Inhalt
In this article about the dynamic world of cyber deception, you will learn how dangerous attackers can be made visible with little effort. Using an example implementation and its connection to a SIEM system, we also show how knowledge of previously unknown attacks and attack patterns can be incorporated into the defense and strengthen cyber resilience. But first a brief explanation of the term:
What is cyber deception?
Cyber deception is a proactive IT security strategy in which simulated targets are created to distract or generally deter attackers from important assets. The basic principle is based on the idea that attractive bait attracts the attention of attackers and directs their actions to specially prepared targets. As a supplementary component of MDR systems (Managed Detection & Response), Cyber Deception gives the defense a decisive time advantage. If the hacker falls for the diversionary maneuver, an alarm is triggered and the defense can react immediately.
Catching flies with honey
Two of the best-known core concepts of cyber deception are honeypots and honeytokens. While honeypots attract attackers as entire bait systems or networks, honeytokens consist of individual artifacts such as files, accounts or registry entries that trigger an alarm when accessed.
In contrast to other or conventional measures that are based purely on detection and defense using signatures, heuristics or similar, Cyber Deception attempts to proactively steer attackers into a controlled and monitored environment. In addition to the obvious advantages, this approach also offers the potential to gain valuable data for threat intelligence. Ultimately, cyber deception also serves to understand attackers and actively influence their decision-making cycle.
1.2 Understanding the psychology of the attacker
Attackers typically choose the path with the least resistance in order to capture as much value as possible. Cyber Deception exploits this way of thinking and presents the attackers with exactly what they want to see. As soon as the attacker has taken the bait, he can be further misled by more breadcrumbs. The aim is to tell a credible story that becomes more believable for the attacker with each subsequent step. But what if the attacker sees through the cyber deception trick? Studies show that even then, this is beneficial for the defenders of the systems, as the attackers often shy away or resort to slower and less effective attacks, giving the SOC team time to analyze and react.
1.3 Is there a catch?
Although Cyber Deception is a powerful defense strategy, it is not without its challenges. False positives can still occur and work must be done on the exact implementation of the selected techniques. In principle, it is clearly defined what is legitimate and what is malicious behavior. Nevertheless, it can occasionally happen that a curious employee accesses Cyber Deception resources by chance. Such situations must be considered in advance.
In addition, honeypots and honeytokens must be constantly maintained and adjusted. The story we want to tell an attacker must be as credible as possible. Otherwise there is a risk that the attacker, as with other detection methods, will find ways to circumvent them.
Example of an implementation
Like any cyber security measure, cyber deception requires well thought-out planning. Whether it is possible to convince the attacker of the authenticity of the deception depends on whether it is possible to present him with a clear and coherent story made up of different parts. Rash critics could now claim, with reference to Kerckhoff’s principle of “no security through obscurity”, that cyber deception does not create any real security. Such objections are not only a misinterpretation, but are simply irrelevant for us as defenders of the system. Kerckhoff’s principle may make sense for cryptosystems, but our concern is different. After all, any approach that distracts an attacker from his target and enables him to be discovered is valuable. The more we can encourage the attacker to act and prevent them from focusing on critical assets, the greater the chance of detecting them and preventing greater damage.
The theoretical structure of sustainable cyber deception is divided into eight steps, which are illustrated below using a simple example:
2.1 Define goals
The initial definition of strategic objectives is crucial to the success of cyber deception. Collecting malware samples for the threat intelligence team is just as much a part of this as diverting various attackers from critical systems. The strategic goals not only determine the next steps, but also the considerations based on them. During target definition, the illusion is still customizable and can be shaped and designed accordingly.
A medium-sized company will serve as an example to illustrate this. After extensive consultation, those responsible realized that many company processes depend on the availability and integrity of the Active Directory . The aim is therefore to increase the security of this system.
2.2 Defining desired reactions
Once the strategic objective has been determined, the psychology of the attacker is considered in order to actively influence their decision-making. The desired reactions of the attacker are defined based on the basic analysis of potential steps and actions. The central question is: “What should the attacker perceive and how should they react?”
In our example scenario, one possible reaction could be to direct the attacks more strongly towards the deception accounts. The company has identified two possible reactions: Case 1: The attacker fails on a fake account and continues his attacks on real accounts or Case 2: The attack on the fake account is successful.
It is important to note that neither scenario has a negative impact on IT security at this point in time, but does provide an advantage for the defense: The more time the attacker spends with a deception account, the greater the chance that he will be discovered. Nevertheless, it is clear that the company does not want the attacker to succeed.
2.3 Identifying attacker bias
The principle of cyber deception is largely based on the fact that attackers are also subject to human characteristics and associated biases that influence their actions. This human factor and its weaknesses are exploited. The different types of bias can be of a personal, emotional, corporate/cultural or cognitive nature. Personal biases are particularly specific and therefore effective, while cognitive biases are more general and therefore less effective. However, since personal information about attackers is rarely available for targeted exploitation, operational or cultural biases are often the most viable tools.
In principle, the cognitive confirmation bias, often also referred to in this context as operational confirmation bias, is also suitable. This occurs when we unconsciously value information more highly if it supports our existing point of view. One way to use the confirmation bias against the attacker is, for example, to give accounts attractive names that suggest an easy target to the attacker. For example, by adding prefixes or suffixes such as “test” or “dev” to an account. This suggests that these accounts have rather insecure passwords and are easy prey.
2.4 Define deception
In this step, we define as precisely as possible how our deception should be designed based on our previous findings. To do this, we first look at the components of computer systems that can be used for the integration of cyber deception (Fig. 1). We then look at the factors that shape the deception strategy (Fig. 2).
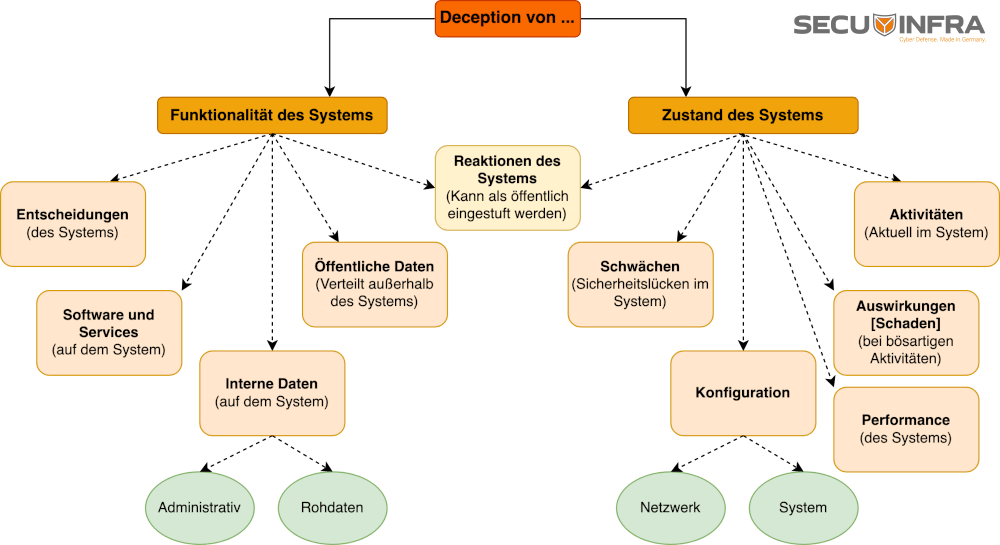
Figure 1: Computer system components suitable for cyber deception.
There are two main ways to deceive a computer system: one is via its functionality, the other via its state. Building on the previous steps, we will now develop our deception story with the help of these components. This phase requires a high degree of individuality and adaptation to the specific circumstances of the company and the environment in which the deception strategy is implemented.
For the example company that wants to supplement its security strategy with cyber deception, it makes sense to simulate a state of the system that is attractive to the attacker based on the previous considerations. Deception accounts are therefore designed in such a way that they appear to be easy targets.
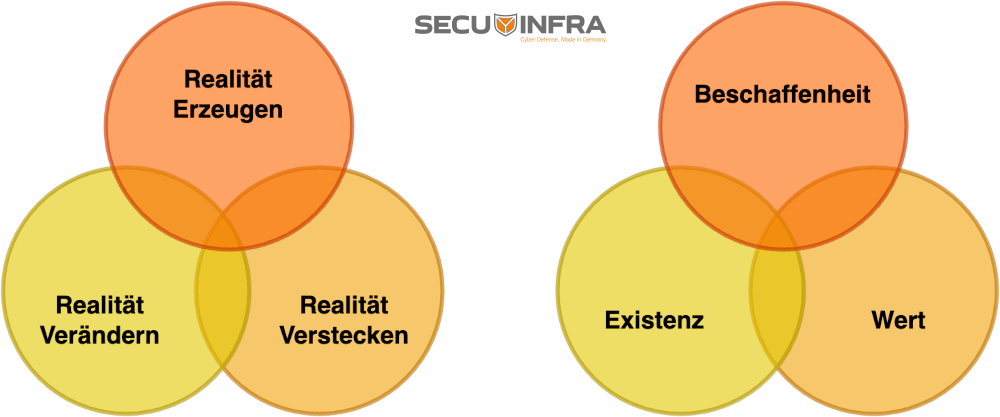
Figure 2: Ways in which attackers can be deceived and which aspects can be manipulated for this purpose.
Figure 2 on the left shows how we can shape reality in our favor by partially concealing, changing or creating it. The right-hand side comprises more general aspects that we can also manipulate, in particular the nature and effect as well as the existence and value of information or systems. Of course, there are overlaps in all areas that we can use to make our deception strategy even more credible.
In our example scenario, we change the area of existence by creating new accounts. At the same time, we try to increase the impact and value of these accounts for potential attackers by assigning them specific names and roles.
2.5 Set up monitoring
In order to be able to recognize attacks, effective monitoring is crucial in addition to well thought-out deception. In this case, the sources of deception are connected to the existing SIEM system. From a technical point of view, there are various ways of achieving this. Ultimately, however, it is important that the deception assets generate logs and that corresponding rules are created in the SIEM system . In order to integrate Deception seamlessly into the existing environment, it is important that the type of monitoring does not differ significantly from other monitoring methods.
2.6 Risk analysis
The introduction of new systems into an environment inevitably brings with it new risks that are either already known or need to be identified and dealt with before implementation. Ideally, there are already established risk management processes in place. Otherwise, now is the time to look into it independently of Cyber Deception.
The particular risks associated with the use of cyber deception include the danger of attackers taking over the systems and using them for their malicious intentions, as well as the potential negative impact on regular users in the IT landscape. However, this risk should also be seen as an opportunity: Because if attackers focus their attention on the decoy systems, the damage caused is likely to be less than if they attack the production systems.
The second risk concerns the detection possibilities: If a normal user in the IT landscape is influenced in any way by cyber deception, the probability of false positives increases. A typical user should therefore ideally not come into contact with the deception unless they are acting outside their normal area of responsibility or with malicious intent.
2.7 Implementing deception
With an elaborate plan and all the previous considerations in mind, the next step is to integrate Cyber-Deception into our environment. It is important to consider the capabilities of the attacker and to focus strongly on the context of the company. This is to ensure that the deception strategy is seamlessly embedded in the overall landscape and that a potential attacker cannot distinguish the deception from the normal assets. Deception should not be isolated, but should be integrated as deeply as possible into the IT infrastructure.
In the example company, the planned deception accounts are therefore set up and the Windows log sources are connected to the existing SIEM system. Use cases for the detection of malicious activities are being developed. In the event of a successful login to the deception accounts, automated SOAR rules are created to block the attacker.
This example shows that cyber deception does not necessarily require a large stack of different cyber defense technologies. The company could just as well have a PowerShell script executed when logging in, which sends an email to the SOC or triggers a webhook, for example. Of course, a large technology stack offers advantages, but a good strategy is much more important.
2.8 Evaluate strategy
In the final step, the cyber deception strategy is evaluated, with a particular focus on its effectiveness. Are there too many false positives? Are alarms generated at all? Is the maintenance effort too high? All these questions need to be answered and the answers can have different effects. For example, the absence of alarms can mean that no attacks have taken place. However, it can also mean that the detection is ineffective or that the deception is too easy to recognize as such.
At this point, it makes sense to initiate a continuous improvement process. For example, the findings from monitoring can be used to identify potential new areas for the use of cyber deception in order to gradually protect the environment even better against attackers and further develop the strategy.
Conclusion
Used correctly, Cyber Deception can be an extremely effective weapon against attackers of all kinds and give us a decisive advantage in the constant battle between attackers and defenders. However, it should be noted that cyber deception should not be viewed in isolation, but rather as a useful addition to standard security measures such as EDR, NDR, patch management, SIEM or compromise assessment.
In such a combination or as an integrated component in a comprehensive MDR solution, Cyber Deception can make a decisive contribution to sustainably increasing cyber resilience.
Do you want to set up your cyber defense effectively and flexibly? Discover the various options for Managed Detection & Response now.










