, our incident responders have developed a tremendous amount of expertise over the years.

SECUINFRA has one of the most effective incident response expert teams in Europe. Framework agreements guarantee the availability of our incident response experts at all times.

Incident response is one of the core competencies of SECUINFRA - Made in Germany. Over the years, we have continuously perfected our methods, processes and tools in order to be able to offer you a professional service at all times.

We carry out onboarding for all incident response customers to prepare them for an emergency. This ensures that they always keep their nerve in an emergency and make the right decisions.
References in the area of incident management
SECURITY
SECUINFRA does not name clients or references publicly! Our customers’ desire for confidentiality always takes precedence over SECUINFRA’s marketing interests.SUCCESS THROUGH RECOMMENDATIONSECUINFRA’s DFIR teams have been supporting companies in the field of digital forensics and incident response (DFIR) day in, day out for years, and more than 7,000 companies in Germany trust SECUINFRA directly or via partners in the field of digital forensics and incident response (DFIR).
REFERENCE ON REQUEST
In case of legitimate interest, we will put you in touch with suitable reference customers.
Here you can get in touch with us!
Contact form end of page
Contact form at the bottom of the page
"*" indicates required fields
Quick help in an emergency!
+49 30 555702 112 incident@secuinfra.com
Our portfolio
©2024 SECUINFRA GmbH. All rights reserved.