Incident Response
Edge infrastructure, such as internet-exposed firewalls, routers, VPN-Gateways etc. are a common initial access target for cybercrime and espionage actors since these appliances are challenging to defend. According to the vulnerability discovery service LeakIx as many as 30 thousand internet-exposed Cisco devices may already have been compromised...
Today many businesses rely on virtualization technology to run and scale their infrastructure. One of the most popular Hypervisor systems on the market is VMware ESXi, which is regularly targeted in Ransomware attacks for the last 3+ years to increase damage to the victims IT systems.
Evgen Blohm • Yasin Ilgar • 24.01.2023 | Compromise Assessment | Digital Forensics | Incident Response
In order to minimize monetary and reputational damage in the event of a successful IT security attack, immediate and correct response measures, a comprehensive overview of the extent of the cyber attack, and a full clarification of the incident are indispensable.
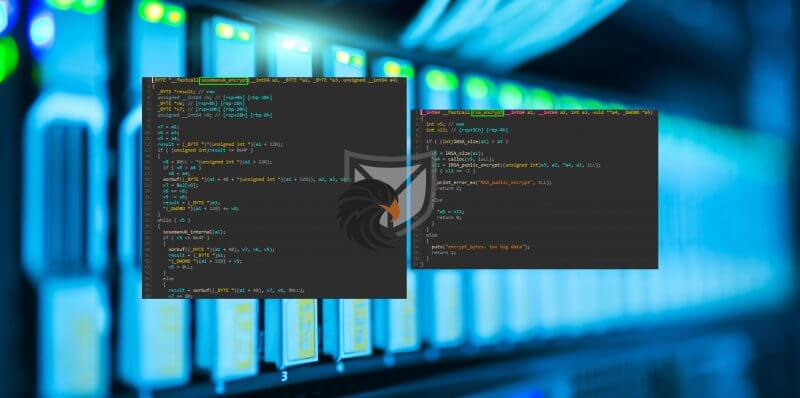
We will first begin at the entry point of this RAT and analyze its executed code before we jump into all possible modules this RAT possesses.
According to Malware Bazaar, samples have been distributed since around mid-January. The final payload is a .NET RAT, which allows the attacker to send commands to the infected system.
This article is intended to provide a deeper insight into the important topic of reporting obligations in the event of an IT security incident.
In order to protect one's own company against phishing, awareness must first and foremost be created among employees. This can be done through workshops, phishing simulation or company policies.
BSI has set up a model that divides the procedure into 6 different phases, which is very finely granulated compared to other models.
In order to shed some light on the subject, we would like to look at a few facts and figures about ransomware as well as a typical course of attack.
That a compromised mailbox is an extremely unpleasant situation is something everyone should be able to imagine. In a recent case we have investigated, attackers have been particularly clever.
Our portfolio
©2024 SECUINFRA GmbH. All rights reserved.