Inhalt
Phishing is a form of threat that relies entirely on humans as a “security gap”. Phishing can be used for many purposes and increasingly serves as a door opener for follow-up attacks with malware such as ransomware.
Phishing can again be divided into several subcategories. In the following, we will look at spray-and-pray phishing, man-in-the-middle phishing, spear phishing and dynamite phishing, in addition to the most well-known, as these are the most widespread types used to attack companies.
Spray-and-Pray Phishing
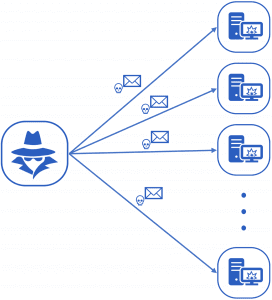
Spray-and-pray phishing works like a large fishing net. Millions of mostly low-quality emails are sent in the hope that a fraction of recipients will respond. Usually, this approach works very well if no specific target is to be attacked. The emails usually contain links to a fake website that provides a registration form. If the victim enters his credentials on this website, they are directly forwarded to the attacker.
Man-in-the-Middle-Phishing
Phishing attacks can also be implemented as man-in-the-middle. This means that the victim is no longer asked to disclose their bank details in the e-mail, but instead the attacker acts as a middleman between the bank and the customer. In doing so, the victim is tricked into installing malware. Alternatively, the attacker tries to get the account data of the e-mail account directly in order to manipulate the communication with the bank afterwards. In this way, an attacker can also bypass modern security systems such as the iTAN procedure. For more information, see the article in our Incident Response Diary.
Spear Phishing
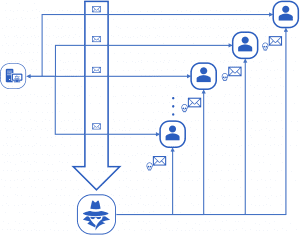
Spear phishing is a type of phishing that is heavily tailored to a target person. First, information about the victim is collected in various ways. These include social networks, data leaks and contact information such as names websites or home address. This information is used in the email to make it look deceptively genuine. However, spear phishing is rarely used to obtain banking information, but is usually part of a more complex operation that aims to infiltrate corporate networks, for example.
Dynamite-Phishing
A big trend in recent years is so-called dynamite phishing.
This type of phishing really became known through the Emotet malware family.
Emotet has a module that spies out all mail conversations on an infected system and forwards them to its own servers. Subsequently, email conversations containing links and file attachments in particular are selected and manipulated in such a way that a Word document is downloaded instead of the desired file, which Emotet can reload. These emails are then reinserted into the conversation. Thus, the malware can spread to other systems.
Protection against phishing
In order to protect one’s own company against phishing, first and foremost awareness must be created among employees. This can be done through workshops, phishing simulation or company policies. A phishing forwarding system that allows employees to forward suspicious e-mails directly to an internal or external analysis department has proven helpful. This department can investigate the emails and provide feedback to the affected employee. Showing a “Report Phishing” button in Outlook will make the employee aware each time they view an email that it could be a phishing email. Furthermore, it is important to train employees to check the sender of every email and never enter personal or company information lightly.
Would you like expert advice for your company? Then get in touch with us!