Inhalt
Your company already uses intrusion detection systems, strong vulnerability management and conducts regular penetration tests? Do you additionally secure your data with conventional IT security measures such as firewalls, antivirus and endpoint protection and are you sure that these protective measures effectively protect your data from cybercriminals? Unfortunately, this is not the case. That’s because attackers are increasingly relying on sophisticated tools and techniques to carry out Advanced Persistent Threats, for example. This type of attack can rarely be detected promptly – and is therefore particularly dangerous. Because if industrial espionage is involved and intellectual properties fall into the wrong hands, the entire company’s existence is threatened.
But what can you do to promptly uncover existing compromises in your network and thus avert massive financial damage and reputational risks to your company? A Compromise Assessment (CA) provides an effective investigative method to reveal hidden attack activity on your network. Learn more about what a Compromise Assessment is and when it is appropriate to use it in the following FAQs.
What is Compromise Assessment?
A Compromise Assessment is a discipline used to identify compromised systems and derive appropriate actions based on the evidence. It is an evaluative, manual and passive discipline. This means that systems must be scanned and assessed and the scanner used does not intervene to take active action against identified potentially critical events.
Various sources (files, the Windows Registry, SHIMCache, Amcache, running processes, event logs, etc.) on a system are consulted and checked against a database of IOCs (Indicators of Compromise). If there are hits, the scanner used generates a corresponding event and the analyst must evaluate this and decide whether or not action is required. This is done with a forensic meticulousness and it is possible to take not only a snapshot but also a historical view of the infrastructure.
What are the use cases for a Compromise Assessment?
There are three relevant use cases for companies to conduct a Compromise Assessment:
- Current security incident
A Compromise Assessment can be used in a security incident that is currently in progress to specify and thus also accelerate the analyses and subsequent recovery.
- Proactive
A Compromise Assessment can also be performed proactively – without the existence of a specific security incident. The results provide information and certainty as to whether attackers are already present in the infrastructure and have left corresponding traces, or whether the installed security measures are working as intended.
- Audit and mergers
Last but not least, a Compromise Assessment is often used as a measure to prepare for an audit; the results serve as evidence for the auditor. In the case of corporate mergers, this discipline can also be used to avoid unwanted surprises from dormant ransomware or Trojans when the networks merge, triggering unexpected security incidents.
Where does Compromise Assessment fit in as a discipline?
Within the world of security disciplines, Compromise Assessment, as an evaluative discipline, can be classified in the Risk Assessment domain, not in the Detection and Response domain. It is therefore unsuitable as a detection service, since the manual execution and analysis can sometimes result in a longer Meantime to Detect (MTD) and Meantime to Respond (MTR) compared to EDR (Endpoint Detection and Response) or SIEM solutions. However, the depth of analysis is significantly greater and APT (Advanced Persistent Threats) can therefore sometimes be detected and stopped.
The technical classification of Compromise Assessment
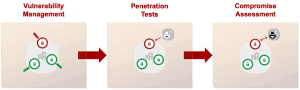
Compromise Assessment is technically specialized in searching for traces of attacks (IOCs) and vulnerabilities. Thus, a comparison can be made with vulnerability management and penetration testing. The following graphic describes this in more detail.
It becomes clear that vulnerability management shows whether there are vulnerabilities in the infrastructure. Penetration tests show whether these are exploitable and a Compromise Assessment shows whether they have already been exploited.
What are the different types of Compromise Assessments?
Ad-Hoc Compromise Assessment
An Ad-Hoc Compromise Assessment is performed when there is a specific IR case or the customer requests an assessment of the system landscape for the purpose of a merger or general review. It is a snapshot that provides clarity on the situation within the system landscape from the time of the scan, sometimes going back to the installation date of the system.
Continuous Compromise Assessment
A Continuous Compromise Assessment picks up the results from an Ad-Hoc Compromise Assessment and is then provided and offered as a service. This is not a detection and response service, but rather a regular review of the infrastructure and assessment of the current security situation, always in relation to traces of attacks. By regularly checking the system landscape, it is possible to increase cyber resilience and to detect and combat attacks much more quickly, because there is no time lag between the individual checks. This means that major damage can be avoided if necessary.
The following example illustrates the strategic advantage of a Continuous Compromise Assessment:
A company decides to conduct an Ad-Hoc Compromise Assessment, the snapshot shows traces of an attack that should have been detected by existing security measures. However, because the detection options did not take effect, the incident has now gone undetected for a very long time. As a result, appropriate measures are taken in the DFIR (Digital Forensics & Incident Response) area and the incident is resolved. The company then decides to conduct a Compromise Assessment once a year. Within this one year, another incident occurs, which was also not detected by the installed measures. Thus, the security incident is not discovered until almost a year later. This time span could have been significantly reduced by a Continuous Compromise Assessment – as well as the damage caused to the company by the security incident. Why would this be the case?
In a Continuous Compromise Assessment, all systems are regularly scanned and analyzed using the moving-window principle. This approach ideally reduces the time to detection to a few days. This spreads the analysis effort over time and results in a very efficient service discipline that helps to strengthen the company’s cyber resilience in the long term. However, other models such as quarterly or semi-annual assessments are also conceivable, but the disadvantages are obvious.
How does a Compromise Assessment at SECUINFRA work?
In the following, the process of Compromise Assessments at SECUINFRA is described and explained in more detail.
Ad-hoc Compromise Assessments are always scheduled for 3 months by our Cyber Defense Consultants. This is due to the license period of 90 days for management systems and 30 days of pure scanning time. Specifically, the tasks break down as follows:
1st month:
- Roll-out of the agent and setup of the tools
- Testing for functionality of the entire architecture
- start of first scans, if applicable
2nd month:
- Continuation of scans
- In case of errors, go into remediation
- if necessary, start analyses
3. month:
- Continue and complete analyses
- Presentation of the results
- Preparation of the final report
In a Continuous Compromise Assessment, the process is different. Here, scans are started after the roll-out and the results are analyzed according to the “moving window principle”. At the end of each month, an interim report is created, which provides information about the previous month. If the customer has any questions, a meeting with the responsible SECUINFRA expert team is set up and the corresponding cases are discussed within this framework. The duration of such a Compromise Assessment is always 12 months, accordingly licenses are required.
In both types, a Compromise Assessment comprises the following four phases:
- Rollout
- Scan
- Analysis
- Report
- In the rollout phase, discussions are held on how many systems are under consideration and which software configurations will be used in the company. Checklists have been prepared for this purpose, which are used by the customer to check progress, as well as information sheets to obtain contact persons or contact details. Then the agents for the service are rolled out in the infrastructure and the management software is configured.
- The process of the scan phase depends on the selected service package. The first scan is always a baseline scan, regardless of the selected service package, to get an overview of the current security and risk situation. If Continuous Compromise Assessment has been selected as the service package, the systems under consideration are permanently scanned and analyzed according to the “moving window principle”. This means that the oldest events are given priority and evaluated. The exception here are events with a particularly high severity level or those that can be directly regarded as a security incident or assigned to one.
- In the analysis phase, SECUINFRA Cyber Defense experts examine the scan results and identify compromised IT systems. The events are described, evaluated and provided with clear recommendations for action. In case of particularly critical results, the end customer is informed immediately.
- Report: After each scan, the end customer receives a detailed report of all results, detailed descriptions, assessments and, if necessary, clear recommendations for action. The report is discussed with the end customer at the end of the process.
SECUINFRA’s Compromise Assessment can be complemented by measures in the area of Digital Forensics and Incident Response or Remediation Support to improve the company’s cyber resilience.
Conclusion
The most dangerous thing about cyber attacks is too much time passing before the attacks are detected. The more time that passes, the longer the attacker has to move around the network, spy on data and take advantage of it. Particularly professionally executed Advanced Persistent Threats can, in the worst case, remain in the systems of the affected companies for months or years – and during this time, secret data falls into unauthorized hands or is used for spying. So critical to network security is early identification of these activities. With a Compromise Assessment, a method is available that detects the smallest artifacts of attacks and thus makes timely defense possible. The particular precision of Compromise Assessments in detecting artifacts or IOCs is due to the manual activity of specially trained cyber defense experts who follow up the smallest traces in the networks. It is precisely through regular Continuous Compromise Assessment that companies can close existing security gaps and significantly increase their cyber resilience.