Managed Detection & Response for Microsoft
- Damage prevention through
Fastest detection and response - German-speaking Cyber Defense Experts
- Quick and easy service start



of a cyber attack
Become a customer
We detect cyber attacks and defend against them before high damage is done.
Comprehensive DETECTION of cyber attacks
Our Microsoft specialists evaluate data from Microsoft Sentinel and Microsoft Defender to detect, analyze and defend against threats on endpoints and in multi- and hybrid-cloud systems.
In addition to data analysis, our experts use state-of-the-art tools and techniques to efficiently identify anomalies and potential security risks. Through continuous training and certification, they are always up to date with the latest Microsoft technologies. The close cooperation with Microsoft ensures that they are informed about updates and innovations at an early stage. This allows us to be proactive and provide the best possible protection against ever-changing threats. With our expertise and technology, we offer companies comprehensive security protection for their Microsoft infrastructure.
Our analysts are highly qualified cyber defense experts.
We are united by a common goal: preventing damage from cyber attacks!
Klaus Wunder, Senior Cyber Defense Consultant
MDR Microsoft Service Module
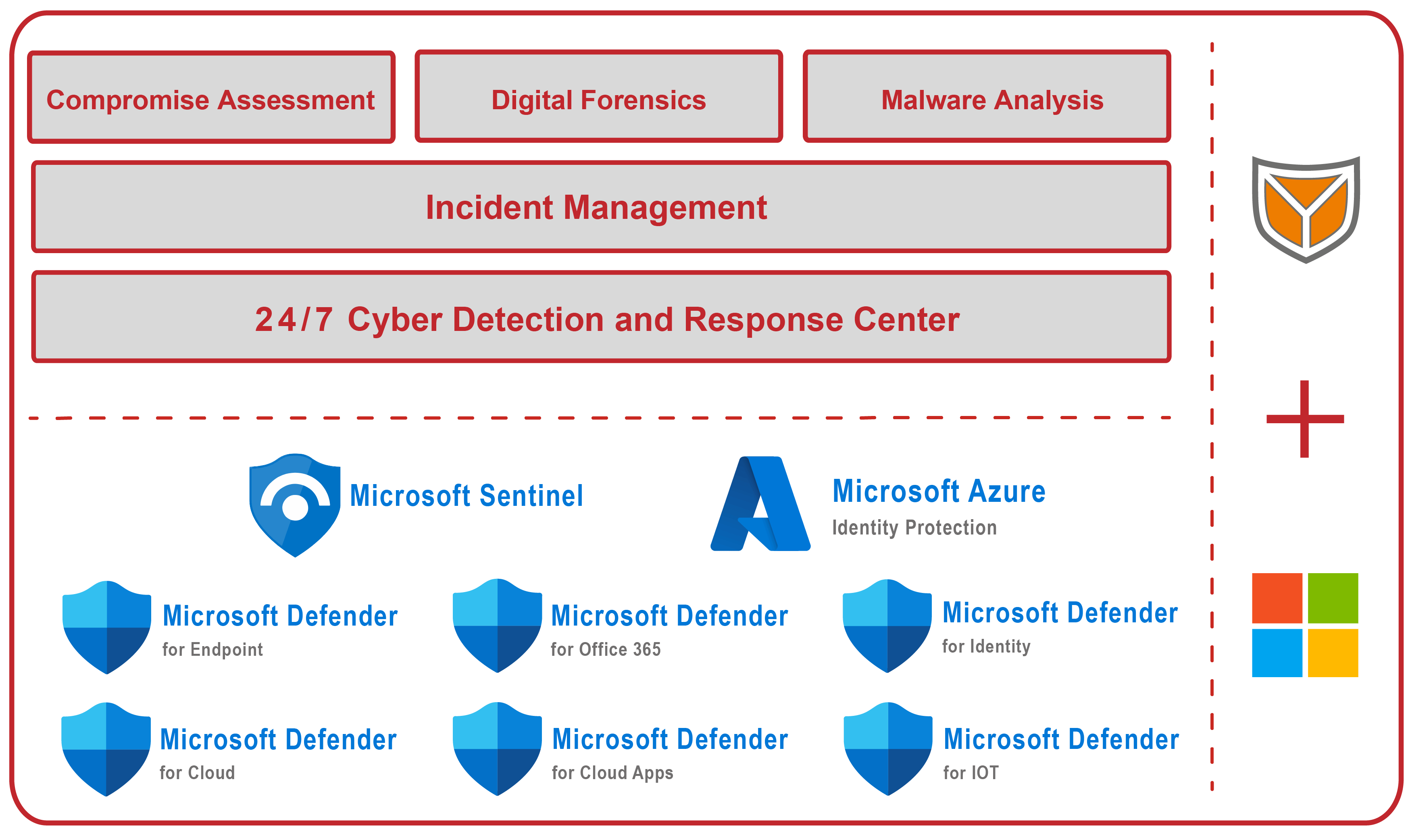
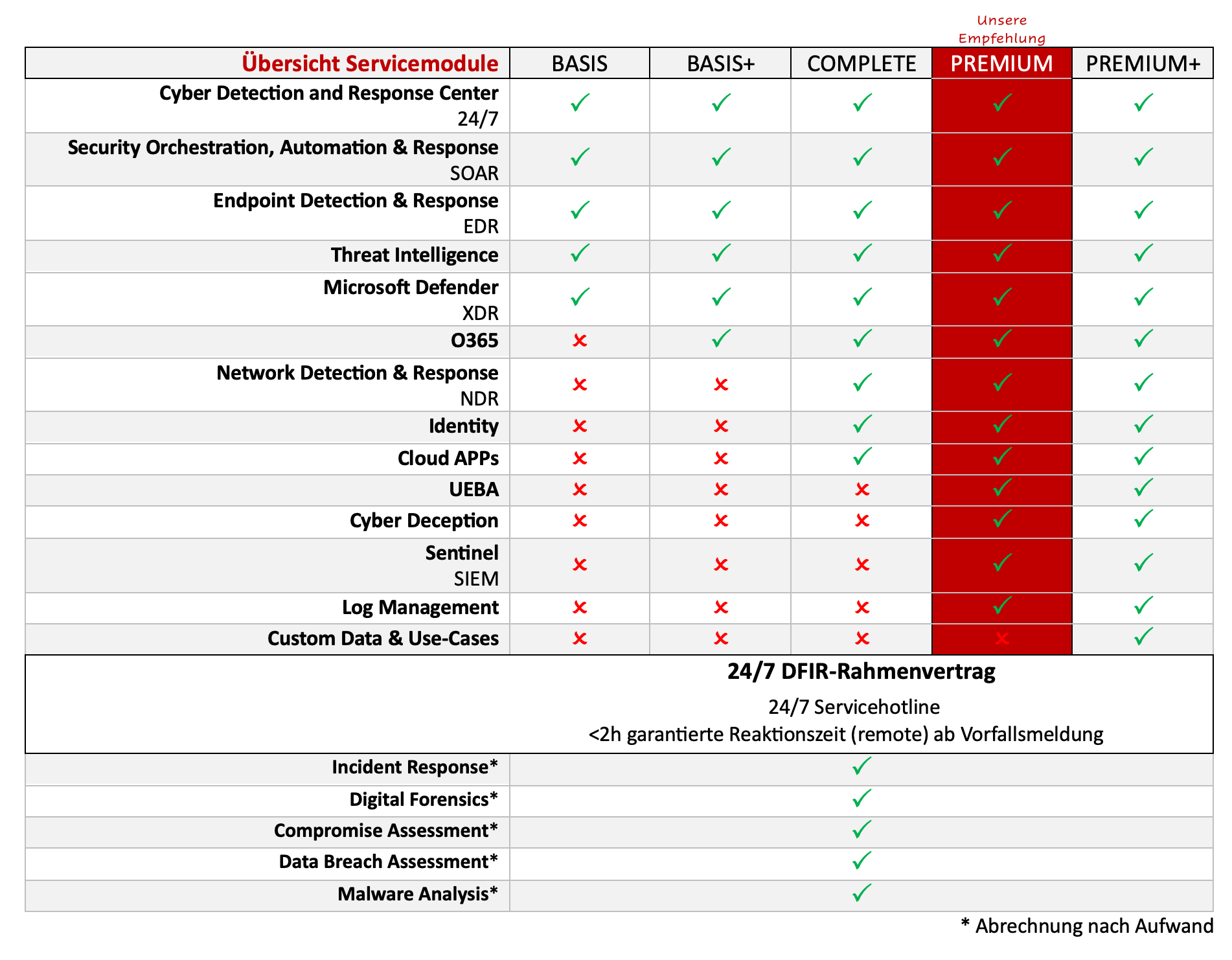
Our MDR service is based on the Microsoft Security Suite. The SECUINFRA 24/7 Cyber Detection & Response Center (CDRC) is the heart of our service. In cooperation with Microsoft, SECUINFRA offers a state-of-the-art Cyber Defense & Response Service. This has a modular structure in 5 expansion stages and guarantees solutions for every requirement.
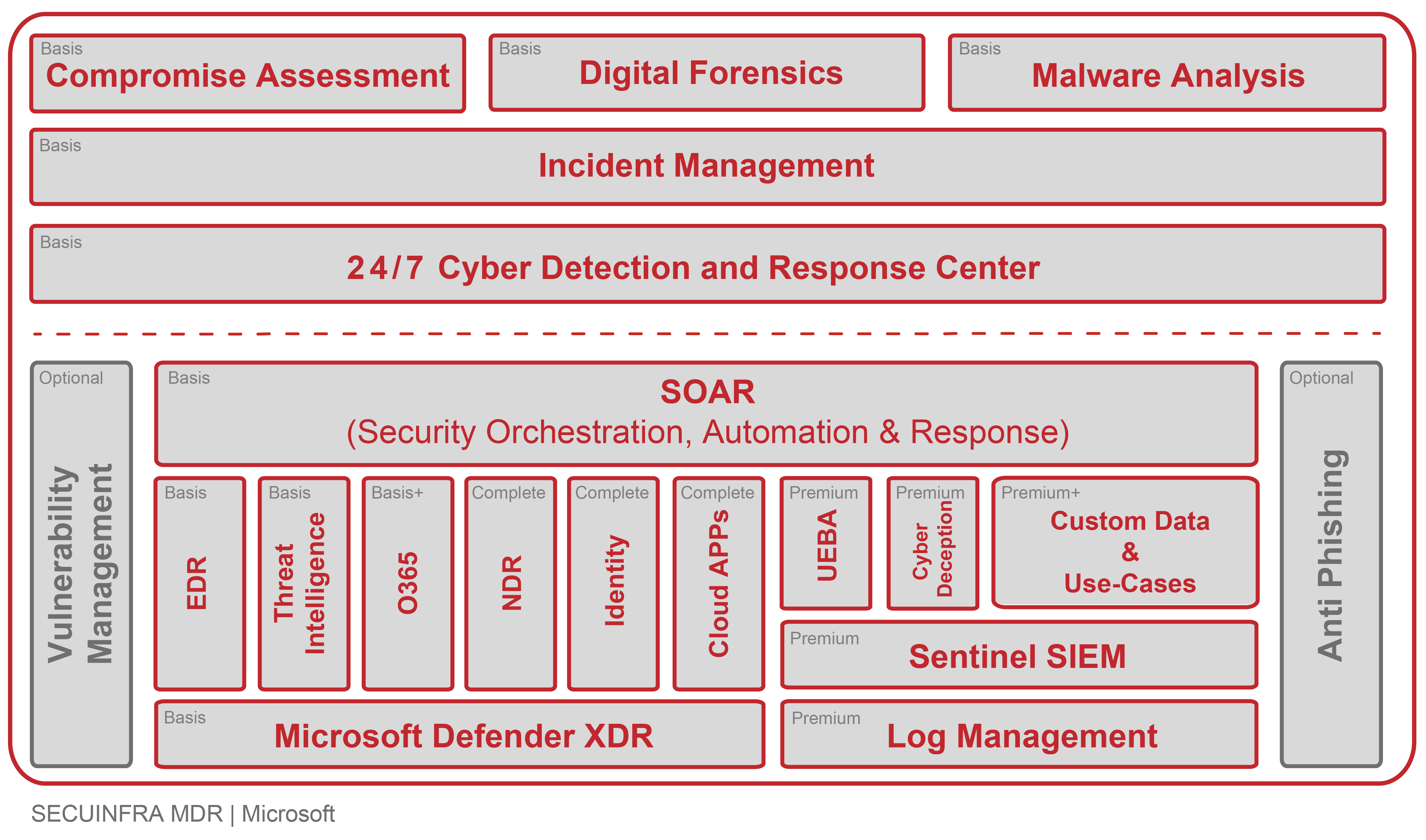
Our MDR Basic Service already includes services that go far beyond the standard. It includes all technologies and services for comprehensive DETECTION, ANALYSIS and PREVENTION of cyber attacks on endpoints. This module is based on Microsoft Defender for Business and is supported by MS Sentinel SOAR, MS Defender XDR and Threat Intelligence.
- 24/7 Cyber Detection & Response Center: Our Cyber Detection & Response Center (CDRC) is where true 24/7 monitoring of your systems takes place. Our analysts are on duty for you around the clock, 365 days a year, to detect cyber attacks on your company at an early stage, analyze them and defend against them in a targeted manner. Our 24/7 service keeps “Mean Time to Detect” (MTTD) to a minimum.
- Security Orchestration, Automation & Response (SOAR): To reduce alarm processing time, SECUINFRA deploys a Security Orchestration, Automation & Response system (SOAR). With its help, analyses and reactions are partially automated. In this way, we reduce the “Mean Time to Respond” (MTTR) to a minimum so that, in the event of a successful cyber attack, we can stop the attacker as early as possible and avert greater damage.
- Threat Intelligence: SECUINFRA uses strategic threat intelligence to select detection mechanisms and operationalizes threat intelligence data as part of threat hunting to uncover previously undetected attacks.
- Microsoft Defender for Business (EDR): Endpoint Detection & Response (EDR) systems form the technological basis for modern detection and defense against cyber attacks. To detect attacks on endpoints (workstations & server systems), SECUINFRA relies on the established Microsoft Defender for Business for behavior-based detection of anomalies on endpoints.
- Microsoft Defender XDR: Protects against cyber threats such as ransomware and phishing. Depending on the module activated, logsare combined to protect endpoints, identities, emails, collaboration tools, cloud apps and data from cyber threats. AI and automation are also used to directly ward off cyberattacks and prioritize incidents. In addition to the pure detection of cyber attacks, XDR also offers the option of actively responding to detected attacks. For example, processes can be terminated, local user accounts can be locked or entire systems can be isolated automatically. This helps to further reduce Mean Time to Respond (MTTR) by stopping a successful cyberattack at the most common entry point of a cyberattack, the endpoint.
However, should a major security incident occur, SECUINFRA provides support with the following services, which are billed on a time and material basis:
- Incident Management: In the event of major cyber attacks, professional coordination and communication is essential to contain and manage the attack. That’s where our incident response experts come in to help you with technical and non-technical challenges.
- Compromise Assessment: In the event of a cyber attack, it is extremely important to clarify the question as quickly and reliably as possible: Which systems have been compromised? Our Compromise Assessment answers this question as quickly, efficiently and reliably as possible.
- Digital Forensics:Digital forensics enables the detailed analysis and reconstruction of security incidents. Our goal here is to learn from the cyberattack and refine your defenses. In addition, the findings of our digital forensics experts enable prosecution and help you make claims against cyber risk insurance companies.
- Malware analysis: As part of malware analysis, we investigate how malware works with the aim of gaining a comprehensive insight into how it works, understanding its potential impact on a system and identifying suitable measures to minimize and prevent future damage. Our malware analysts use both static and dynamic analysis as well as reverse engineering.
Company collaboration platforms are a popular gateway for attacks, which can be exploited by means of phishing and identity theft. This is where the Microsoft 365 Business Premium feature “Defender for Office 365” comes in to protect email, Exchange, Teams, SharePoint etc. against malware and phishing.
- Defender for Office 365: In Office 365, this provides enhanced protection against phishing, email fraud, ransomware and other threats to your collaboration tools. Artificial intelligence and automation are used to detect and stop cyberattacks, prioritize incidents and focus the response of our analysts in a targeted manner.
The MDR Complete Service offers companies of all sizes comprehensive protection and is based on the Microsoft 365 E5 security features coupled with services from SECUINFRA. The three most important points of attack “end device, e-mail and identity” are protectedin this module. In addition, the module offers enhanced protection by detecting anomalies in the network and securing SaaS applications against identity theft and data leakage. This provides you with comprehensive detection, analysis and response against cyber attacks and puts you in an excellent position in this area.
- Network Detection & Response (NDR): In addition to detecting access to the command-and-control infrastructure of known attackers, SECUINFRA offers behavior-based detection of attackers at the network level. A modern Network Detection & Response (NDR) system is used here which, in contrast to conventional products such as N-IDS, relies primarily on the detection of behavioral patterns. The data generated is not only extremely valuable for detecting attacks, but is also used by our analysts as part of the response process to contextualize suspicious events. In addition to attack detection and contextualization capabilities, our NDR also provides the ability to actively respond to detected attacks. For example, communication relationships can be terminated, access to command and control servers can be blocked, or IT systems can be isolated automatically to minimize the impact of detected security incidents.
- Defender for Identity: This security service specializes in protecting identities in your networks from hackers and thus preventing lateral movement. Local and cloud networks are monitored. Suspicious logins and user activities are detected, reported and stopped locally, in the Microsoft Active Directory and in Azure with Entra Identity Protection. Password resets and user lockouts are automated and performed quickly before systems and data are compromised.
- Defender for Cloud Apps: Cloud applications and services are monitored and evaluated according to risk factors. By analyzing information from various application sources, cyberattacks on cloud applications or data in the cloud are detected and effectively stopped. This provides all-round protection for yourcloud applications and prevents lateral movement from the cloud to yourinfrastructure.
The MDR Premium module offers companies of all sizes even greater protection and covers all Microsoft security products of the respective subscription, including the SIEM functionalities of Microsoft Sentinel. The service also offers flexibility in the retention period of the collected security-relevant data. The service is based on the features of Business Premium or Microsoft 365 E5 Security Features and is supported by the advanced detection capabilities of UEBA. Other services such as Defender for Cloud are also covered. This provides full protection for endpoints, collaboration (email & Teams), identities (AD and Azure Entra ID) and yourcloud infrastructure. This module alsooffers services such as cyber deception.
- Central log management: The database for the SIEM area is provided by our central log management. Security-relevant log data is recorded centrally and stored for a period of 90 days, or longer if required, in a searchable format.
- Security Information & Event Management Microsoft Sentinel SIEM is a scalable, cloud-native solution that provides security intelligence and event management, security orchestration, automation and response (SOAR), and intelligent security analytics and threat intelligence for organizations. With Microsoft Sentinel, data can be collected from various sources, interactive reports and workbooks createdalarms are correlated into incidents and tasks are automated.
- User and Entity Behavior Analytics (UEBA) detects and investigates suspicious activities. An entity can be a user, a device, an IP address or an application. Microsoft Sentinel collects and analyzes the data and creates a normal behavior profile for each entity. Various methods and machine learning are used to find abnormal activity that indicates a possible attack or compromise. These anomalies are presented in the form of warnings and incidents. In addition, sensitivity, behavioral profiles and criticality are shown. This allows analysts to quickly assess the priority and severity of the threat and initiate further investigations and remediation of the incident.
- Cyber deception: This technique deceives, confuses and exposes attackers who are trying to penetrate a computer system or network. For example, false or manipulated data or resources are created in the network, which serve as so-called honey pots, i.e. decoy traps. This is used to gather information about the attackers’ intentions and identities.
In addition to all MDR Premium features, the highest level offers the option of enriching the Sentinel SIEM with security-relevant data from your log sources via Microsoft Data Connectors. This has the advantage that this data and the data from the Defender modules can be correlated using additional use case rules and thus utilize the full Sentinel SIEM capabilities. Benefit from SECUINFRA’s extensive USE-CASE library, which has proven itself in numerous customer projects and is constantly being optimized by our experts. Third-party hardware and software, such as firewalls or proxy servers, etc., are also monitored to detect anomalies.
Anti Phishing: Companies are facing an increasing number of cyber attacks. Phishing is a special and very successful type of phishing. Around 90% of attacks on a company begin with a phishing e-mail. In order to cover this incidence vector comprehensively, we divide this AddOn module into two sub-modules. The sub-modules can also be ordered separately, but always require at least the Basic+ module.
- Phish button: This add-on module offers the possibility, to have suspicious emails checked by our analysts. For this purpose, the end user is given the option in Outlook to report each email as potentially suspicious. During this analysis, URLs, QR codes or attachments are checked for malware or phishing attempts. The advantage here is that every reported e-mail is processed and checked directly by an analyst. Suspect or malicious content is moved to quarantine and the notifier receives feedback on the analysis result.
- Phishing awareness campaign: This module is extremely effective in sensitizing employees to the various and sometimes perfidious phishing attacks. For a simulation, SECUINFRA, in consultation with the customer, creates a mail layout with the aim of requesting login data from the customer’s users or tricking users into performing security-critical actions. has. Only the user names are collected, actual Passwords are not collected by the phishing campaign. A simulation comprises one phishing e-mail per employee of a specific division or the entire company. A detailed procedure will be defined in close consultation after commissioning.
In order to make the campaign appear as authentic as possible, SECUINFRA (or the customer) registers a previously agreed domain.
A phishing simulation will run for a period of approx. 10 days in order to reach as many users as possible. The lead time for the start of a campaign is approx. 10 working days.
Once each simulation has been completed, the customer receives a report within 2 weeks. It is also possible to send awareness training to conspicuous users via the O365 Defender.
Vulnerability Management: This additional module can be added to any module. The service is based on the Microsoft Defender Vulnerability Management Plan. This additional module provides an overview of the current vulnerabilities of yoursystems, both inside and outside your environment. The vulnerabilities identified are also used to evaluate the alarms and possible incidents from the aforementioned modules.
Expert know-how for your safety
Our experts are on duty for you around the clock. All employees are proven experts in the detection, analysis and defense of cyber attacks. In addition to numerous Microsoft certifications, they also hold vendor-neutral certifications in the areas of threat detection, incident response, digital forensics and malware analysis.













The most important FAQ from the Managed Detection & Response area
MDR is a security service that optimizes threat detection and response. In the Microsoft context, MDR services leverage platforms such as Microsoft Sentinel, Microsoft Defender, and Azure to effectively monitor, analyze, and respond to security events.
MDR leverages Microsoft Sentinel for SIEM capabilities, Defender for endpoint protection, and Azure for cloud security to create a holistic monitoring and response system.
By integrating MDR with Microsoft tools, organizations can leverage advanced threat detection capabilities that seamlessly integrate with their existing Microsoft infrastructure.
MDR services using Microsoft technologies strictly adhere to Microsoft’s privacy policies and standards and supplement them with their own security protocols and best practices.
Yes, we offer the ability to extend and optimize existing deployments of Microsoft Defender, Sentinel or other Microsoft security tools. We recommend that you inquire directly with us about individual offers and packages.
The cost of an MDR service can vary depending on the size of the organization, the number of endpoints monitored, and specific requirements. We will be happy to advise you on the selection of the optimum license.
Our awards

Best SIEM consulting/service company in Europe

Market leader in Security Information Event Management (SIEM)

Leading provider of SIEM consulting services in Germany

TOP 10 SIEM consulting/service companies in Europe
That's why MDR from SECUINFRA!
Supported by automation and SOAR systems, our specialists quickly categorize, prioritize and triage security incidents. Depending on the agreement with the customer, we escalate the tickets to your employees or take over further processing ourselves.
Escalation and tracking of incidents as well as reporting and automation are our strengths. In the event of a security incident, we contact your specialist departments so that security incidents can be processed quickly and efficiently and further damage can be avoided.
We support you with critical security incidents through incident management, forensics and malware analysis. In addition, we assess your current security situation through threat hunting and integrate threat intelligence where appropriate. Malware infections and major security incidents are routine for our cyber defense analysts.
In order to be able to offer a stable service, all components of the MDR service are monitored at hardware and software level. This also includes the appliances installed at the customer's premises.
Against the backdrop of a constantly changing threat situation, the continuous development of our Managed Detection & Response Services is an integral part of our service. The detection mechanisms and response options are therefore being continuously developed for all customers of our service.
As a customer, you will be informed about these further developments as part of our regular service reviews and can also use this progress to prove compliance with compliance requirements (e.g. VAIT, BAIT, TISAX, ISO27001) or legal requirements such as KRITIS.
More informative blog posts and technical articles!
References in the area of Managed Detection & Response (MDR)
- SECURITY
SECUINFRA does not name clients or references publicly! Our customers’ desire for discretion always takes precedence over SECUINFRA’s marketing interests. - SUCCESS THROUGH RECOMMENDATION
Since 2010, we have focused exclusively on cyber attack detection, analysis and defense. Almost all customers have become aware of SECUINFRA through recommendations and have in turn recommended us to others. - REFERENZ AUF ANFRAGE
Bei berechtigtem Interesse stellen wir den Kontakt zu geeigneten Referenzkunden her.
Here you can get in touch with us!
Contact form end of page
Contact form at the bottom of the page
"*" indicates required fields
Our portfolio
©2024 SECUINFRA GmbH. All rights reserved.








