Digital Forensics
- 24/7 availability of our certified digital forensics experts.
- Quick help for every company. Guaranteed response times through framework agreement.
- Understand and rectify the course of events.
since 2017
für for quick help Hilfe
Use digital forensics techniques to understand exactly how the attacker got into the system and what they did.
Analysis of digital traces and crime scenes Understand
Every perpetrator leaves traces. By professionally analyzing these traces, it is possible to trace how the attacker got into the system and what he did there. The forensic analysis of a system requires a professional and coordinated approach in order not to cover any traces and a forensic laboratory for efficient analysis.
SECUINFRA forensically analyzes the affected systems and presents the determined actual state in a reliable and comprehensible manner.

Incidents can be detected in various ways, e.g. by an alarm in EDR (Endpoint Detection and Response) or by a call from an employee who has detected suspicious activity on their system. There are many ways to clearly classify the alarm, but a forensic analysis is the most thorough method to obtain certainty.
We clarify the handling, transmission and analysis of digital evidence. As there are numerous technological means of preparing systems for forensic analysis or optimizing personnel and processes, SECUINFRA also supports you in increasing your forensic readiness.
Understand what the attacker has done on your systems and lock them out faster.
Evgen Blohm, Cyber Defense Consultant
The most important FAQs from the field of digital forensics
Generally all common systems such as Windows, Linux, MacOS clients and servers, but also other devices such as smartphones. In general, however, other data can be included in an analysis, such as network data from a firewall or a proxy.
The result of a forensic analysis is the answer to certain questions that we put to the system in consultation with you. We determine the attacker’s activities on the system and display them. Since the forensic analysis of a system can take a long time, it is all the more important to formulate these forensic questions in concrete and specific terms.
Generally none. However, technical settings can be activated that increase the information content of the systems and can therefore be used for forensic analyses. This is referred to as “forensic readiness”. Increasing this “forensic readiness” can significantly improve the efficiency of forensic analysis and provide more insights into the attackers’ approach.
Do not switch off the device beforehand! This can destroy relevant traces, such as the working memory. The device must be isolated on the mains side until all necessary system images have been created.
There are two options here, either the complete physical system is transmitted or only the digital images. If the complete device is to be transferred, this will be done by courier. If images that have already been created are to be transmitted, this is done via a secure file storage facility provided by SECUINFRA.
There are different types of images that are created by the affected systems and then used for the analysis. If the system is still switched on, an image of the working memory (RAM) can be created. This image contains a lot of relevant information about processes, network connections, etc. In most cases, an image of the hard disk is created. There are different types of images here, such as the full disk image and the triage image. The full disk image is a 1:1 bit copy of the hard disk and contains all the information that can be found on the original hard disk. As the creation of this image can be very time-consuming, so-called triage images are often used in time-critical situations. Only previously defined files that are of forensic interest are copied. This has the advantage that the analysis is significantly faster, but the disadvantage that not all the required information may be available.
Our procedure for collecting and storing evidence is based on the ISO 27037 standard. The evidence is stored securely in a safe and the laboratories are only accessible to authorized personnel.
Certifications of our experts






Our approach to digital forensics
Our approach to digital forensics, structured according to the guidelines of the National Institute of Standards and Technology (NIST), divides the investigation process into four main phases: Collection, Examination, Analysis and Reporting. These phases are briefly explained below. Each of these phases is critical to the success of a digital forensic investigation and requires specialized knowledge and tools.
Targeted forensic analysis to better understand cyber attacks and the course of events.
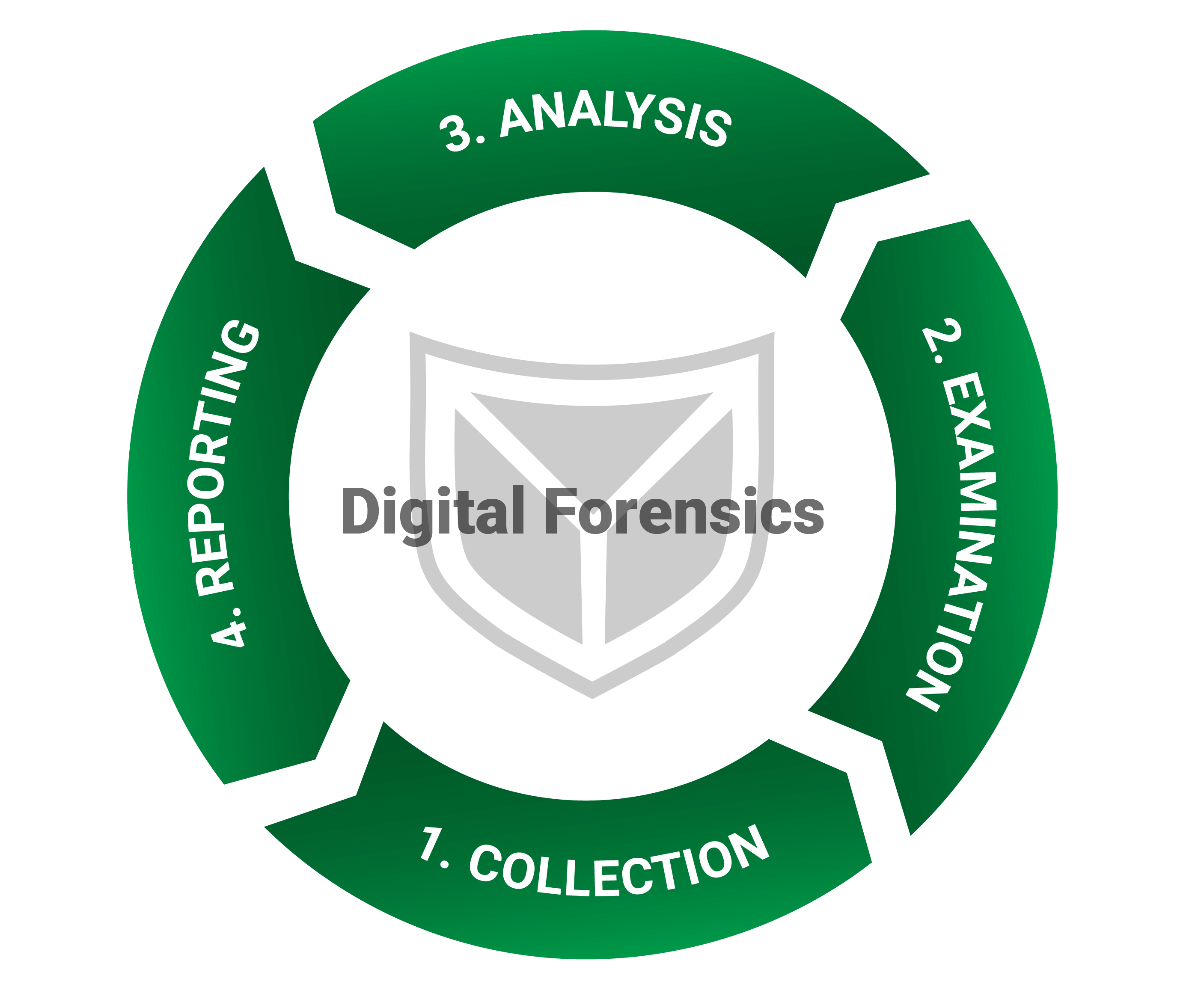
The aim of this phase is to identify, collect and secure digital evidence. This includes backing up data from various sources such as computers, network devices, storage media and mobile devices. The aim is to capture the evidence in such a way that its integrity is preserved and it is protected from alteration, which is crucial for its subsequent legal use.
In this phase, the collected data is analyzed in detail using special tools and techniques to identify relevant information. This can include searching file systems, searching log files and restoring deleted data. This is a technically demanding step that requires expert knowledge in order to effectively isolate and process the relevant data.
In the analysis phase, the information found during the investigation is evaluated to determine how the incident occurred and who may be responsible. In this phase, data patterns, user activity and other relevant indicators are analyzed to draw conclusions about the nature of the security incident or crime. This phase often requires a critical evaluation and interpretation of the data.
In the final phase, a detailed report is prepared in which the results of the investigation and analysis are presented. The report should be clear, precise and written in language that is understandable to laypersons. It usually contains a summary of the incident, a description of the forensic steps taken, the evidence found and the conclusions drawn. The report is of crucial importance for legal proceedings and for communication with interest groups.
That's why SECUINFRA!

Through training, certifications, and most importantly, ongoing incident response assignments, our incident responders have developed a tremendous amount of expertise over the years.

SECUINFRA has one of the most effective incident response expert teams in Europe. Framework agreements guarantee the availability of our incident response experts at all times.

Incident response is one of the core competencies of SECUINFRA - Made in Germany. Over the years, we have continuously perfected our methods, processes and tools in order to be able to offer you a professional service at all times.

We carry out onboarding for all incident response customers to prepare them for an emergency. This ensures that they always keep their nerve in an emergency and make the right decisions.
Awards in the area of incident response

More than 7000 companies in Germany rely on SECUINFRA directly or via partners in the field of digital forensics and incident response (DFIR)

Best product in the area of Advanced Persistent Threat (APT) Detection and Response

Winner of the Cybersecurity Excellence Award & recognized as the best incident response service company in Europe!

SECUINFRA has been one of the TOP 10 digital forensics consulting/service companies in Europe since 2020 according to Enterprise Security Magazine!
More informative blog posts and technical articles!
References in the area of incident response
-
SECURITY
SECUINFRA does not name clients or references publicly! Our customers’ desire for confidentiality always takes precedence over SECUINFRA’s marketing interests. -
ERFOLG DURCH EMPFEHLUNG
Die SECUINFRA DFIR-Teams unterstützen seit Jahren Tag für Tag Unternehmen im Bereich digitale Forensik und Incident Response (DFIR).Mehr als 7000 Unternehmen in Deutschland vertrauen SECUINFRA direkt oder über Partner im Bereich digitale Forensik und Incident Response (DFIR). -
REFERENCE ON REQUEST
In case of legitimate interest, we will put you in touch with suitable reference customers.
Here you can get in touch with us!
Contact form end of page
Contact form at the bottom of the page
"*" indicates required fields
Quick help in an emergency!
+49 30 555702 112
incident@secuinfra.com
Quick help in an emergency!
+49 30 555702 112 incident@secuinfra.com
Our portfolio
©2024 SECUINFRA GmbH. All rights reserved.








