SOAR
SOAR
Security Orchestration Automation and Response (SOAR)
SOAR systems offer you a platform to efficiently process incoming alarms from various IT security systems. To this end, they bring together all the relevant information in the company that is required to process an IT security incident.
By introducing a SOAR system, we sustainably improve your security process and strengthen the reproducibility and quality of the analysis work.
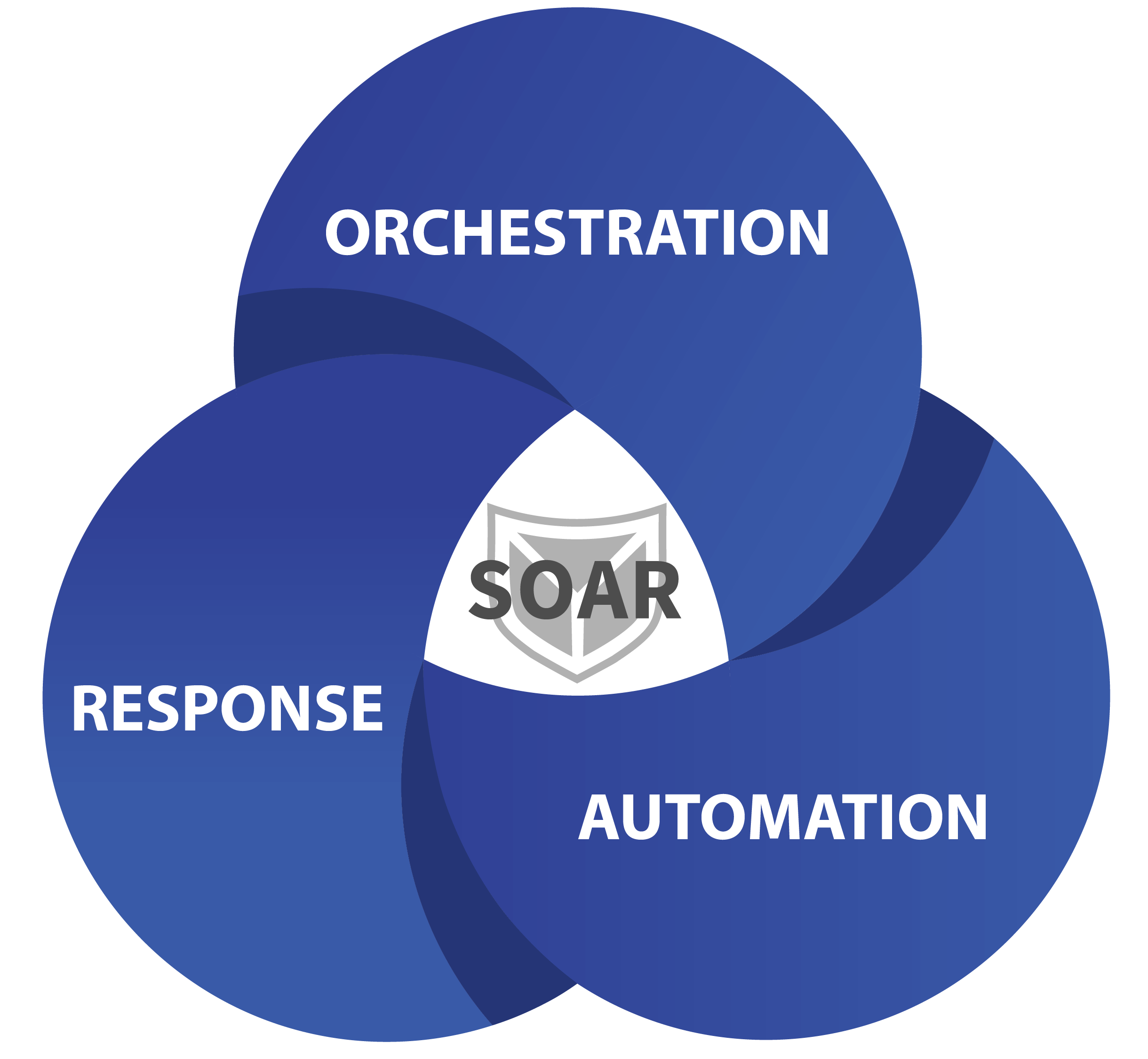
Orchestration
Connect all systems to your SOAR that can initially detect a potential IT security incident, provide further information for assessment or initiate protective measures.
Automation
Automatically correlate incoming alarms from different data sources to avoid duplicates. Automate recurring tasks for fast and efficient analysis.
Response
React automatically to alarm messages through connected components such as firewalls and EDR systems and thus ensure that countermeasures are implemented quickly in the event of a threat.
SOAR supports the analysis
SOAR automates the analysis and response process following a security alarm.
Without SOAR
Time-consuming information gathering and reaction
Without a SOAR system, incoming security alarms have to be contextualized and evaluated with additional information in a time-consuming process. In addition, a subsequent manual response is required to minimize the impact of the security incident.
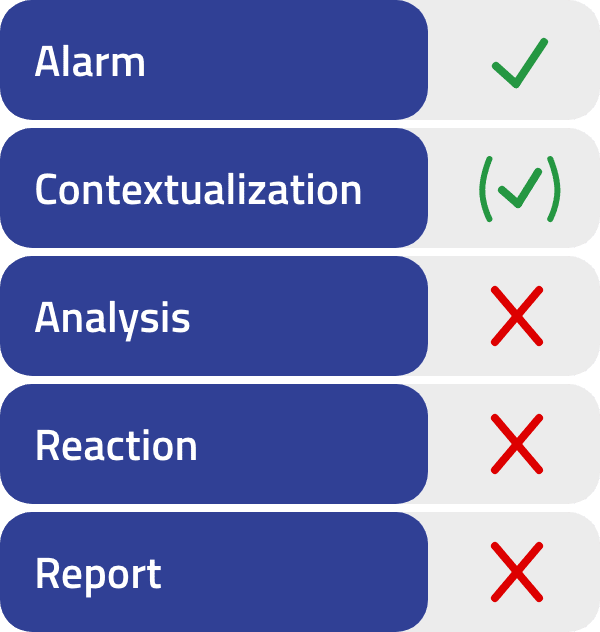
With SOAR
Automatic contextualization and response
A SOAR system automatically enriches emerging security alarms with further information and carries out initial countermeasures. A security analyst immediately receives all relevant information and can quickly and efficiently initiate further measures.

The most important FAQs from the SOAR area
SOAR (Security Orchestration, Automation and Response) is a combination of compatible programs that enables a company to collect data on security threats from a wide variety of sources.
Security Orchestration, Automation and Response (SOAR) systems provide a platform for efficiently processing incoming alarms from various IT security systems within the company. To this end, they bring together all the relevant information in the company that is required to process a potential IT security incident. The tools also offer the option of reacting automatically to alarm messages and initiating appropriate protective measures. A SOAR supports security analysts in threat and vulnerability management, the incident response process and the automation of various security-related processes.
The SOAR integrated in the company is, alongside a SIEM, the central tool for processing potential security incidents as part of the incident response process. To this end, it brings together all the security tools used in the company on a single platform, combines the available information and supports the collaboration of several analysts on a single case. It also serves to document past events.
- Central connection of all security tools
- Automatic (pre-)processing of incoming security alarms
- Display of all relevant information at a glance
- Simple collaboration between analysts and cases
- Automatic response to confirmed incidents
- Continuous documentation of all events
We have experience with many leading SOAR manufacturers.
SECUINFRA also has strategic partnerships with Swimlane and Palo Alto Networks to get the most out of SOAR*.
The SOAR system specifically supports the work of security analysts, but cannot replace it. A SOAR system automates recurring tasks, aggregates alarms of one alarm type or reacts to threats with specific measures. A SOAR also helps to implement efficient working methods by bringing together all security-relevant systems, information and people on one platform.
NO. A SIEM system is responsible for the initial detection of potential security incidents. After the initial alert from the SIEM system, it is the security analyst’s job to contextualize it and assess the threat to the company. If the alarm turns out to be a concrete threat, it is necessary to react accordingly as part of the incident response process and take appropriate protective measures.
A SOAR supports the security analyst in all work steps after the initial alarm. This includes the automation of recurring analysis steps, the central control of various security tools and the continuous documentation of all steps carried out and their results.
More and more companies want to improve their security process with a SOAR – but this is difficult or even impossible, especially with small budgets or a lack of in-house IT security experts. SECUINFRA gives you the opportunity to realize your individual SOAR according to the modular principle. Our experts work with you to plan the implementation and optimization of various analysis scenarios and automations.
SOAR areas
SOAR Consulting
SECUINFRA can look back on many years of experience in the field of cyber defense and security incident analysis. The know-how gained flows into every new project.
Co-Managed SOAR
Our co-managed SOAR approach supports you exactly where you need support – flexible, hybrid and, above all, transparent.
SOAR Playbook Library
Save money and time when creating SOAR playbooks. Take advantage of our constantly growing playbook library.
Where the SOAR system does the work
The correct use of SIEM and SOAR using the example of the incident response process.
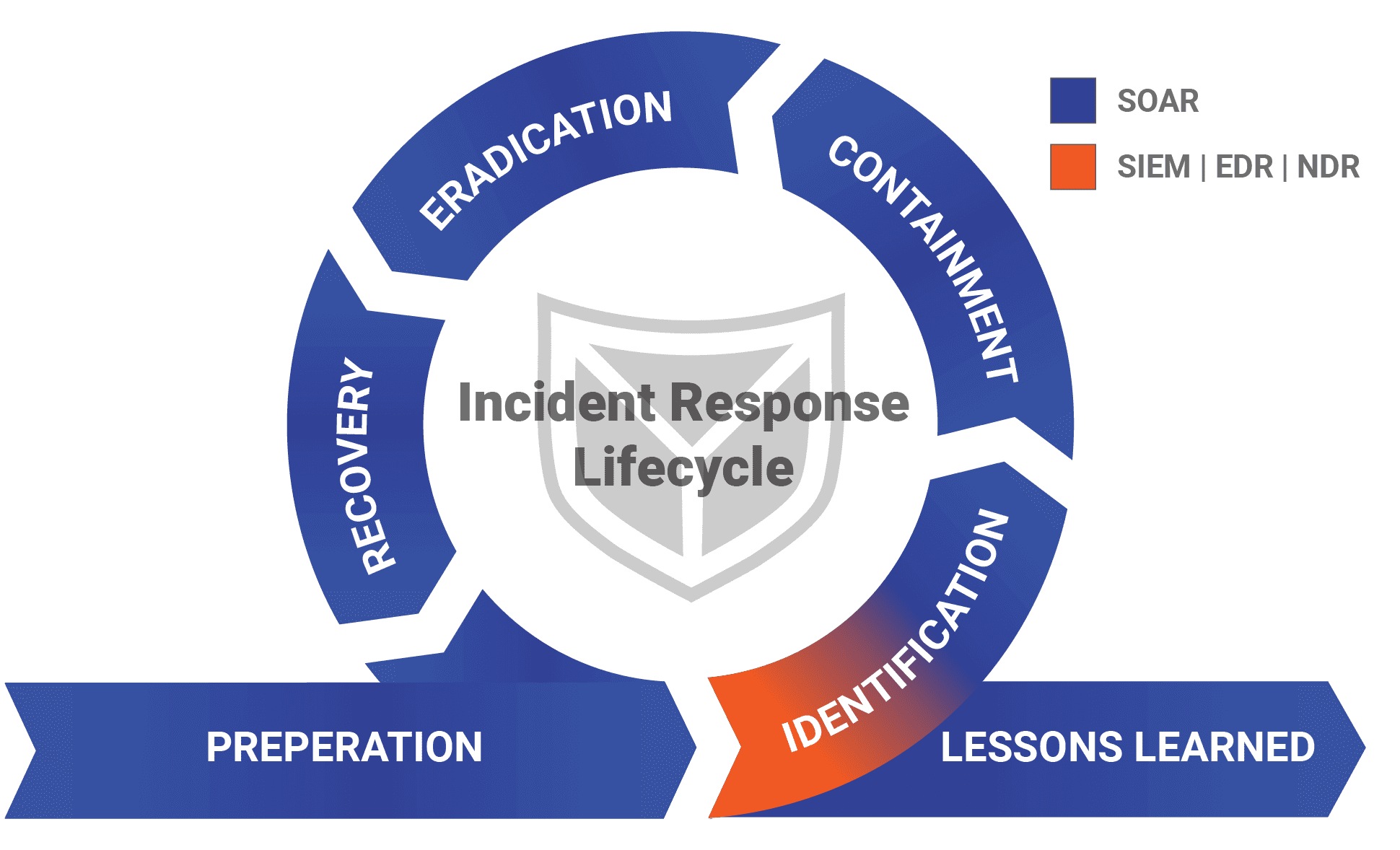
The SOAR system strengthens security in the company even before a security incident occurs. Thanks to the connection to all relevant security systems, software statuses can be monitored for up-to-dateness or threat intelligence information.
The SOAR also contains all the playbooks required to automatically respond to the alarm and initiate initial measures in the event of an incident.
The detection of a potential IT security incident is divided into different areas. These include alerts from the SIEM system, the endpoint or network detection and response solution or employees who report a phishing email.
The analysis process can also be triggered by threat hunting findings or information from threat intelligence sources.
After the initial alarm, this must be assessed by further information and the correlation of various events. The SOAR system provides support here and automatically provides all relevant information. In addition, accumulated alarms can be summarized or de-duplicated. The information collected also enables the SOAR to assess alarms and, if necessary, identify them as false positives before an analyst has to invest any work.
In the containment phase, the SOAR system initiates individual initial measures based on the information previously obtained in order to minimize potential damage. This includes, for example, the isolation of a host system or the blocking of user accounts.
In addition, the SOAR enables an analyst to control all security tools centrally and provides a precise overview of the current steps.
The SOAR system also enables the connection of a ticketing system or the sending of e-mails to inform other people about the incident.
In addition, continuous documentation of all incidents takes place throughout the entire incident response process.
Once the analysis work has been completed, the SOAR system offers the option of automatically or manually reversing the containment measures taken. Furthermore, passwords can be reset if required, e.g. through connections to Active Directory.
All collected Indicators of Compromise remain in the SOAR system to correlate subsequent alarms.
The SOAR system provides a clear overview of the incident and a basis for subsequent lessons learned thanks to the traceable sequence within the incident response process and the continuous documentation of all steps.
That's why SECUINFRA
- Innovation
The continuous support and further development of the SOAR system by SECUINFRA’s cyber defense experts makes it possible to react to a constantly changing threat landscape.
- Expertise
SECUINFRA can look back on years of experience in developing use cases and analyzing security incidents. The know-how gained flows into every new project.
- Customer orientation
Thanks to SECUINFRA’s many years of experience in consulting, our cyber defense experts can address your needs in a targeted manner.
- Partnerships
As part of our partnerships with leading manufacturers, we have a direct communication channel and can react to changes in a targeted manner.
- Comprehensive
The project does not stop after the SOAR implementation. SECUINFRA can also assist you with analysis and further development on request.
Strategic partners
We maintain our long-standing strategic partnerships primarily with the following companies
Paloalto Networks
and
Swimlane.


More informative blog posts and technical articles!
Here you can get in touch with us!
Contact form end of page
Contact form at the bottom of the page
"*" indicates required fields
Our portfolio
©2024 SECUINFRA GmbH. All rights reserved.









