Inhalt
A customer approached us because he had received fake invoices by email. What initially sounds like simple phishing turned out to be more extensive than initially assumed.
The analysis
After we acquired the e-mails and images of the affected computers, the analysis was initiated and it was determined that the attacker was not only sending fake emails to the victim, but also had access to the victim’s e-mail account.
This access was therefore advantageous for the attacker, as he was able to forward all of the victim’s emails to himself and thus also came into possession of legitimate invoices. These invoices were then manipulated to get the victim to transfer money to the attacker’s accounts. To do this, the manipulated invoices were sent to the victim using a fake email address that was similar to the original biller. To avoid noticing that invoices were arriving twice, rules were set up in Outlook that would send all emails from the original biller to the attacker first and then delete them from the victim’s email account. In addition to the incoming emails from the biller, all outgoing emails to the biller were also deleted so that if a request was made to the spoofed email address, it would not be noticed that the email address was unreachable.
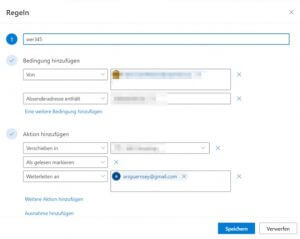
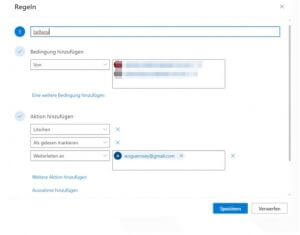
As can be seen in the images below, the rules were named “wer345” and “bellwoy” and in each case the emails were forwarded to the attacker’s address “arsguernsey@gmail[.]com”.
Since the attacker had access to the account, the inquiries were nevertheless answered not by the original biller, but by the attacker. The victim could only recognize this fraud by the ending of the e-mail address of the supposed business partner. Here, the “com” was replaced by a “corn”.
It was only due to the good attention of the victim that no major damage was caused.
After we completed the analysis, we were able to determine where the attacker had logged into the account from and what the real email address behind the attacker was.
As always, the same applies in this case: read sender addresses carefully!
IOC
Attacker email address: arsguernsey@gmail[.]com