Inhalt
Artificial intelligence is a much-discussed topic. It offers great opportunities, but obviously also harbors risks. And it also has two faces when it comes to IT security. This is because AI-based methods are suitable for both attacks and defense. However, it is undisputed that artificial intelligence will soon play a key role in cyber security.
What is the strength of AI?
In simple terms, artificial intelligence is designed to enable computers to learn and think like humans. From an IT security perspective, the sub-discipline of machine learning is particularly interesting. This makes it possible to develop processes that recognize patterns and regularities in data and establish correlations. This ability allows defense systems to develop a generalized understanding in order to make decisions or predictions. This gives us security experts a behavior-based view of the environment we are monitoring, which is particularly valuable in dynamic and complex threat scenarios. This is all the more true as the attackers logically also use AI methods.
How attackers can use AI
Artificial intelligence offers cyber criminals a wide range of applications to pursue their criminal activities. For example, offensive AI methods are suitable for phishing, malware or brute force attacks. With the help of underlying technologies, on which ChatGPT and other AI tools are based, phishing emails can be made even more personal and convincing. In combination with social engineering, certain users can also be targeted even more specifically and enticed to interact as desired. Numerous offensive AI methods have already been described in the specialist literature that use technologies such as Long-Short-Term Memory Networks (LSTM), Generative Adversarial Networks (GANs) or so-called transformers for different application scenarios.
More powerful malware and brute force attacks
Another attack method described in the specialist literature is AI-based malware. Even if the complexity of the malicious code is still manageable, the resulting increased risk potential is becoming apparent. This applies in particular to polymorphic malware, which changes its code with every attack and is therefore not detected by signature-based protection mechanisms. Experts are also expecting more effective brute force attacks that use intelligent test procedures to guess passwords more quickly. For example, self-learning algorithms and a password database from previous attacks are used to gain unauthorized access to networks and IT systems in a shorter time.
As can already be seen from these few examples, there is a general trend towards the increasing use of AI for attack purposes, whereby many known types of attack can also be carried out more effectively and efficiently by combining them with AI methods.
Offensive AI detects zero-day exploits
The threat situation could be further exacerbated by offensive AI technologies that pursue their goals more or less autonomously. Like a self-driving car that finds its own way from A to B, intelligent malware could move through the digital landscape in search of vulnerabilities. By not only reinterpreting the given data world, they could independently discover previously unknown security gaps, so-called zero-day exploits, and exploit them for criminal purposes. Companies must also be prepared for this heightened threat situation.
Defensive AI strategies as a countermeasure
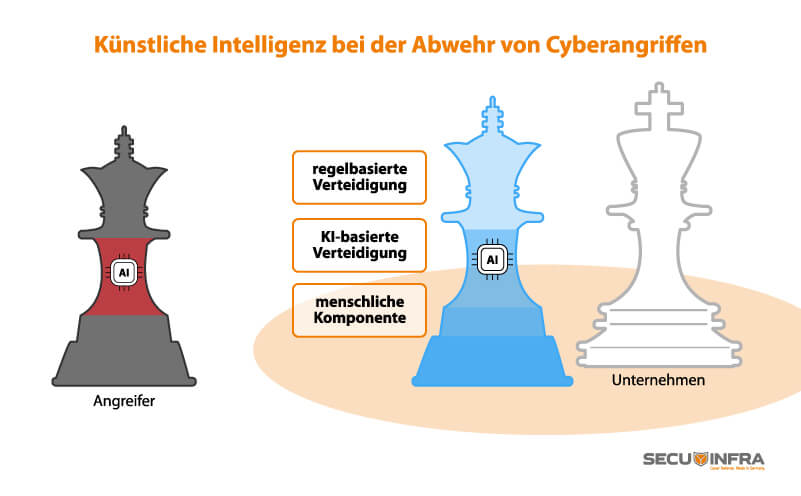
Given the new possibilities offered by AI and the huge threat dimension, it is clear that artificial intelligence will become increasingly important as a defensive tool to improve companies’ detection and defense capabilities. What’s more, sooner or later, defensive AI methods will prove to be the only alternative if our customers want to arm themselves against sophisticated attacks. Defensive AI methods are also based on the ability to recognize patterns and anomalies in large amounts of data and learn from them. With this support, however, we can not only detect phishing attempts more easily or address polymorphic malware. Rather, the constructive use of offensive AI methods opens up an exciting field of application for us. For example, to identify weak points in the infrastructure and eliminate associated risks at an early stage.
You can’t do without the human factor
Fortunately for us security experts, machine learning is well researched, so we can already add it to our toolbox today. Nevertheless, defensive AI is just one component in the overall toolkit with which we are countering the new threat situation with offensive AI. The fact that defensive AI procedures usually need to become even more precise so that they do not cause too many false alarms also plays a role here. Instead, effective protection requires the combination of AI with rule-based detection methods – and above all human expertise. Ultimately, experience and personal judgment determine whether a recognized event is actually an attack or not. AI can provide valuable interpretation clues, but without signature-based detection, well thought-out concepts and processes and the experience of analysts in the Security Operations Center (SOC), a security strategy would definitely fall short.
Conclusion: opportunity or challenge?
The answer to the question of whether AI is more beneficial or detrimental to IT security misses the point. AI has come to stay. While attackers are using advanced AI methods to refine their attacks, defensive AI technologies offer us new ways to effectively detect and combat these threats. The future standard in cyber defense will therefore be a comprehensive security approach with integrated AI technologies.
However, there is something important to consider first: Before a company can start building a new security standard with integrated AI methods, it should definitely have established transparency about its own infrastructure. A proven approach for this is to implement a Security Information and Event Management (SIEM) system. By consolidating events from a wide variety of data sources, the SIEM creates a valid database for defensive AI methods. Only then can behavioral patterns and regularities become visible in the holistic context of one’s own environment, so that the processes can form an overall picture and learn from it.