Centralized Log Management
Centralized Log Management
What centralized log management is all about
Centralized log management involves the process of collecting, storing, analyzing and managing log data from various sources in a centralized platform. It is a very effective way to collect and monitor log data from distributed systems, applications, devices and infrastructures.
This is done by transferring logs from various sources such as servers, network components, applications and security devices to a central location. This allows IT teams to get a comprehensive view of events and activities across their environment.
By introducing central log management, you save time and resources when analyzing distributed log data!
By working with SECUINFRA, ensure that the right log data ends up in the central log management and is available when needed!
The most important FAQ
from the area of centralized log management
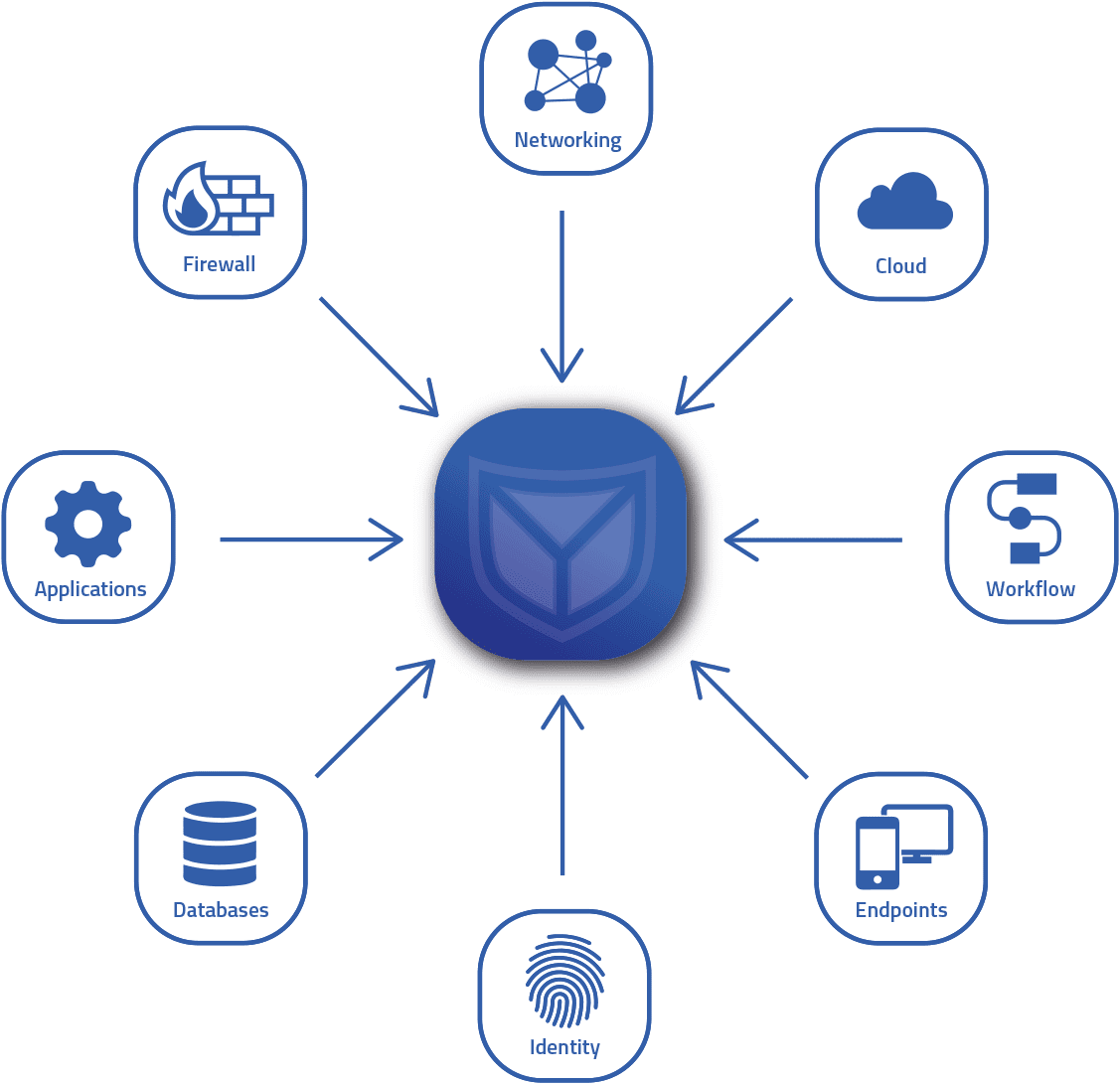
Centralized log management is an approach in which log data from various sources within an organization is collected, stored and analyzed in a single, centralized system. These sources can be different servers, applications, databases or network devices.
Centralized management of log data has several advantages. It improves visibility by providing a unified view of data from different systems. This can make it easier to detect patterns or anomalies that could indicate security threats or performance issues. It can also facilitate compliance by ensuring that all log data is stored in a manner that meets regulatory requirements.
Centralized log management typically also includes capabilities for parsing and indexing logs to improve their searchability, as well as alerting and reporting to draw attention to important events and track trends. It is often used in conjunction with security information and event management (SIEM) systems to improve security monitoring.
There are many tools and services that can be used for centralized log management, including Logstash, Fluentd, Graylog, Splunk, and many cloud-based services.
As a service provider, SECUINFRA will provide you with comprehensive advice on the planning, implementation and use of a log management solution, take over some of the tasks or operate your log management solution as a service for you.
Centralized log management is a process that centralizes the collection and management of log files from various systems within a network. Here are the general steps that this system involves:
- Data collection: the centralized log management system collects log files from various sources. These can include servers, applications, databases, network devices and more.
- Normalization: log data can be in different formats, depending on the system it comes from. A centralized log management system converts this data into a uniform format for more efficient analysis and storage.
- Processing and analysis: The collected log data is analyzed to identify patterns, anomalies or specific events. This analysis can be performed in real-time or retrospectively.
- Storage: The analyzed log data is securely stored in a central database or other storage system.
- Alerting and reporting: based on the analysis, alerts are triggered or reports are generated when specific events or conditions are met. This can help identify potential problems or security breaches early.
- Search and recovery: When needed, such as during a security audit or for troubleshooting, log data can be searched and information quickly recovered.
The exact features and capabilities may vary depending on the specific log management tool or service being used. Common tools include Elasticsearch, Logstash and Kibana (ELK Stack), Splunk, Loggly, and many others.
Centralized log management offers a number of benefits. Here are some of the most important:
- Simplified access and analysis: all logs are in a central location, making it easier to search and analyze data. It’s easier to identify patterns and make connections between different events when all data is in a consistent format and comes from a single source.
- Efficiency: A centralized log management system can automatically collect and analyze logs from multiple sources in real time. This saves time and resources compared to manual methods.
- Security: With centralized log management, you can detect and respond to security incidents faster. You can also conduct forensic investigations and perform audits to meet compliance requirements.
- Troubleshooting: Centralized log management helps identify and resolve problems. You can respond to and minimize downtime faster by identifying and fixing underlying issues.
- Compliance: Many regulations and standards require organizations to retain their logs for a specified period of time. Centralized log management facilitates compliance with these regulations.
- Storage and archiving: Centralized log management enables efficient storage and archiving of logs. This simplifies long-term data storage and allows you to leverage historical data for future analysis.
- Scalability: Centralized log management solutions can typically scale easily to handle large volumes of log data, which is especially important for organizations with growing or varying data volumes.
Setting up a centralized log management system can vary depending on your specific needs and the types of systems you use. However, here are basic steps you can follow:
- Needs assessment: Identify your specific needs and goals for a centralized log management system. This could be system and network performance monitoring, security monitoring, compliance requirements or troubleshooting.
- Selecting the right tools: There are many log management tools on the market, including Splunk, Loggly, Logstash, Graylog and many others. Each has its own strengths and weaknesses and may be better suited for certain use cases. Do your research and choose the tool that best fits your needs.
- Installation and configuration: install your log management tool on a dedicated server or in the cloud, depending on your requirements and preferences. Configure it according to the requirements of your network and systems.
- Set up log sources: You need to configure your systems and applications to send their logs to your centralized log management tool. This may include setting up Syslog on Linux servers, setting up Windows Event Forwarding on Windows servers, or configuring applications to log.
- Configuring dashboards and alerts: Most log management tools provide the ability to create dashboards and configure alerts. You can create dashboards for monitoring system performance, network traffic, security events, etc. You can also configure alerts to notify you when certain events or conditions occur.
- Test and optimize: After you set up your log management system, you should test it thoroughly to make sure it works properly. You should also continue to optimize and customize it over time to meet your specific needs.
Please note that this is only a rough outline and the exact process may vary depending on your specific use case and the tools you choose. It is always a good idea to refer to the specific documentation of your chosen tool. Feel free to contact us directly for further details and consultation. We will clarify any open questions and help you with the rest of the process.
Centralized and decentralized log management are two different approaches to handling and analyzing log data in a system or network. Here are some distinguishing characteristics:
Data storage and access: in a centralized log management system, all log data is stored and managed in a single location or server. This allows for quick, consolidated access to the data, analysis and reporting. In contrast, decentralized log management stores and manages data in multiple locations, usually on the servers or systems that generate the logs.
Security: centralized log management can provide a higher level of security because all data is stored in one location and security measures can be implemented at that central point. With decentralized log management, data can be spread across multiple locations, which can make it difficult to implement consistent security measures.
Maintenance and monitoring: With centralized log management, it is easier to perform consistent maintenance and monitoring because all data is stored in a central location. With decentralized log management, maintenance and monitoring can be more complex because it must be performed across multiple locations.
Scalability: With decentralized log management, scalability can be easier because new log sources can be added without impacting the central storage resource. However, with centralized log management, the addition of new log sources may overload the central resource, potentially requiring expansion of the central storage resource.
Both approaches have their advantages and disadvantages, and the choice between centralized and decentralized log management depends on the specific requirements and conditions of the system or network in question.
That's why SECUINFRA
- Experience
SECUINFRA has focused on the topic of SIEM since 2010. A good Centralized Log Management is the basis for SIEM. In more than 150 successfully implemented SIEM projects, our more than 30 permanently employed SIEM experts have already been able to help numerous customers.
- Data relevance
SECUINFRA supports you in including the right data in your Centralized Log Management. This is the only way to track irregularities in your infrastructure and save costs by avoiding unnecessary data.
- Availability
With our Co-Managed Centralized Log Management, we ensure that your Centralized Log Management is always available. In addition, we ensure that relevant data is available in Centralized Log Management when you need it.
More informative blog posts and technical articles on CLM!
Here you can get in touch with us!
Contact form end of page
Contact form at the bottom of the page
"*" indicates required fields
Our portfolio
©2024 SECUINFRA GmbH. All rights reserved.