Inhalt
Incident Response Process Models
One of the most widespread models in German-speaking countries is the process model of the Federal Office for Information Security (BSI). The BSI has set up a model that divides the procedure into 6 different phases and thus subdivides it in a very finely granulated manner compared to other models. An alternative to the BSI model is the Casey model, which is widely used in Anglo-Saxon countries. With 12 phases, this model is even more detailed than the BSI model and will be the subject of the next article on the topic of process models.
The BSI Model
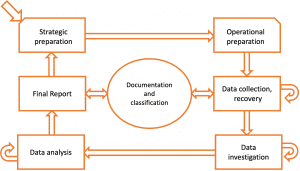
Figure 1 shows the process chain of the BSI model.
The start is the strategic preparation. It is important to note that the third, fourth and fifth phases represent a loop, i.e., these phases can be repeated should they be deemed insufficient by later findings. In addition, documentation must start at the beginning of the third phase and be carried out without gaps until the last phase.
Phase 1: Strategic preparation
The first phase deals with all the preparations that need to be made before a security incident occurs. This includes, for example, preparing software and hardware, such as a workstation or a write blocker. In addition, instructions for communication must be defined. Which department must be involved, when and how, for example, lawyers must be called in.
Phase 2: Operational preparation
Operational preparation is carried out when the incident has occurred. At the beginning, a scope for the investigation is set and the initial suspicion is defined.
Based on this, an inventory of the potential affected systems is made. This procedure ensures that no systems are overlooked in the subsequent data collection and that all sources known at that time are taken into account. In addition, questions regarding data protection must be clarified in this phase.
Phase 3: Data collection, recovery
In phase 3, data collection is carried out according to the specifications made in the operational preparation. Here, a distinction is made between a complete image of all systems and a triage. While the former creates a 1-to-1 image of the systems in order to store all data accurately and not to cover any traces, triage is limited to the rapid collection of data that, in the context of a cyber attack, provides information about the procedure and type of attack. A detailed article on the topic of triage in digital forensics can be found here (Triage in digital forensics).
The order in which data is backed up also plays a major role. Volatile storage such as RAM should always come first in the data backup process. In phase 3, the relevance of the chain of custody also begins. This describes a complete documentation of the whereabouts of the evidence and must be maintained in detail until the investigation is completed. Also, the progress log is started to be written in this phase.
Phase 4: Data investigation
Data investigation is the preliminary stage of the actual analysis. In this phase, the data is to be prepared for the forensic examination. For this purpose, traces are extracted from the collected evidence and, if necessary, transferred to another format. In addition, deleted or corrupt data sets can be restored in this phase. If new data sources are identified in this course, the data collection can be repeated.
Phase 5: Data analysis
The fifth phase now deals with the evaluation of the data obtained and their interpretation. As a rule, this phase attempts to put the data in a chronological and logical order in order to be able to recognize and evaluate correlations. If new data sources are identified or if it is determined that data sets are incomplete, a new data collection can be initiated as in phase 4.
Phase 6: Final Report
The final report is also referred to as the final log. The BSI explicitly distinguishes this from the progress log, which is already started in phase 3 and is part of the chain of evidence. This progress report contains all investigation steps, forensic tools and collected data. With the help of the progress log, the final log for the specified target group can now be written in the sixth phase. It thus contains an overview of the entire forensic process as well as the results collected from the analysis.