Inhalt
Such remote access solutions are introduced, for example, for network access of partner companies or in times of the COVID19 pandemic for employees in home offices. Unfortunately, maintenance of these network devices is neglected in some cases, which means that security vulnerabilities in these products are not closed. For example, so-called “remote code execution” (RCE) vulnerabilities are particularly critical. Exploitation of these can grant the attacker direct system access and subsequently enable propagation in the corporate network. This approach has been used for some time by ransomware groups, among others, and has enormous damage potential.
The scale of the problem is enormous
In recent weeks, the SECUINFRA Falcon Team (DFIR – Digital Forensics/Incident Response Team) has managed various IT security incidents at companies with SonicWall appliances. These incidents were triggered by appliances that had not received any firmware updates for a long time.
Since 2019, over 60 vulnerabilities have been found in SonicWall products, a detailed overview can be found here.
An overview of the numerous uses of obsolete SonicWall appliances in Germany, and thus the enormous scale of the problem, can be found in the chart below.
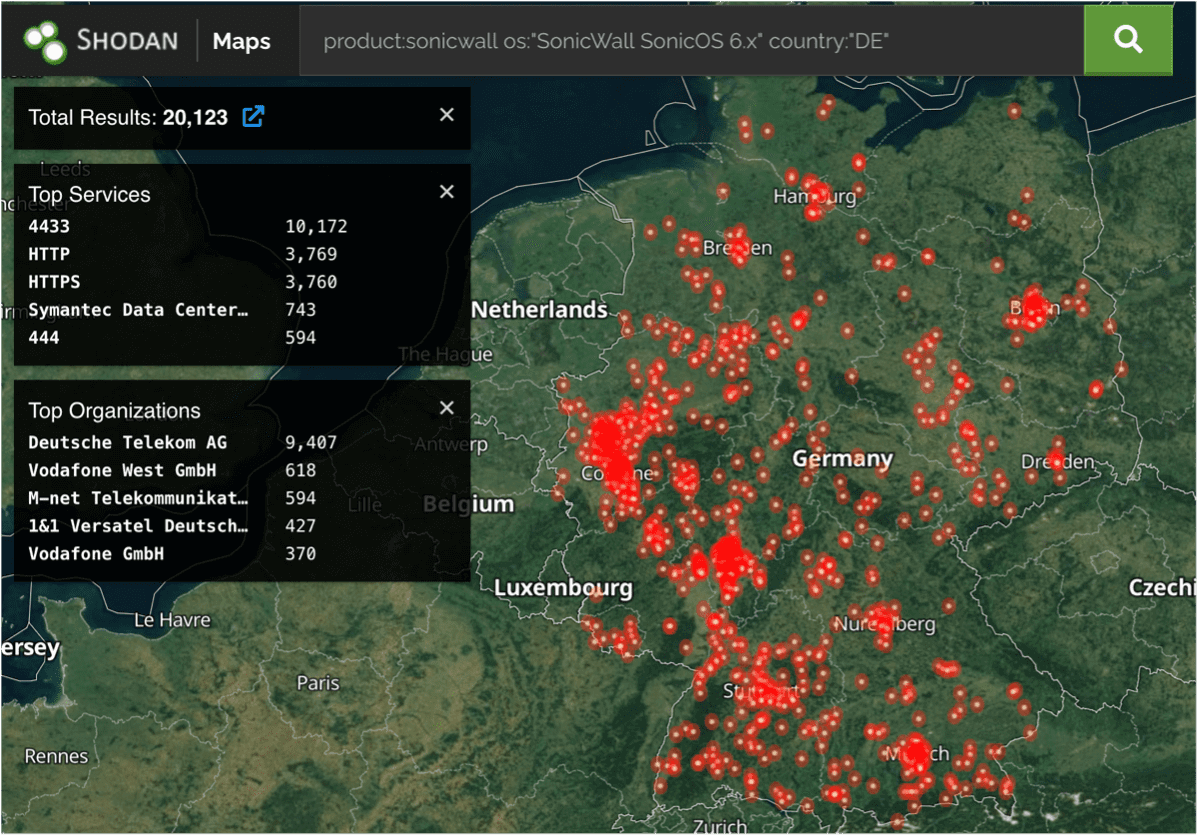
SECUINFRA Incident Response Procedure
In handling each incident, we first obtained an overview of the situation to identify critical systems. Log data from firewalls and critical computer systems were reviewed for previous unauthorized access.
To rule out or, if necessary, address a compromise of the enterprise infrastructure, we applied our Compromise Assessment Service. This involved analyzing forensic artifacts on the customer’s client and server systems using static rule sets and incorporating current threat intelligence data, each tailored to the incident. For one of our customers, the assessment included their OT (Operational Technology) environment, which had process control technology and associated control systems with outdated operating systems. Combined with the appliance’s non-updated firmware, this allowed an attacker to move even more easily across the enterprise network. Fortunately, the compromise was quickly detected and the attacker was driven off the network before they could take over the OT environment and thus impact our customer’s production.
Current threats to other products
As of mid-December 2022, two new security vulnerabilities are also now threatening enterprise networks worldwide:
- CVE-2022-42475 in Fortinet products (Manufacturer notification) and
- CVE-2022-27518 in Citrix ADC and Gateway systems (Manufacturer notification).
Both vulnerabilities are currently being actively exploited, in part by Advanced Persistent Threats, as BleepingComputer and NSA report.
To efficiently prevent such security incidents, we recommend the following measures:
- Keep the software of network and computer systems up-to-date. Check with the product manufacturer or reputable news sources about current security vulnerabilities and corresponding updates.
- Use complex credentials and multi-factor authentication. Remove unused accounts.
- Tie network security systems to a log management platform to facilitate alerting and analysis.
- In the event of a (suspected) compromise: Isolate the appliance from both the Internet and the internal corporate network. Ensure there is no active third-party access through a forensic investigation, such as our Compromise Assessment. Change all assigned credentials and certificates. Check the configuration (e.g., of the firewall) for manipulations.
Do you have questions or need our support? Contact us by phone at +49 30 5557021 11 or online – we are happy to help!










