Incident Management
Incident Management
for your company
Incident management approaches
SECUINFRA enables its customers to choose the right approach to incident management in an ever-changing digital world. In times of growing challenges, SECUINFRA offers decisive, proactive and flexible strategies to respond effectively to security incidents. Our dedicated team of experts provides our clients with comprehensive incident management to protect their businesses from the impact of cyber threats. From our broad portfolio, our customers can select the service that best meets their individual requirements.
Whether our clients are already affected by a security incident and rely on SECUINFRA to respond effectively, or whether they opt for a proactive partnership to best prepare for potential incidents, we are there for our clients. Implementing proactive monitoring and response strategies strengthens companies’ resilience to cyber attacks and ensures the protection of sensitive data.
Our team works closely with our customers to ensure that their IT systems can be restored quickly and efficiently following a security incident. In this way, we minimize downtimes and protect your company’s assets. At SECUINFRA, the security of our customers is our top priority.
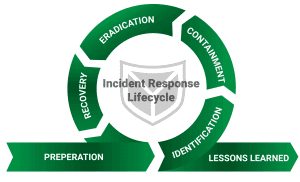
Incident Response
Have you been the victim of a cyberattack? We help you quickly and efficiently, around the clock, 365 days a year! Proper coordination and communication during a cyber attack prevents major damage.
Compromise Assessment
Detect compromised systems through Compromise Assessment before major damage occurs and increase your cyber resilience through Continuous Compromise Assessment.
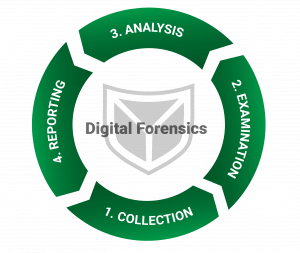
Digital Forensics
Use digital forensics techniques to understand exactly how the attacker got into the system and what they did.
Data Breach Assessment
Use the Data Breach Assessment to find out which of your access data has already been sold and what external attack surface your company offers.
Get in contact with us!
Contact form end of page
Contact form at the bottom of the page
"*" indicates required fields
Our portfolio
©2024 SECUINFRA GmbH. All rights reserved.







