Inhalt
According to a 2021 study* by Verizon, about two-thirds of all cyberattacks on companies are due to either hacking or social engineering. Social engineering – the manipulation of employees with the aim of consciously or unconsciously introducing malware into a company – is becoming increasingly popular.
Detecting cyberattacks early and thus being able to defend against them in a timely manner remains challenging for companies – because security events that indicate a cyberattack or compromise often do not stand out from the crowd. Looking for signs that an attack has occurred or is underway can be subtle: a handful of failed login attempts, accessing an application from an unknown Internet address, attempts to connect to restricted corporate resources, or first-time use of tools or processes. Artificial intelligence and machine learning can help by pointing out anomalous activity, but such automation “doesn’t know” whether the anomalous behavior is good or bad – it lacks situational context.
But what approach can organizations use to achieve the elemental goal of detecting cyberattacks on their network in a timely manner and promptly defending against them?
Digression: Why response time should be 0 at best.
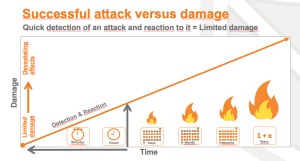
When a cyberattack launches against an enterprise, the time lag between attack detection and attack mitigation is particularly critical. If the time lag is long enough, an attacker can cause massive damage, steal data, encrypt it, destroy systems or even gain admin sovereignty over the entire network.
An organization is better secured the closer the detection and response timings are to zero, see figure.
Real-time event correlation, ideally in conjunction with behavioral analysis, enables very early, if not immediate, detection of cyberattacks.
However, immediate detection of a cyber attack is only one relevant aspect – the fastest possible response to it is the other. This is especially not ensured when attacks occur outside normal working hours or when the security team is flooded with alerts, possibly false alarms.
In addition to drastically reducing false alarms through powerful analysis, automating downstream processes, especially defensive processes, plays a critical role.
How do I detect cyberattacks early?
The most important methods for detecting cyberattacks in a timely manner are real-time correlation of events and analysis of behavioral anomalies.
Real-time correlation analyzes incoming event log data from systems in real time for specific behavioral patterns of known attack tactics. These can either be derived from known threat analysis frameworks (e.g. MITRE ATTACK) (see also MITRE ATTACK TechTalk post), based on the company’s experience, or obtained through an exchange in the community – or a combination of all. Real-Time Correlation can be very performant – but Real-Time Correlation also only detects attack methods and tactics that are basically already known.
Behavioral anomaly analysis observes the behavior of each individual user within the system landscape to then detect deviations and evaluate them for their risk potential. This is referred to as UEBA – User and Entity Behavior Analytics. An alarm is triggered when a certain threshold is exceeded in the risk assessment. This is where artificial intelligence and machine learning find their application.
Only a combination of all three approaches is the basis for effective cybersecurity. In the following, we will talk about the Layered Analytics approach.
Why do I need a Layered analytics approach?
Layered analytics – the combination of correlation, behavioral analysis and threat hunting – helps organizations minimize the impact of a cyberattack. Vigilant organizations with the right tools recognize that today’s threats are not single malicious incidents that appear out of nowhere, but a series of actions that can be detected at each step of the attack chain. Different technologies and techniques are better suited for analyzing, for example, log events, user actions and anomalous traffic.
For example, ArcSight’s Layered Analytics approach brings together these different types of analytics and combines signals generated by potential threats.
Layered Analytics thus maximizes an organization’s ability to detect and respond to an attack by capturing the signs of an attack throughout the attack chain:
- Real-time correlation brings together security events, threat data and log data to better detect threats and minimize false positives.
- Behavioral analytics and machine learning capabilities detect user and device behavior that deviates from expected normal activity.
- The Big Data analytics and search capabilities support comprehensive threat hunting and incident response activities.
By combining the approaches and how they work together, organizations gain faster, actionable insights with context and are supported in the key challenge of minimizing the time they are exposed to a successful cyberattack. Only by responding promptly and appropriately can high financial losses and reputational damage be prevented.
Conclusion
The key to early detection of complex threats is to recognize signs of attack from as many parts of the attack chain as possible. Unable to rely on a single source of information, the Layered Analytics approach helps organizations correlate the subtle signs of an attack into a single, context-based decision by incorporating the entire lifecycle of threat data.
Real-time correlation enables organizations to leverage known threat details to automate threat detection. User and entity behavior analysis (UEBA) can determine what activities are normal in your organization and what should be considered an anomaly. Threat Hunting gives IT security teams the tools to use current indicators of compromise to incorporate the appropriate historical data into the analysis.
Layered analytics supports the entire threat data lifecycle. In a world of rapidly changing threat landscape, the Layered Analytics approach serves as a force multiplier for your SOC team so they can focus on what really matters: increasing your organization’s cyber resilience.
Would you like a consultation on the Layered Analytics approach? Contact us you via E-mail or phone: +49 30 5557021 11 – we’ll be happy to advise you!