TechTalk
Here you will find articles on the latest findings and in-depth analyses in the field of IT security, presenting both current trends and the in-depth expertise of our cyber defense experts. Immerse yourself in the world of cyber security, enrich your knowledge and stay at the forefront of technological progress.
Modern EDR or XDR solutions are capable of detecting suspicious behavior. The widely used Elastic solution has been integrating this feature with Elastic Defend since 2019 and offers industry-leading transparency.
Below we show how security experts work with it.
Companies and organizations operating in the critical infrastructure sector (KRITIS) are subject to special requirements. The BSI Law obliges them to regulate the protection of these critical infrastructures at IT level. SECUINFRA has produced a white paper as a guide and orientation aid to help affected companies with implementation. This guide is available here as a free download.
In this article about the dynamic world of cyber deception, you will learn how dangerous attackers can be made visible with little effort. Using an example implementation and its connection to a SIEM system, we also show how knowledge of previously unknown attacks and attack patterns can be incorporated into the defense and strengthen cyber resilience.
Various tools are used to detect IT security incidents within an organization. The foundation for this is the combination of Endpoint Detection and Response (EDR) and Network Detection and Response (NDR) systems.
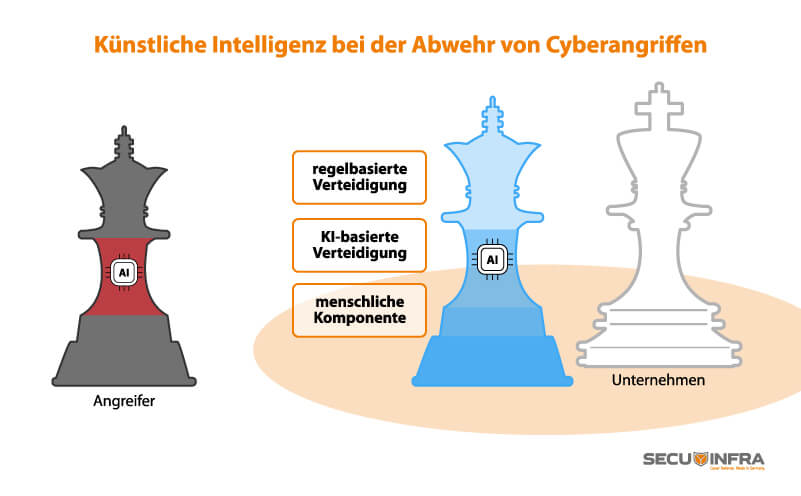
Artificial intelligence is a much-discussed topic. It offers great opportunities, but obviously also harbors risks. And it also has two faces when it comes to IT security.
There are some beliefs, half-truths and myths - and not just in IT - that persist for an astonishingly long time. If they affect the security of a company, it becomes dangerous.
Cyber attacks often lead to unauthorized access to personal or confidential data. If the data is stolen from the organizational network in the process, it is referred to as a data leak or data exfiltration. The motives for data theft are diverse and range from industrial espionage and blackmail to resale or identity theft. Recently, there has also been a…
Edge infrastructure, such as internet-exposed firewalls, routers, VPN-Gateways etc. are a common initial access target for cybercrime and espionage actors since these appliances are challenging to defend. According to the vulnerability discovery service LeakIx as many as 30 thousand internet-exposed Cisco devices may already have been compromised...
In this article, our author shows how Compromise Assessment can meaningfully extend traditional IT security tools to help organizations achieve robust cyber resilience.
What benefits do SOAR solutions actually offer in concrete terms, and what do companies achieve with them? We provide answers to the 5 most frequently asked questions about SOAR!
Learn in this article how you can realize effective, sustainable and reliable threat detection through the interaction of NDR, EDR and SIEM.
Today many businesses rely on virtualization technology to run and scale their infrastructure. One of the most popular Hypervisor systems on the market is VMware ESXi, which is regularly targeted in Ransomware attacks for the last 3+ years to increase damage to the victims IT systems.
Our portfolio
©2024 SECUINFRA GmbH. All rights reserved.