SIEM
SIEM
Security Information and Event Management (SIEM)
SIEM (Security Information and Event Management) is one of the central components of a SOC (Security Operation Center). It collects event log data from various sources such as operating systems, network components, applications and IT security tools at a central location and evaluates this automatically based on predefined rules (SIEM use cases). Depending on the data collected and the defined use cases, cyber attacks and compliance breaches can be detected almost in real time with the help of a SIEM.
SIEM is much more than a product.
In our view, SIEM is much more than just a product.
A SIEM product supports cyber defense analysts in detecting cyber attacks and compliance violations. A SIEM is useless without cyber defense analysts!
Conversely, it is essential both to feed the right data into a SIEM system and to ask the right questions of this data (SIEM use cases). If this does not happen, your SIEM will not detect cyber attacks or compliance breaches.
Our aim is for you to generate added value from your SIEM.
SECUINFRA does not simply sell you a product. We provide you with comprehensive support in the area of SIEM:
- Initial consultation on SIEM and SOC
- Creation of a SIEM concept as the basis for all further steps
- Support with product selection
- Implementation of the SIEM product in your infrastructure
- Selecting and connecting the right data sources to the SIEM
- Configuration of data sources so that the right data ends up in the SIEM
- Implementation and fine-tuning of the rules in the SIEM adapted to your needs
- Operational support and continuous further development and optimization of your SIEM
Areas
SIEM Consulting
Avoid mistakes and save time and money. Rely on the leading SIEM experts right from the start. We have specialized in SIEM since our foundation in 2010 and have more than 30 permanently employed SIEM experts.
SIEM concept
Our SIEM concept forms the basis for rapid implementation and smooth operation. It has already proven itself with many customers and has been continuously developed over the years. We customize it to your individual needs.
SIEM product
We are familiar with all common SIEM products and their respective advantages and disadvantages. As we specialize in the provision of services, we always act neutrally and in your best interests when it comes to choosing the best SIEM product.
SIEM integration
During the integration phase, we not only integrate the SIEM product into your infrastructure, but also the necessary use cases and log sources into your SIEM product and the necessary processes into your company.
SIEM use case library
Save time and money when creating SIEM use cases and log policies. Access our use case library with runbooks and test cases, which has been growing steadily since 2010 and will be based on MITRE ATT@CK from 2019.
SIEM operational support
Our co-managed SIEM approach provides you with support exactly where you need it – flexible, hybrid and, above all, transparent! The data and use cases belong to you and always stay with you.
The most important FAQs from the SIEM area
SIEM stands for Security Information and Event Management. It is a comprehensive IT security solution that supports companies in protecting their networks and systems against threats.
SIEM systems collect and analyze data from various sources such as firewalls, intrusion detection systems, antivirus programs and log files to detect and respond to potential security incidents. The information collected is analyzed in real time and correlations between different events are established in order to detect possible attacks or security breaches at an early stage.
A SIEM system enables companies to obtain a central overview of their security situation. It identifies unusual behavior, recognizes known attack patterns and warns of potential security risks. It also enables the forensic investigation of security incidents in order to determine causes, assess effects and take appropriate countermeasures.
The basic functional principle of SIEM is to collect data from various sources such as log files, network devices, hosts and applications. This data is analyzed by SIEM systems in real time or at regular intervals. By analyzing the data, patterns, anomalies and potential security incidents can be identified.
SIEM systems use various techniques to process data and detect threats. This includes the correlation of events, the application of rules and algorithms and the use of threat intelligence information. By combining these techniques, SIEM systems can identify suspicious activity and generate alerts that indicate potential security incidents.
Another important aspect of SIEM is the ability to collect and categorize events in order to obtain a comprehensive overview of the company’s security situation. This allows security teams to recognize trends, identify potential vulnerabilities and take proactive measures to close security gaps.
SIEM (Security Information and Event Management) offers many advantages when it comes to the security of company networks and data. Here are some of the key benefits of SIEM:
- Real-time monitoring: SIEM enables real-time monitoring of networks, systems and applications. It continuously collects and analyzes security events and data in order to detect potential threats at an early stage. In this way, security incidents can be detected immediately and appropriate countermeasures initiated.
- Threat detection: SIEM aggregates and correlates security events from various sources and analyzes them using sophisticated algorithms. This allows patterns and anomalies to be identified that indicate potential threats. SIEM helps to detect unauthorized access, malware infections, insider threats and other security risks.
- Incident Response: SIEM supports effective incident response by providing a centralized platform for managing security incidents. It enables a rapid response to security incidents by enforcing automated alerts, escalation procedures and policies. This shortens the response time and minimizes the impact of security breaches.
- Compliance and reporting: SIEM helps companies to meet compliance requirements and simplify reporting processes. By centrally collecting and analyzing security data, SIEM can create audit trails, monitor security policies and generate reports needed for internal and external audits.
- Security analysis and optimization: SIEM provides a comprehensive insight into the company’s security situation. It enables security data to be analyzed, vulnerabilities to be identified and the security infrastructure to be improved. Through continuous monitoring and analysis, companies can optimize their security strategies and react proactively to new threats.
In summary, SIEM offers an effective way of increasing the security of company networks and data. It improves threat detection, shortens response times, promotes compliance and enables continuous security analysis and optimization. By using SIEM, companies can raise their security measures to a higher level and respond better to the constantly growing threat landscape.
A SIEM (Security Information and Event Management) system is a powerful tool used in the field of IT security to monitor a company’s security situation, detect threats and respond to them. It combines the functions of Security Information Management (SIM) and Security Event Management (SEM) and provides a central platform for aggregating, correlating and analyzing security events and information from various sources.
The main functions of a SIEM system are
- Event monitoring and correlation: The SIEM system collects and analyzes information from various sources such as security logs, network devices, operating systems and applications. It identifies and correlates events in order to detect attacks or suspicious activities. By combining various data sources, it can provide a comprehensive picture of the security situation.
- Warning and notification: The SIEM system generates alerts and notifications when potentially harmful activities are detected. This enables security teams to react quickly to incidents and take appropriate measures to ward off attacks or eliminate vulnerabilities.
- Logging and storage of security data: A SIEM system collects and stores logs and security data over a certain period of time. This enables a comprehensive review of past events and facilitates forensic analysis in the event of threats or security breaches.
- Compliance management: SIEM systems support companies in adhering to compliance guidelines and regulations. They offer reporting functions that make it easier to prove compliance with regulations such as GDPR, PCI-DSS or HIPAA. The system can generate audit logs and reports that are useful for checking and verifying the company’s security measures.
- Incident response and forensics: In the event of a security incident, a SIEM system enables the security teams to respond quickly. It facilitates the investigation of security breaches by providing a comprehensive data history and analysis tools to determine the origin of the attack and take appropriate measures to restore security.
Overall, a SIEM system plays a crucial role in monitoring and improving a company’s security posture by providing the ability to detect threats early, respond to them and continuously optimize security measures.
There are a large number of SIEM (Security Information and Event Management) solutions on the market that help companies to monitor their IT infrastructure, detect security incidents and respond to them. Here are some of the best-known SIEM solutions currently on the market:
- IBM QRadar: A comprehensive SIEM platform that provides comprehensive data analysis, correlation of security events and a user-friendly dashboard. IBM QRadar also supports the exchange of threat information and offers integrations with various security tools.
- Splunk Enterprise Security: Splunk is a leading platform for machine learning and data analysis. Splunk Enterprise Security offers comprehensive SIEM functions such as real-time monitoring, event correlation and forensic investigations.
- LogRhythm: LogRhythm is a holistic SIEM solution that combines advanced analytics, behavioral analysis and threat intelligence. The platform also offers functions such as the automation of security processes and compliance reporting.
- McAfee Enterprise Security Manager: This SIEM solution from McAfee offers real-time monitoring, event correlation and threat intelligence. It enables the rapid detection of security incidents and supports the response and elimination of threats.
- Elastic SIEM: Elastic SIEM is an open source SIEM solution based on the Elastic Stack platform. It offers scalable and flexible monitoring of security events, comprehensive analyses and dashboards for visualizing security data.
- Microsoft: One of the strengths of Microsoft’s SIEM solution is its integration with other Microsoft products such as Azure Sentinel, Azure Active Directory and Office 365. This enables seamless data transfer and effective collaboration between different security solutions to ensure a comprehensive and proactive security strategy.
- ArcSight: A central feature of the ArcSight SIEM solution is the advanced correlation function. It enables the linking of security events from various sources in order to obtain a comprehensive picture of the security situation. By analyzing log data, network traffic and other relevant information, the solution can detect attack patterns, uncover suspicious activity and proactively defend against threats.
This list is not exhaustive, as the market is constantly evolving and new SIEM tools & solutions may come onto the market. Companies should consider their specific requirements and budgets in order to select the SIEM solution that best suits their needs. Our product experience with all current providers makes your selection easier. We provide you with comprehensive advice!
Choosing the right SIEM (Security Information and Event Management) system is an important step in effectively monitoring and improving the security situation in an organization. Here are some steps that can be helpful when choosing the right SIEM system:
- Requirements analysis: Start with a thorough analysis of your organization’s requirements. Think about what kind of security information and events you want to monitor, what compliance requirements you need to fulfill and what specific functions you need, such as log collection, event correlation, threat detection, etc.
- Scalability and flexibility: Take into account the size of your organization and future growth. Make sure that the SIEM system is scalable and can grow with your requirements. It should also be flexible enough to adapt to new threats and technologies.
- Integration: Check how well the SIEM system can be integrated into your existing security solutions. It should work seamlessly with other tools such as firewalls, intrusion detection systems (IDS), antivirus programs, etc. to provide a comprehensive security picture.
- Ease of use: Test the SIEM system’s user interface to ensure it is intuitive and user-friendly. Employees should be able to easily monitor events, create reports and effectively investigate threats without having to undergo extensive training.
- Performance and speed: Check how efficiently the SIEM system collects and analyzes data and reports events. It should be able to process large volumes of logs in real time in order to quickly detect and respond to threats.
- Support and maintenance: Check the SIEM provider’s support and maintenance services. Make sure that you have access to reliable support in the event of problems or questions and that regular updates and patches are available for the system.
- Costs: Consider the costs for the implementation and ongoing operation of the SIEM system. Compare different offers and make sure that the system you choose offers good value for money and fits your budget.
By conducting a thorough requirements analysis, evaluating features and weighing costs, you can find the SIEM system that best meets your organization’s security needs. It is important to invest time and resources in choosing the right SIEM system, as it can make a significant contribution to improving your cyber security.
The implementation of a SIEM (Security Information and Event Management) system requires careful planning and a structured approach. Here are the basic steps for implementing a SIEM system:
- Requirements analysis: Identify the specific requirements of your company. Consider factors such as size, type of infrastructure, compliance requirements and threat landscape.
- Select a suitable SIEM tool: Research different SIEM tools on the market and choose the one that best suits your needs. Consider functions such as event recording, correlation analysis, alerting, reporting and scalability.
- Architecture design: Develop a SIEM architecture that enables integration with existing systems and effective capture of security events. Define the network segmentation, data sources, log formats and the connection to the central SIEM server.
- Provision of the infrastructure: Setting up the necessary hardware, software and network infrastructure. Ensure that all required protocols are enabled on the relevant devices to capture security events.
- Data aggregation: Configure the SIEM system to collect data from various sources such as network devices, servers, firewalls, intrusion detection systems (IDS) and anti-virus solutions. Implement protocol collectors or agents to send the data to the SIEM system.
- Definition of rules and correlation rules: Create rules and correlation rules to identify suspicious activity and trigger alerts. Adjust these rules continuously to ensure a high level of accuracy when detecting threats.
- Alerting and response: Configure alarms to be notified immediately in the event of security-relevant incidents. Establish clear escalation procedures and define the action plan for responding to incidents.
- Monitoring and reporting: Continuously monitor the SIEM system to ensure that all relevant events are recorded. Create regular reports on security incidents, trends and vulnerabilities to gain a better understanding of the security situation.
- Training and maintenance: Training employees who work with and respond to the SIEM system is crucial. Ensure that the system is regularly maintained, including updates, patches and performance checks.
- Continuous improvement: The implementation of SIEM is a continuous process. Regularly analyze the effectiveness of the system, adjust the rules and optimize the configuration to further improve security.
Implementing a SIEM system requires time, resources and expertise. It is important to take a holistic approach and consider the specific requirements of the business to create an effective security monitoring system.
SIEM stands for Security Information and Event Management and is a technology that helps companies to monitor their security situation, detect threats and respond to them. Many companies use SIEM solutions to protect their IT infrastructure and prevent cyber attacks. Here are some examples of companies that use SIEM technology (also as a service, managed SIEM):
- Large financial institutions: Banks, insurance companies and other financial institutions rely heavily on security to protect their sensitive customer data and financial transactions. SIEM systems help them to detect and respond to potential security incidents in order to minimize financial losses.
- Government agencies: Government organizations at national and local levels have access to highly sensitive information and need to protect it from cyber attacks. SIEM technology helps them to monitor potential threats and detect attacks at an early stage.
- E-commerce companies: Companies in the e-commerce sector process large volumes of transactions and personal customer data. SIEM solutions help them to protect their systems and data to prevent fraud, data leaks or other security incidents.
- Healthcare: Hospitals, medical facilities and healthcare organizations process highly sensitive patient data and must comply with strict data protection regulations. SIEM helps them to detect anomalies in data traffic that could indicate possible data breaches.
- Technology companies: IT and technology companies are often the target of cyber attacks because they hold valuable intellectual property and customer information. SIEM systems offer them improved security monitoring and enable an effective response to security incidents.
It is important to note that SIEM is not limited to these specific industries and can be used by companies in different sectors. The decision to use SIEM depends on the individual security requirements and risk profiles of the company in question.
The implementation of a SIEM (Security Information and Event Management) system can be a complex process due to various challenges. Here are some of the most common challenges that can arise when implementing a SIEM system:
- Data integration: SIEM systems collect information from various sources such as logs, network devices and security solutions. The challenge is to integrate this data into the SIEM system and ensure that it is properly formatted and structured to provide meaningful information.
- Adaptation to the corporate environment: Every company has a unique IT infrastructure and specific security requirements. A SIEM system or SIEM tool must be adapted to these individual requirements in order to be effective. This requires a thorough analysis of the environment to ensure that the SIEM system supports the right protocols and generates the necessary alerts and notifications.
- Complex configuration: SIEM systems offer a wide range of configuration options for customizing alarms, rules and reports. Correct configuration requires expert knowledge of security events and threat landscapes in order to minimize false positives and avoid overlooking important incidents.
- Data quality and integrity: The accuracy and completeness of the data fed into the SIEM system is crucial to the effectiveness of the system. It must be ensured that the data sources are trustworthy and that the data is not lost or manipulated.
- Scalability and performance: SIEM systems must be able to process and analyze large volumes of data. The scalability of the system, both in terms of storage and processing capacity as well as performance, is crucial in order to keep pace with growing data traffic and the increasing number of security events.
- Skills shortage: SIEM systems require specific expertise to be implemented and managed effectively. Finding qualified security experts can be a challenge, as the market for such specialists is often scarce.
The successful implementation of a SIEM system requires careful planning, technical expertise and consideration of a company’s individual requirements. However, if these challenges are overcome, a SIEM system can be a valuable addition to monitoring and improving a company’s security situation.
SIEM, short for Security Information and Event Management, is a proven method for monitoring and analyzing security-relevant events in IT systems. It offers companies the opportunity to recognize potential threats and react to them. However, there are also alternative approaches and technologies that companies can consider to enhance their security strategies. Here are some alternatives to SIEM:
- User and Entity Behavior Analytics (UEBA): UEBA platforms analyze the behavior of users and entities such as devices or applications to identify anomalies and suspicious activities. By monitoring behavioral patterns and detecting deviations, they can identify potential threats at an early stage.
- Security Orchestration, Automation and Response (SOAR): SOAR platforms automate security processes and enable a rapid response to incidents. They integrate security solutions and tools to improve the efficiency of security teams and shorten response times.
- Threat Intelligence Platforms (TIP): TIPs collect and analyze information on current threats and security risks from various sources. They provide insights into the threat landscape and support companies in identifying and prioritizing potential threats.
- Endpoint Detection and Response (EDR): EDR solutions focus on monitoring and protecting endpoints such as laptops, desktops and servers. They record and analyze activities on the end devices in order to detect suspicious activities and malware.
- Network traffic analysis (NTA): NTA tools monitor network traffic and analyze data packets for unusual activities. They help to detect threats that can be overlooked by conventional security solutions.
These alternatives to SIEM offer companies additional opportunities to expand their security strategies and combat potential threats. Depending on a company’s specific requirements and resources, it may make sense to consider one or more of these technologies in order to increase the effectiveness of security measures.
The cloud plays a crucial role in a SIEM solution as it enables scalability, efficiency, cost savings and better collaboration. Companies can benefit from a cloud-based SIEM solution to strengthen their security infrastructure and effectively combat threats. Here are some of the most important aspects:
- Scalability: A cloud-based SIEM solution enables companies to adapt their resources as required. The cloud offers elastic resources so that the capacity of the SIEM system can be flexibly scaled as required. This is particularly useful for coping with sudden load peaks or data growth without bottlenecks or performance losses.
- Data aggregation: SIEM solutions need to collect and analyze large amounts of security data from different sources. The cloud makes it possible to collect this data quickly and efficiently, as it has an extensive network of data centers. This ensures efficient aggregation and analysis of security events from different sources, regardless of their location.
- Cost optimization: Cloud-based SIEM solutions usually offer a pay-as-you-go model, where companies only pay for the resources they actually use. This eliminates high investment costs for hardware and infrastructure. Companies can scale their SIEM solution as required and use resources efficiently, resulting in an optimized cost structure.
- Automation and updates: By using a cloud-based SIEM solution, companies benefit from automatic updates and patches. Cloud providers are responsible for updating the infrastructure and applications, which reduces the administrative burden for companies. In addition, the cloud enables the integration of machine learning and artificial intelligence algorithms to automate security tasks and detect threats in real time.
- Accessibility and collaboration: A cloud-based SIEM solution enables access to security information and events from different locations. This allows security teams to collaborate across sites and analyze and respond to threats in real time. The cloud also offers the possibility of securely exchanging security information with external partners and service providers.
We make your SIEM successful!
SIEM solutions ensure comprehensive monitoring of IT systems, networks and applications in order to detect and respond to threats. Security events are collected, correlated and analyzed in order to detect threats at an early stage and initiate appropriate countermeasures.
Planning, implementing, operating and optimizing a SIEM solution requires a deep understanding of the company’s technical and organizational requirements and business processes. Careful planning, professional implementation and continuous improvement of SIEM are essential to ensure an effective and efficient IT security strategy in companies.
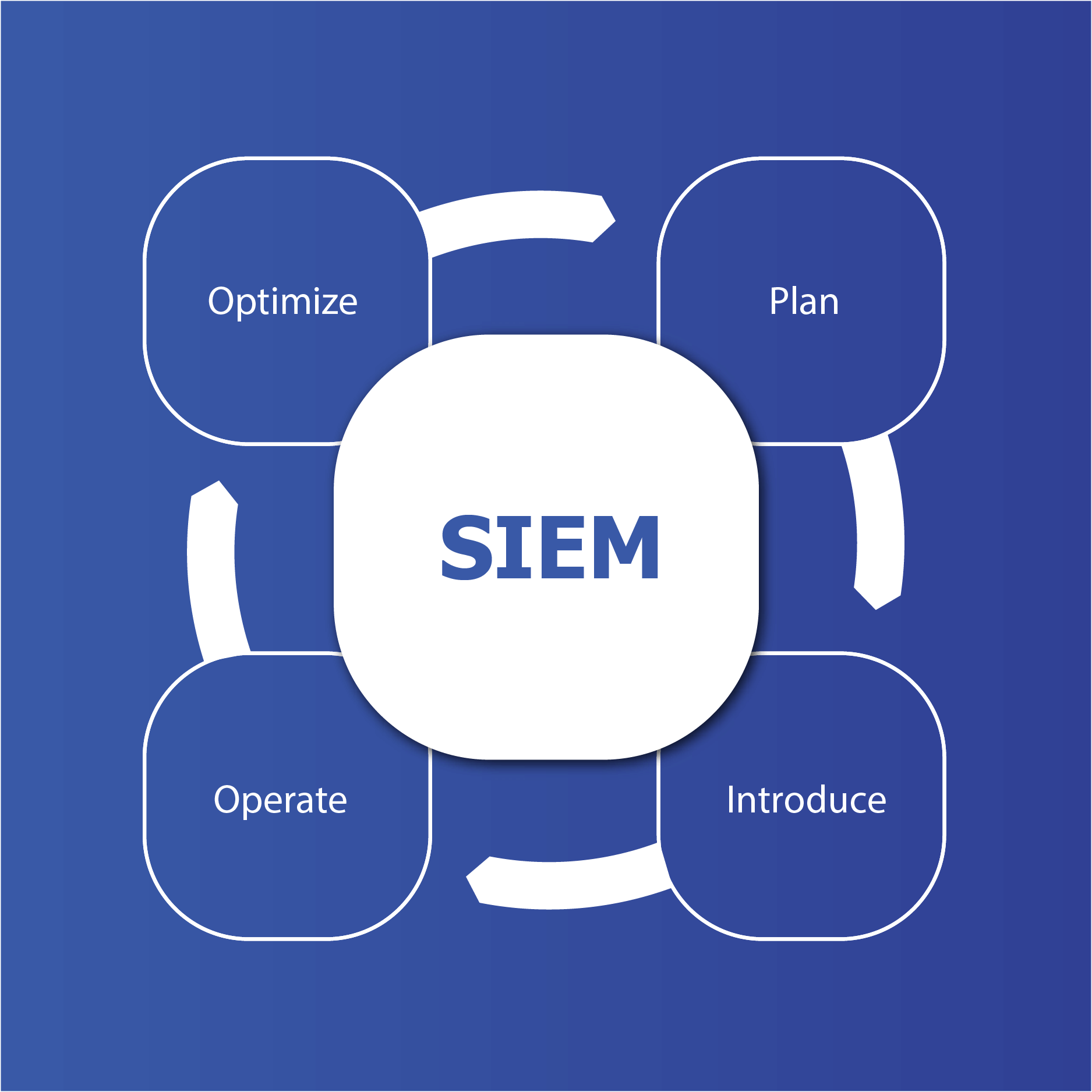
Planning a SIEM solution requires a careful analysis of the company’s business and security requirements as well as detailed knowledge of the technical requirements and limitations. Solid planning forms the basis for a successful implementation and optimal performance of the SIEM solution.
The most important aspects that should be considered when planning a SIEM solution are as follows:
- Business and compliance requirements
- Requirements for data collection
- Requirements for data storage
- Integration of data sources
- Definition of alarms and notifications
- Planning training courses for the responsible IT security team
Implementing a SIEM requires careful planning and preparation to ensure that the solution works effectively and efficiently. Among other things, it must be ensured that the necessary infrastructure is in place to support the SIEM solution, including sufficient server capacity, network bandwidth and storage space. In addition, all required data sources must be configured correctly and the data recorded correctly. Clear and meaningful alerts and notifications need to be configured to ensure that threats can be detected and responded to quickly.
Use cases are of particular importance when setting up a SIEM. You define various attack detection logics. When implemented in a SIEM solution, they help to detect actual attacks on the monitored IT infrastructure. Developing economical and effective use cases is a complex task that requires in-depth expert knowledge.
Among other things, continuous monitoring is essential for the successful operation of a SIEM solution. Monitoring helps to identify and rectify problems at an early stage. Regular audits of the SIEM solution also ensure that it meets the company’s current security requirements and works efficiently. Audits can also help to identify and eliminate weaknesses.
In addition, regular software updates, monitoring of system logs and regular backups are essential. The SIEM solution should also be continuously adapted to new threats (SIEM use case development).
Continuous optimization of the SIEM solution ensures, among other things, that it meets current security requirements and that alarms and notifications are configured correctly to avoid false alarms. Optimizing the data sources can help to improve the accuracy of the SIEM solution.
Successful optimization also requires close cooperation with other departments as well as regular training and awareness-raising for employees.
That's why SECUINFRA
- Sustainability
We are familiar with all common SIEM products and will only recommend the SIEM products with which we have had the best experience during our more than 28,000 SIEM consulting days since 2010.
- Fully comprehensive
You don’t just get a SIEM product from us. We accompany you through the entire SIEM life cycle, from the initial SIEM concept to long-term support in the operation of your SIEM through our co-managed SIEM approach.
- Experience
SECUINFRA has focused on SIEM since 2010. In more than 150 successfully implemented SIEM projects, our 30+ permanently employed SIEM experts have been able to help numerous customers and gain extensive experience.
- Use cases library
Take advantage of our globally unique SIEM use cases library. In addition to the SIEM rules, each use case also contains clear instructions for data generation, run books for handling alarms and test routines.
- Delivery capability
With a team of over 30 permanently employed SIEM experts, we have the most powerful SIEM expert team in Germany and can also implement large SIEM projects quickly, efficiently and professionally.
More informative blog posts and technical articles!
Here you can get in touch with us!
Contact form end of page
Contact form at the bottom of the page
"*" indicates required fields
Our portfolio
©2024 SECUINFRA GmbH. All rights reserved.