Managed Detection and Response (MDR) No-Cloud
- Complete solution including hardware, software and services.
- Combination of anomaly detection and mature use cases.
- Best price-performance ratio for medium-sized businesses.


from cyber attacks
With SECUINFRA’s MDR service, you won’t get lost in a flood of alerts. We undertake not only the DETECTION of cyber-attacks, but also their ANALYSIS and RESPONSE.
Comprehensive DETECTION of cyber attacks
The detection of cyber attacks in our MDR service is technologically based on the three pillars of endpoint-based, log data-based and network-based attack detection.
Endpoint-based attack detection & response
At the endpoint, we deploy advanced Endpoint Detection & Response (EDR) systems. Unlike outdated signature-based detection mechanisms such as AntiVirus, modern EDR systems detect anomalies in the execution of programs. If cyber attacks are detected, they can already be response against automatically at the endpoint.
Log-based attack detection
At the heart of our MDR service is Security Information & Event Management (SIEM). Here we process all relevant log data from your company and supplement it with contextual information and threat intelligence feeds. We rely on our globally unique use case library including cyber deception. Use-case-based attack detection is complemented by machine learning.
Network-based attack detection & response
The analysis of network-based data is two-pronged in our MDR service. Both a classic intrusion detection system (IDS) and a modern, protocol-based network detection & response (NDR) system are used. If cyber attacks are detected, they can be defended against automatically at the network level using NDR.
Deep ANALYSIS of Cyber Attacks
When analyzing cyberattacks, it is important to have the right data available and to ask the right questions of that data. We have been dealing with the generation of the right data and the right questions since SECUINFRA was founded in 2010 – you will not find more experience in this field in Germany!

Rapid RESPONSE from cyber attacks
In the event of a cyber attack, in addition to detection and analysis, rapid and professional response is critical. That’s why, when it comes to defending against cyber attacks, we rely on a combination of automated response technologies such as Endpoint Detection & Response (EDR), Network Detection & Response (NDR) and Security Orchestration, Automation and Response (SOAR) on the one hand, and the expert know-how of our cyber defense analysts on the other, who are on duty for you 24/7. In the event of a major incident, our incident responders will support you.
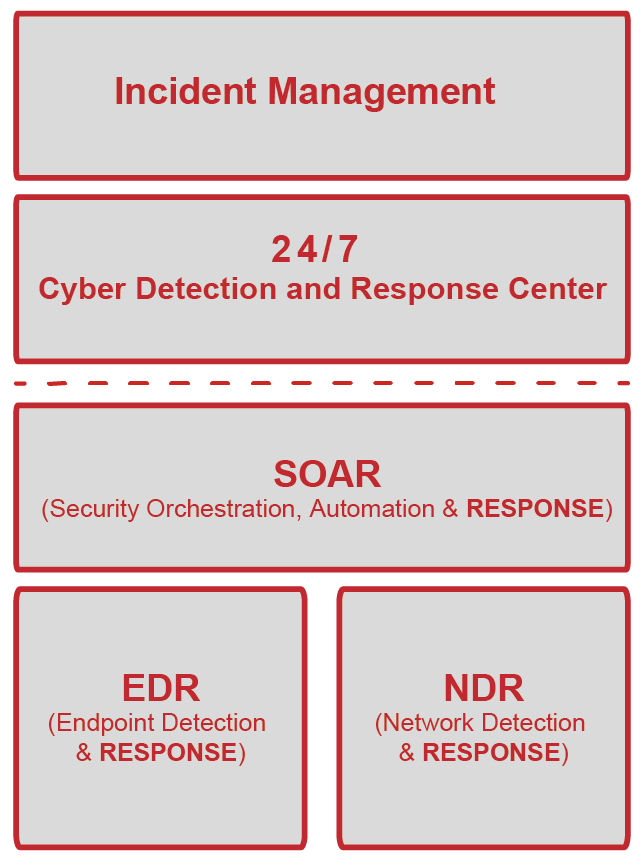
Once an attacker has compromised a system, every minute counts. To stop the attack as early as possible, we rely on automated response technologies. These stop the attacker at the endpoint using EDR, on the network using NDR, and at any other location using SOAR. Which actions are automated is coordinated in advance.
Fastest defense through automated response technologies
24/7 response by cyber defense experts
In addition to automated response technologies, our cyber defense analysts are available 24/7. If necessary, they block compromised accounts, disconnect infected systems from the network or carry out other measures agreed in the Incident Response Plan.
Holistic DETECTION + ANALYSIS + RESPONSE
of cyber attacks instead of flood of alarms!
Many competitors offer only the operation of cyber-attack detection technologies, relying on manufacturers’ standard rules. Ideally, the alarms generated in this way are evaluated before they are forwarded. The actual work, the in-depth analysis and response against cyber attacks, is left to you, the customer.
SECUINFRA offers you a holistic approach, from detection to analysis and response.
With our MDR service, you can achieve a level of security that is otherwise only reserved for large corporations.
David Bischoff, Principal Cyber Defense Consultant
Expert know-how for your safety
Our cyber defense experts are available 24/7 and have in-depth training and experience in detecting, analyzing and defending against cyber attacks. Below is a selection of certifications held by our cyber defense analysts, incident responders, digital forensics experts and malware analysts.








The most important FAQ from the Managed Detection & Response area
Managed Detection and Response (MDR) is an outsourced service that helps organizations detect, respond to and mitigate complex threats. Unlike traditional security measures, which are primarily focused on preventing attacks, MDR focuses on detecting and responding to threats that have breached the first line of defense.
MDR uses advanced technologies such as machine learning and behavioral analysis to identify suspicious activity. As soon as a threat is detected, the MDR team reacts quickly to isolate the threat and minimize its impact. It is therefore a proactive and continuous approach to monitoring cyber security.
Conventional security measures such as firewalls and anti-virus software are important, but are often not enough to detect and respond to complex attacks. MDR provides a deeper and more comprehensive layer of security by combining continuous monitoring, advanced threat detection and rapid response to minimize the risk of security breaches and reduce the impact of a potential incident.
Managed Detection and Response (MDR) is an advanced cyber security service that combines the capabilities of security technologies, advanced analytics and human experts to protect organizations from cyber threats.
MDR service providers continuously monitor a company’s IT infrastructure to identify anomalies and suspicious activity. If a threat is detected, the MDR team responds quickly to investigate the incident, determine the extent of the threat and take appropriate action to mitigate and eliminate the risk.
Compared to in-house solutions, MDR services offer round-the-clock monitoring and response, which is often difficult to achieve with an in-house team. In addition, MDR service providers have expertise in a variety of security areas and stay up-to-date with the ever-evolving cyber threat landscape.
By outsourcing to an MDR service provider, an organization can benefit from the expertise of a dedicated security team without the costs and challenges associated with building and maintaining its own in-house security team. Overall, this can lead to a more efficient and cost-effective cybersecurity solution.
When selecting an MDR service provider, a number of criteria should be taken into account:
- Expertise and experience: A good MDR service provider should have in-depth expertise and proven experience in providing effective MDR services. Check whether the company has experience in your sector or with similar companies.
- Technology: Check which technologies the provider uses. These should be up to date in order to keep pace with the constantly changing threat landscape.
- Response time: The service provider should be able to respond quickly to incidents. A quick response time can help to minimize the damage.
- Reporting and communication: A good MDR service provider should report transparently and regularly on its activities. You should feel well informed and supported when working with him.
- Adaptability: The service provider should be able to adapt its services to the specific needs of your company.
- Value for money: Last but not least, the cost of the service should be proportionate to the services provided and the level of protection expected.
Remember that choosing an MDR service provider depends on many factors, including the size of your business, the industry you operate in and the specific risks you face. Take advantage of our support and let us advise you on the various criteria.
Since the detection mechanisms are selected from our use case database on a customer-specific basis, it is not possible to make a categorical statement in this regard.
However, during an initial consultation, we would be happy to show you the potential coverage provided by the MDR service using the MITRE ATT&CK matrix. Please contact our sales team for this.
At the beginning of the contractual relationship, a fixed price per asset is set for various asset categories. Asset categories are differentiated between workstations, servers, network devices and firewalls (up to 1GB/s).
With our fixed price model, your future costs are clearly calculable and you save yourself unpleasant surprises.
After the assignment, the onboarding phase begins, during which close coordination with you takes place. Since cyber-attack detection is highly dependent on the particular IT landscape, service parameters need to be adapted to your organization at this stage.
Since this coordination is crucial for success, we take between four and eight weeks for this, depending on the size of the organization and the number of contacts.
During the onboarding phase, technical implementation is also already underway. However, this is usually completed much more quickly than the substantive coordination between the contracting parties.
Finally, the service goes into trial operation, which usually lasts a month. The total time to go live from the specified start date is therefore 8 to 12 weeks.
At the beginning, a precise coordination between the technical contacts on the customer side and the cyber defense experts of SECUINFRA is necessary in order to outline the existing IT landscape and to select suitable detection mechanisms.
The primary and ongoing task for you as a customer is to provide SECUINFRA with all the necessary information about your IT landscape so that the detection mechanisms always function reliably.
The task of your IT is then to connect all systems to be monitored to our system by installing agents or configuring the forwarding of logs via syslog. However, we will support you in this as far as possible.
SECUINFRA sets very high standards when recruiting staff and introduces each new employee to all relevant specialist topics in a program lasting several months to ensure consistent competence.
Since SECUINFRA has been exclusively dedicated to the detection, analysis and defense of cyber attacks since its foundation in 2010, our analysts already have extensive experience.
As a customer, you have a fixed contact person in the MDR area who exchanges information with you on a cyclical basis and is available if required. This applies to all administrative matters.
Since our cyber defense analysts are on duty around the clock, there can be no fixed point of contact for operational service that is available at all times. However, we make every effort to provide you with the same contact persons for each shift and for as long as possible.
According to the Service Level Agreement (SLA), the contractually guaranteed response time is 30 minutes, but the response is usually provided in less than 15 minutes.
The Service Level Agreement (SLA) guarantees 99.5% availability of the central components of the MDR service.
The so-called retention time is 60 days. During this time, the data can be used to detect and defend against attacks.
Our awards in the field of MDR

Best SIEM consulting/service company in Europe

Market leader in Security Information Event Management (SIEM)

Leading provider of SIEM consulting services in Germany

TOP 10 SIEM consulting/service companies in Europe
Our MDR service: Optimally adapted to your IT landscape!
Every IT landscape is different and none is completely static. To take this into account, our MDR service does not offer a fixed set of detection mechanisms, but always makes an individual selection and adaptation of all centralized detection mechanisms.
To achieve this goal, the onboarding of new customers into the SECUINFRA MDR service starts with a detailed exchange about the customer’s requirements and IT landscape. The goal is to develop a mutual understanding of the elementary processes, a mapping of the IT landscape to be monitored and a common detection target within the framework of a series of workshops.
The service workshops are followed by the deployment of the platform. For this purpose, log and network appliances are installed on site to ensure secure and reliable collection and transmission of security-relevant log and network data.
As soon as the first data has been transferred to one of our two data centers in Germany, the onboarding of the customer into SECUINFRA’s security monitoring begins. To enable environment-specific detection mechanisms, the provision of the necessary context data is coordinated.
To achieve the best possible response in the event of an emergency, key IT contacts are integrated into our runbooks.
As a rule, onboarding in SECUINFRA MDR is completed after four to eight weeks and the new customer moves on to SECUINFRA’s regular 24/7 monitoring.
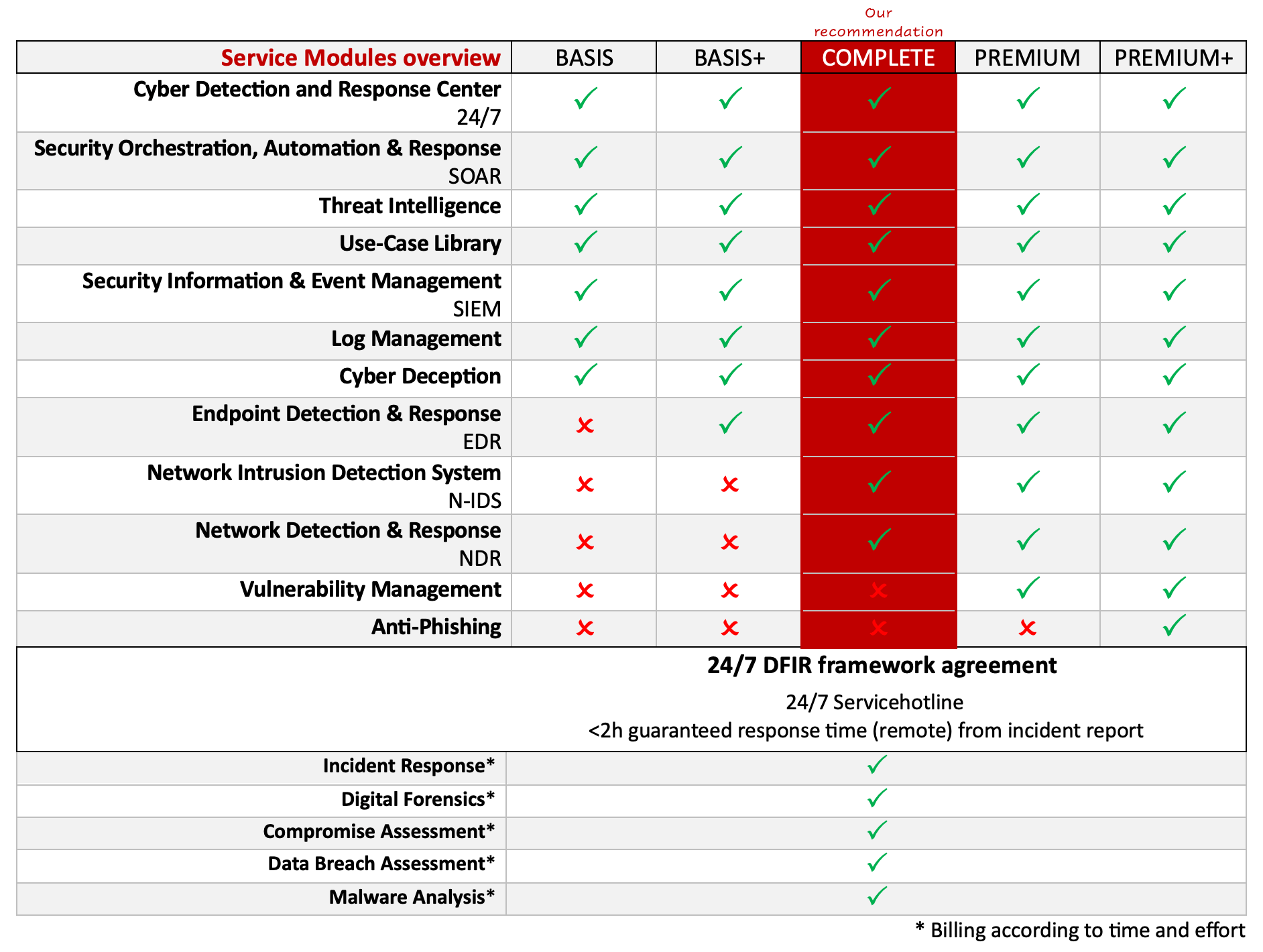
MDR Service Modules
Our MDR service has a modular structure and even the basic version includes a very wide range of functions and services that go far beyond basic coverage of most requirement profiles.
With these modules, our Managed Detection & Response service already meets all the requirements defined by Gartner for a full MDR service and a Managed SOC (MSOC). Most cyber defense compliance requirements are also met out of the box with our service.
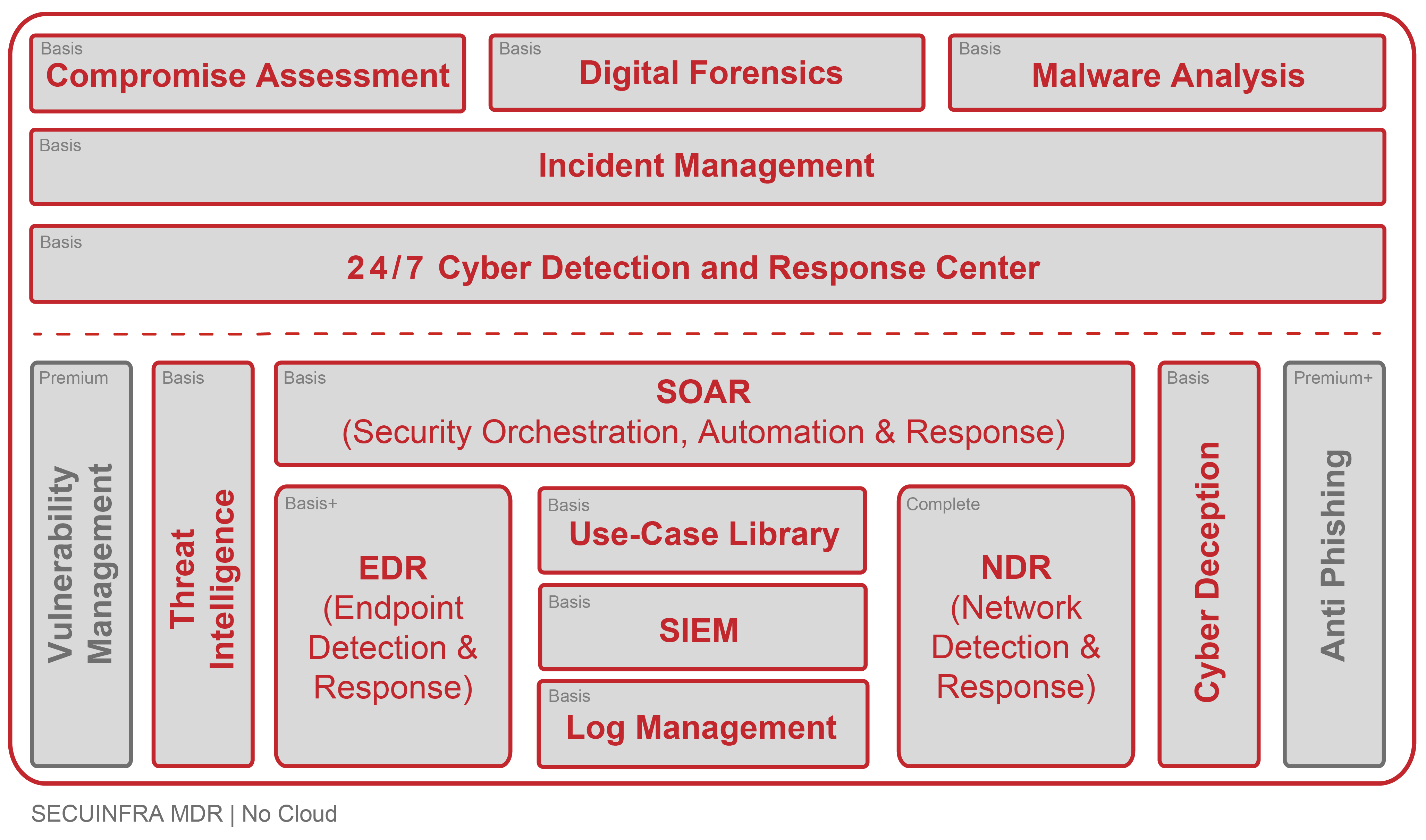
Our MDR Basic Service already includes far more than comparable services from our competitors. It includes all technologies and services for comprehensive DETECTION, ANALYSIS and RESPONSE of cyber attacks based on event log data, threat intelligence feeds and cyber deception.
- 24/7 Cyber Detection & Response Center: Our Cyber Detection & Response Center (CDRC) is where true 24/7 monitoring of your systems takes place. Our analysts are on duty for you around the clock, 365 days a year, to detect cyber attacks on your company at an early stage, analyze them and defend against them in a targeted manner. Our 24/7 service keeps “Mean Time to Detect” (MTTD) to a minimum.
- Security Orchestration, Automation & Response (SOAR): To reduce alarm processing time, SECUINFRA deploys a Security Orchestration, Automation & Response system (SOAR). With its help, analyses and reactions are partially automated. In this way, we reduce the “Mean Time to Respond” (MTTR) to a minimum so that, in the event of a successful cyber attack, we can stop the attacker as early as possible and avert greater damage.
- Threat Intelligence: SECUINFRA uses strategic threat intelligence to select detection mechanisms and operationalizes threat intelligence data as part of threat hunting to uncover previously undetected attacks.
- Use case library: Our use case library is the result of many years of experience in setting up, operating and using SIEM systems in numerous customer projects and as a SOC service provider. In contrast to the out-of-the-box rules of SIEM manufacturers, the use cases in the SECUINFRA Use Case Library are selected on a customer-specific basis to ensure compatibility with the IT landscape. In this way, we avoid unreliable use cases, high false positive rates and the need for constant contact with the customer.
- Security Information & Event Management (SIEM): The SIEM system is used to centralize all security-related log entries and events from third-party sources (e.g. anti-virus, IDS, EDR). Numerous use cases developed by SECUINFRA since 2010 in the areas of threat detection, user and entity behavior analytics (UEBA) and optionally machine learning are applied.
- Central log management: The database for the SIEM area is provided by our central log management. Security-related log data is collected centrally and stored in a searchable manner for a period of 60 days.
- Cyber Deception: With Cyber Deception, we deceive cyber criminals to identify their activities in their infrastructure. To do this, we smuggle specially prepared resources such as shares, accounts or supposed access data into your IT environment. In the attacker’s attempt to spy on your IT (Reconnaissance), to spread further (Lateral Movement) and to extend privileges (Privilege Escalation), sooner or later he will inevitably resort to the specially prepared resources. Since they are not used elsewhere, their use is a very clear sign that an attacker is on the network. This information flows into the central SIEM system as alarms with a very high priority.
However, should a major security incident occur, SECUINFRA provides support with the following services, which are billed on a time and material basis:
- Incident Management: In the event of major cyberattacks, professional coordination and communication is essential to contain and manage the attack. That’s where our incident response experts come in to help you with technical and non-technical challenges.
- Compromise Assessment: In the event of a cyber attack, it is extremely important to answer the question as quickly and reliably as possible: Which systems have been compromised? Our Compromise Assessment answers this question as quickly, efficiently and reliably as possible.
- Digital Forensics: Digital forensics enables detailed analysis and reconstruction of security incidents. Our goal here is to learn from the cyberattack and refine your defenses. In addition, the findings of our digital forensics experts enable prosecution and help you make claims against cyber risk insurance companies.
- Malware analysis: As part of malware analysis, we examine how malware works with the goal of gaining comprehensive insight into how it operates, understanding its potential impact on a system, and identifying appropriate measures for future mitigation and prevention. Our malware analysts use both static and dynamic analysis as well as reverse engineering.
Endpoint-based detection and response against cyber attacks is one of the most important pillars of modern cyber detection & response and is an optimal complement to log data-based attack detection.
Our MDR service BASIS+ therefore includes the following services:
- Endpoint Detection & Response (EDR): Endpoint Detection & Response (EDR) systems form the technological basis for modern detection and response against cyber attacks. To detect attacks on endpoints (workstations & server systems), SECUINFRA uses established EDR technologies for behavior-based detection of anomalies on endpoints. In addition to the pure detection of cyber attacks, EDR also offers the possibility to actively react to detected attacks. For example, processes can be terminated, local user accounts can be locked or entire systems can be isolated automatically. This helps to further reduce Mean Time to Respond (MTTR) by stopping a successful cyberattack at the most common entry point of a cyberattack, the endpoint.
The MDR Complete service adds the pillars of endpoint-based cyber attack detection and response and log data-based attack detection to the pillar of network-based cyber attack detection and response. This provides you with comprehensive detection, analysis and response against cyber attacks and puts you in an excellent position in this area.
- Network Intrusion Detection System (N-IDS): The traditional N-IDS is a network traffic virus scanner that detects attacker behavior based on signatures. Using traditional N-IDS, our analysts detect the transmission and use of known malware, as well as access to the command-and-control infrastructure of known attackers.
- Network Detection & Response (NDR): In addition to the classic Network IDS, SECUINFRA offers behavior-based detection of attackers at the network level. This uses an advanced Network Detection & Response (NDR) system that, unlike traditional products such as N-IDS, relies on behavioral pattern detection. The data generated is not only extremely valuable for detecting attacks, but is also used by our analysts as part of the response process to contextualize suspicious events. In addition to attack detection and contextualization capabilities, our NDR also provides the ability to actively respond to detected attacks. For example, communication relationships can be terminated, access to command and control servers can be blocked, or IT systems can be isolated automatically to minimize the impact of detected security incidents.
Our MDR Premium Service complements our comprehensive MDR Complete Service for detecting, analyzing and defending against cyber attacks with Vulnerability Management, which is important for compliance reasons.
- Vulnerability Management: Known vulnerabilities are often not closed because there is no overview of the current patch status and new vulnerabilities. This is where our Vulnerability Management Service comes in. We check your systems for known vulnerabilities and provide you with consolidated results.
In addition to the comprehensive detection, analysis and response against cyber attacks from our MDR Complete service and vulnerability management, which is important for compliance reasons, we support you with our MDR Premium+ service in reducing the risk of successful phishing attacks on your company:
- Anti Phishing: Phishing is one of the main gateways for successful cyber attacks. The risk can be reduced through various measures such as employee education and awareness, as well as technical protection measures such as anti-spam solutions, browser extensions and sandboxes. Nevertheless, it happens again and again that suspicious e-mails reach the employees and they have to decide whether to open the attachment, click on the link or rather delete the suspicious e-mail. Wouldn’t it be very helpful to have experts at your side at all times when making this potentially momentous decision? This is exactly where SECUINFRA’s anti-phishing service comes in. In case of suspicious mails, your employees forward them to our experts via phishing button. They check the mails from an expert’s point of view and give your employees a prompt answer: phishing or legitimate.
That's why MDR from SECUINFRA!
Supported by automation and SOAR systems, our specialists quickly categorize, prioritize and triage security incidents. Depending on the agreement with the customer, we escalate the tickets to your employees or take over further processing ourselves.
Escalation and tracking of incidents as well as reporting and automation are our strengths. In the event of a security incident, we contact your specialist departments so that security incidents can be processed quickly and efficiently and further damage can be avoided.
We support you with critical security incidents through incident management, forensics and malware analysis. In addition, we assess your current security situation through threat hunting and integrate threat intelligence where appropriate. Malware infections and major security incidents are routine for our cyber defense analysts.
In order to be able to offer a stable service, all components of the MDR service are monitored at hardware and software level. This also includes the appliances installed at the customer's premises.
Against the backdrop of a constantly changing threat situation, the continuous development of our Managed Detection & Response Services is an integral part of our service. The detection mechanisms and response options are therefore being continuously developed for all customers of our service.
As a customer, you will be informed about these further developments as part of our regular service reviews and can also use this progress to prove compliance with compliance requirements (e.g. VAIT, BAIT, TISAX, ISO27001) or legal requirements such as KRITIS.
More informative blog posts and technical articles!
References in the area of Managed Detection & Response (MDR)
- SECURITY
SECUINFRA does not name clients or references publicly! Our customers’ desire for discretion always takes precedence over SECUINFRA’s marketing interests. - SUCCESS THROUGH RECOMMENDATION
Since 2010, we have focused exclusively on cyber attack detection, analysis and defense. Almost all customers have become aware of SECUINFRA through recommendations and have in turn recommended us to others. - REFERENZ AUF ANFRAGE
Bei berechtigtem Interesse stellen wir den Kontakt zu geeigneten Referenzkunden her.
Here you can get in touch with us!
Contact form end of page
Contact form at the bottom of the page
"*" indicates required fields
Our portfolio
©2024 SECUINFRA GmbH. All rights reserved.








